Published: Apr 18, 2025 by Isaac Johnson
Recently the topic came up about scanning containers. I recalled that ACR used to have that feature built in but when I checked the few images I keep in ACR, I found no method to scan.
Today we’ll look up how to setup scans using Microsoft Defender for Cloud and how Defender for Cloud results compare to Open-Source options like HarborCR to scan for CVEs.
We’ll also touch on Docker Scout as a local scan on containers as well as what Harbor Container Registry can provide. I’ll also touch on CVE scores and the future of the CVE program.
Azure Container Registry (ACR)
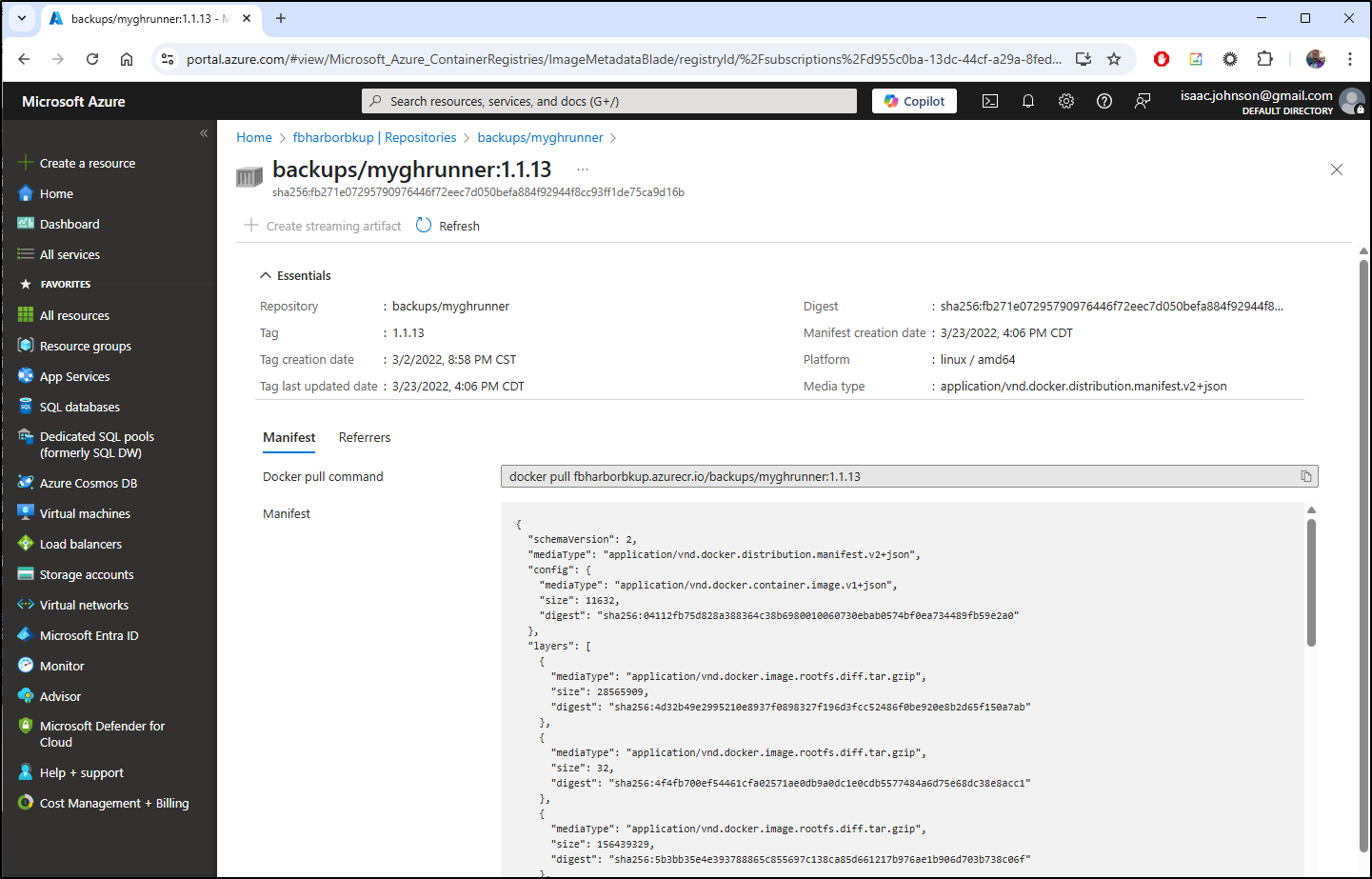
The first step I did was look up an existing Repository (image) in ACR
we can see many details, but not a scan.
I have a memory that it used to be part of ACR at a Premium SKU, but cannot substantiate that.
Today, if we wish to enable security scans on containers, we first need to go to “Microsoft Defender for Cloud”
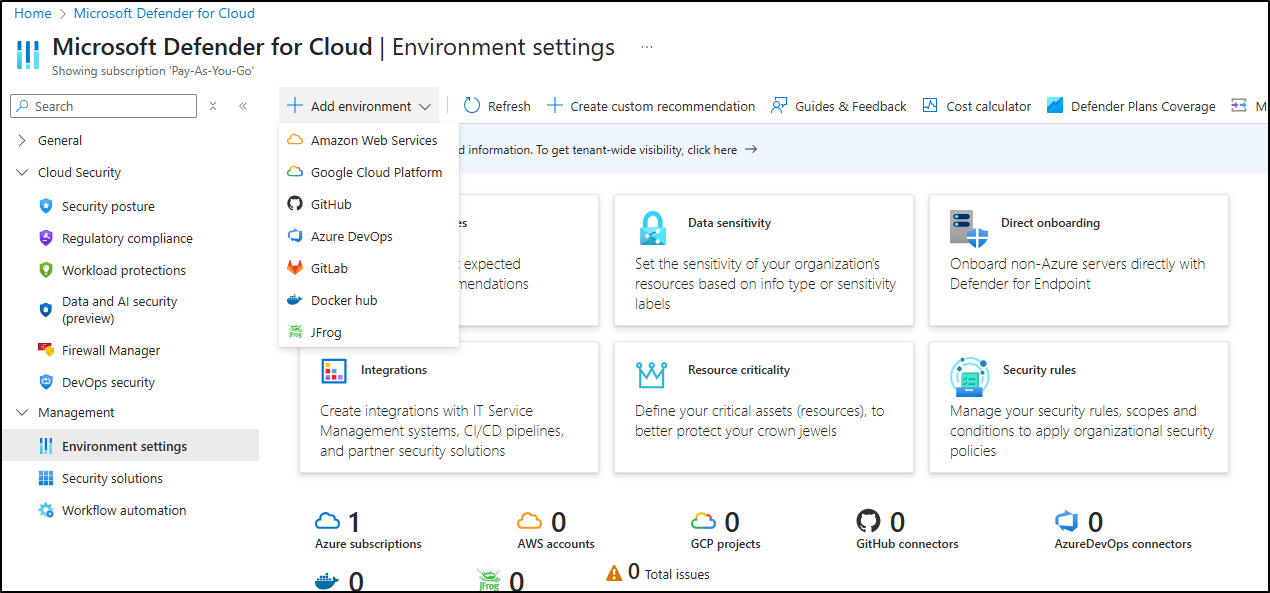
We could do things like add Artifactory or Gitlab or even scan Docker hub
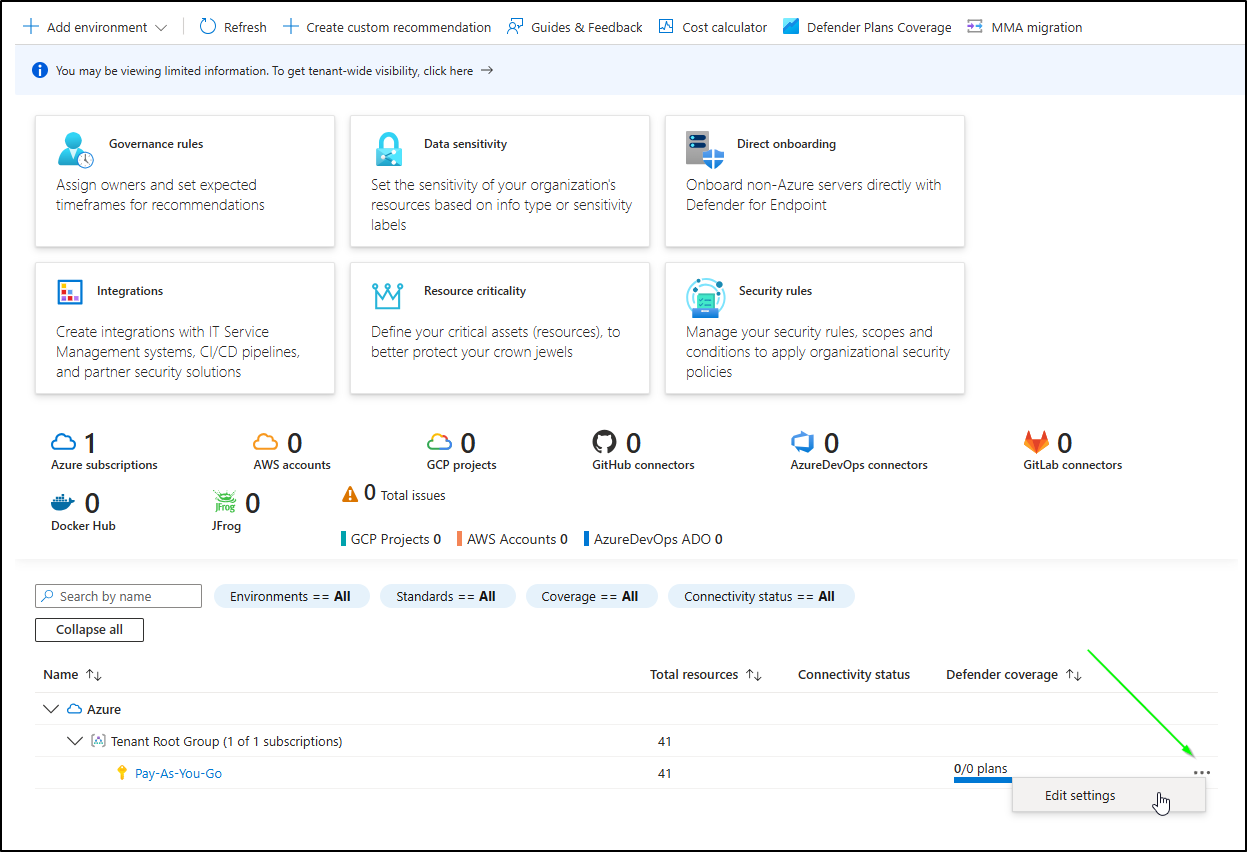
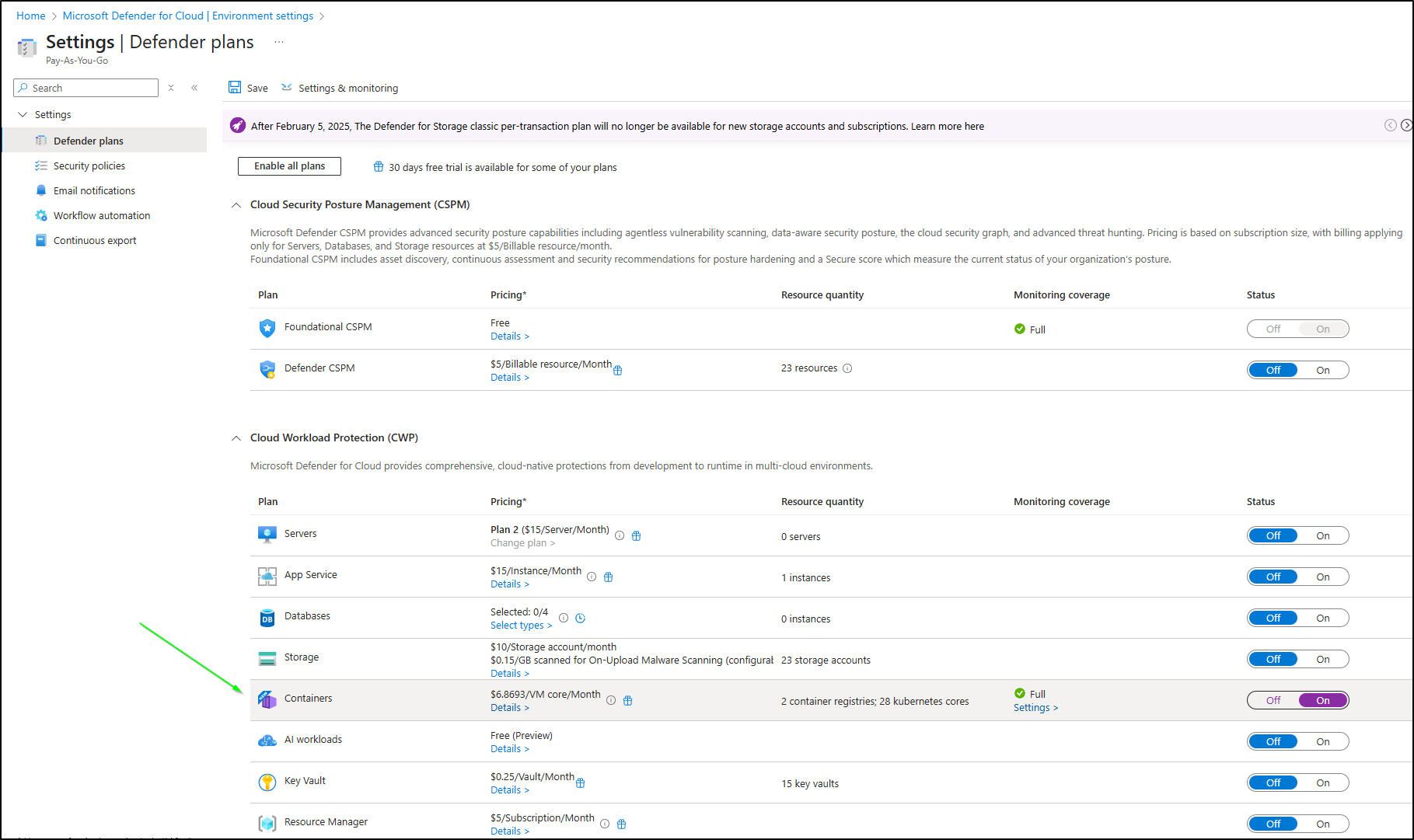
However, what we want to do is add scanning to our ACRs. To do that, we go to the “…” menu on our Subscription and click “Edit Settings”. In my case, this is my “Pay-As-You-Go” subscription
I can now enable “Containers” scanning
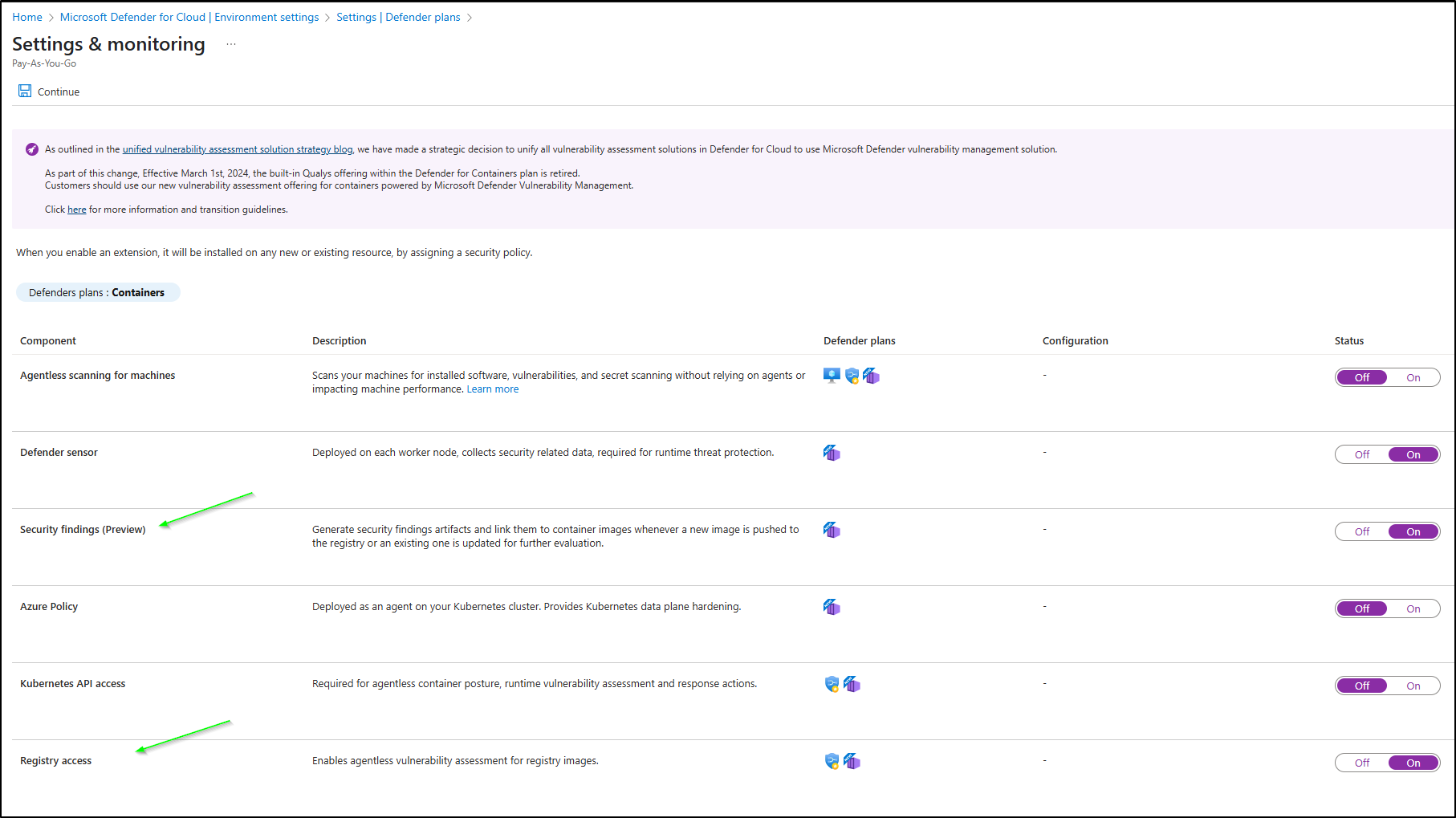
By default, that is “full”, so lets go to the settings to be a bit more specific.
I believe I just need Security Findings and Registry Access to get scans going on my ACR images
Note: Don’t forget to save to make your changes go live
Once I did, I could see scans taking place
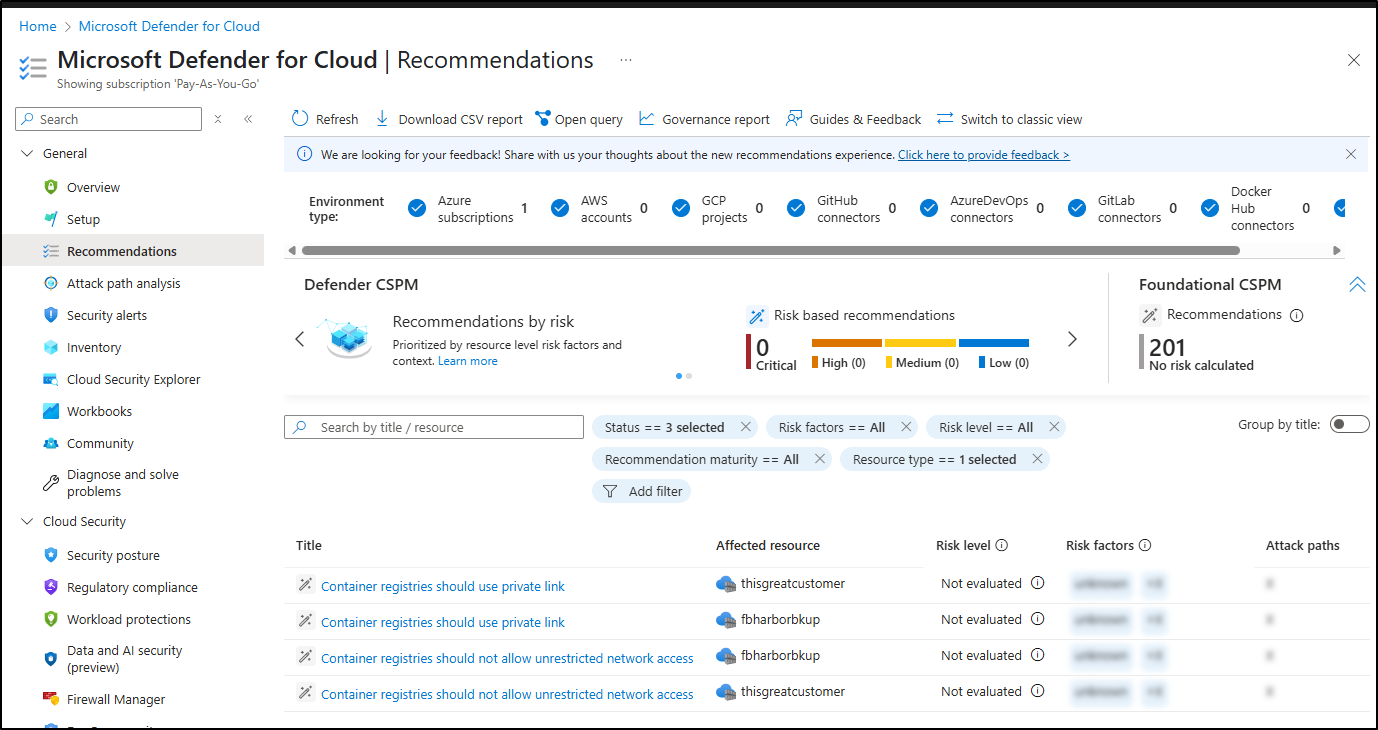
However, rather than showing me a good detailed scan, I instead saw that “Defender for Cloud” just gave me some bland recommendation for my container registry not my actual repositories.
I also followed this guide which suggested I look in the Recommendations section for Defender, but it too showed nothing related to my images
Perhaps it kicks in just on new images. I tried tagging and pushing a weather app I built a while back
$ docker tag myweather:latest thisgreatcustomer.azurecr.io/myweather:latest
$ docker push thisgreatcustomer.azurecr.io/myweather:latest
The push refers to repository [thisgreatcustomer.azurecr.io/myweather]
3e15e997561e: Pushed
acd48962d9cd: Pushed
78086c89b5cd: Pushed
4490b217aedd: Pushed
a606fad1d28b: Pushed
bf83ef464e6d: Pushed
05783ac4ef3c: Pushed
926b35a05f1d: Pushed
d4fc045c9e3a: Pushed
latest: digest: sha256:7b5c4566c830de7546c0ba2cfccd5d7fa95c8447df12019efb4fe261995adaec size: 2204
Alas, yet again I saw scan details in the image nor tag
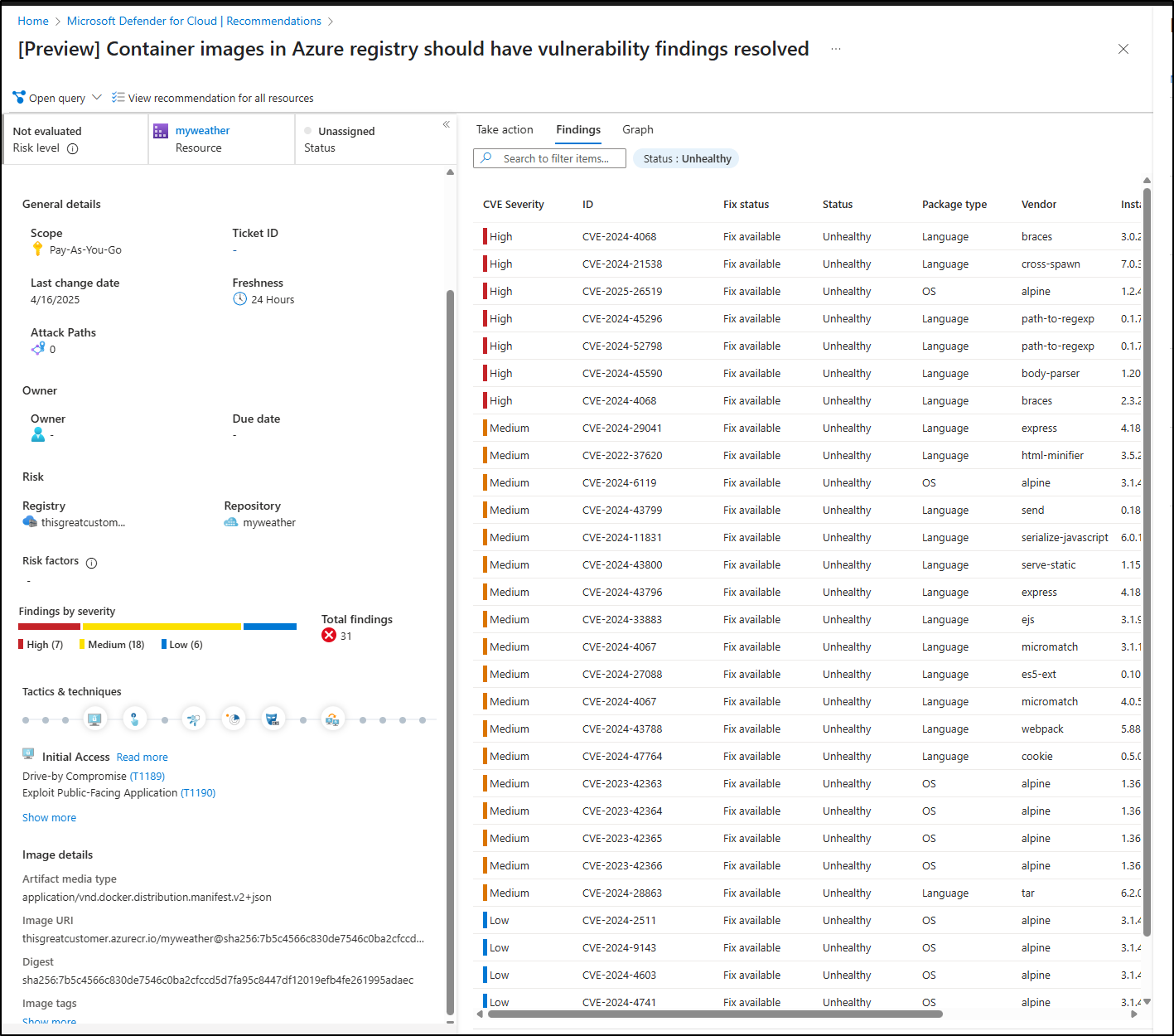
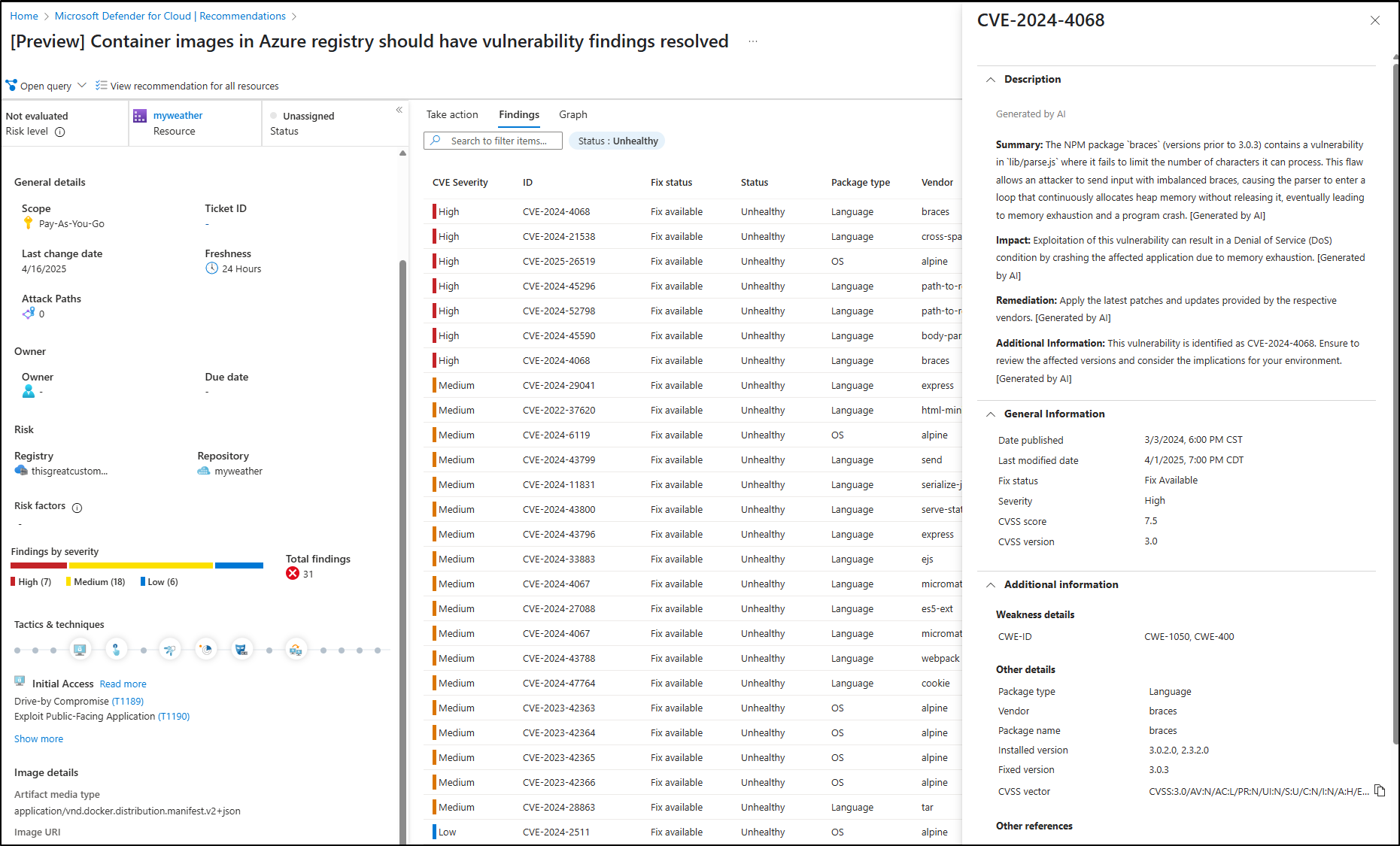
This time, however, I could find results in the Defender for Cloud Recommendations
Selecting a CVE gave me details
There is a “Graph” option, but it seems to be on yet another service tier (and I’m already worried on how this will spike my bill)
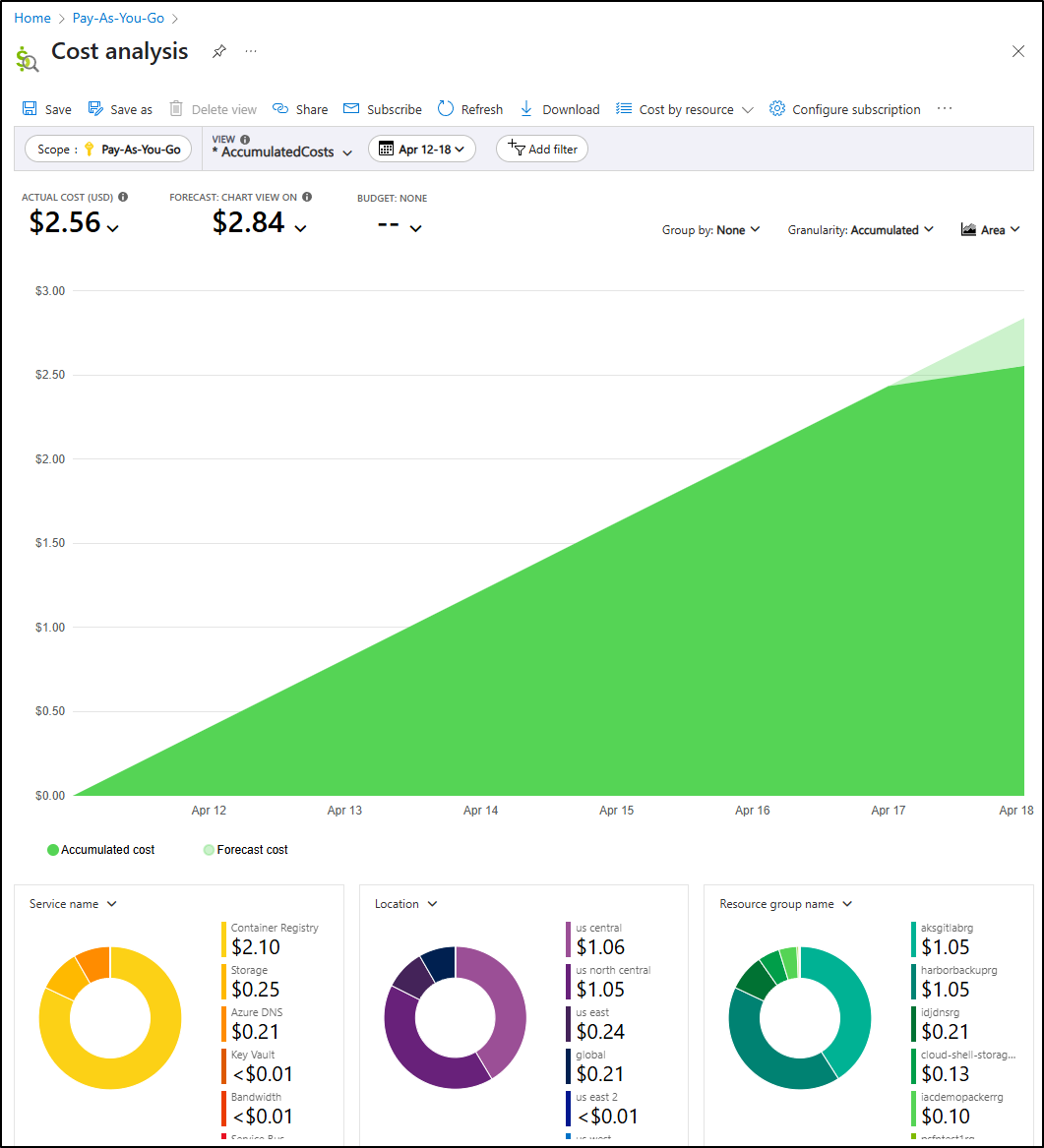
Costs
I did circle back a few days later and can confirm no big jumps in costs
Harbor CR
I found my Harbor CR was down. After digging a bit, the Core Service was out and after rotating some pods and looking at logs, I realized I hosted the underlying DB in PostgreSQL and, of course, used an IPv4 of the master node which a week ago had moved IPs
builder@LuiGi:~/Workspaces/jekyll-blog$ kubectl get cm harbor-registry-core -o yaml | grep .33
POSTGRESQL_HOST: 192.168.1.33
uid: ff89c233-4d74-4edd-80ed-25d5a27664ac
I ended up needing to manually update the CM for core and exporter
$ kubectl edit cm harbor-registry-exporter-env
$ kubectl edit cm harbor-registry-core
and rotate the pods, but once clean
$ kubectl get po -l app=harbor
NAME READY STATUS RESTARTS AGE
harbor-registry-portal-f9d76c856-85k5t 1/1 Running 2 (13d ago) 410d
harbor-registry-redis-0 1/1 Running 2 (13d ago) 410d
harbor-registry-trivy-0 1/1 Running 1 (13d ago) 410d
harbor-registry-registry-74b9f6b76d-l6bz2 2/2 Running 0 158d
harbor-registry-core-7fc8bb68f9-9fcq9 1/1 Running 0 4m25s
harbor-registry-jobservice-57d78975b7-jx2cl 1/1 Running 0 3m33s
harbor-registry-exporter-89f4b7c8b-2bbzz 1/1 Running 0 103s
Harbor CR
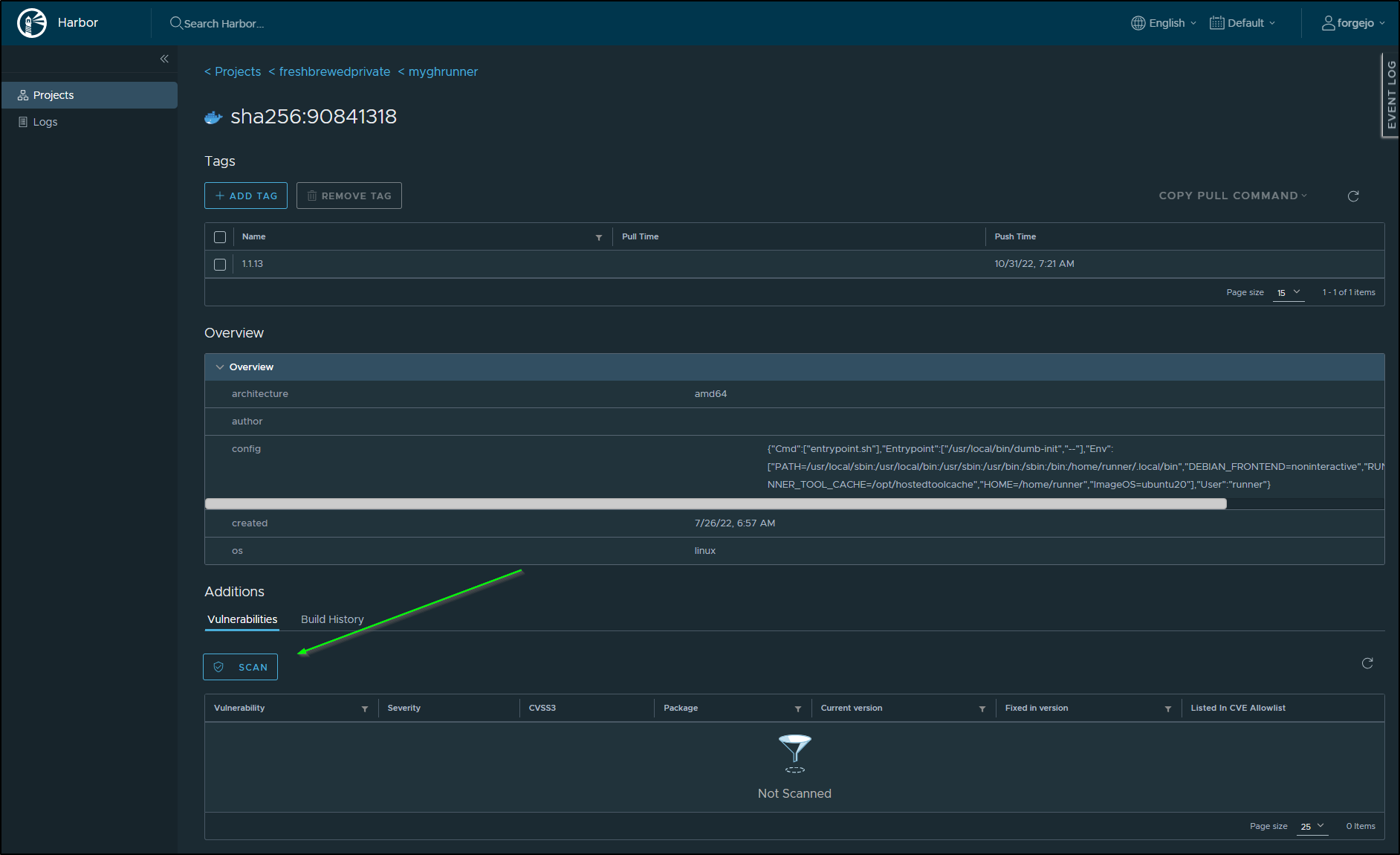
I can now scan, if I had not done so already, a repository
This kicks off a scan
However, I found the private repo was giving errors
2025-04-16T14:46:55Z [INFO] [/pkg/scan/job.go:167]: Report mime types: [application/vnd.security.vulnerability.report; version=1.1]
2025-04-16T14:46:55Z [INFO] [/pkg/scan/job.go:224]: Get report for mime type: application/vnd.security.vulnerability.report; version=1.1
2025-04-16T14:46:57Z [INFO] [/pkg/scan/job.go:245]: Report with mime type application/vnd.security.vulnerability.report; version=1.1 is not ready yet, retry after 5 seconds
2025-04-16T14:47:02Z [INFO] [/pkg/scan/job.go:245]: Report with mime type application/vnd.security.vulnerability.report; version=1.1 is not ready yet, retry after 5 seconds
2025-04-16T14:47:07Z [ERROR] [/pkg/scan/job.go:294]: check scan report with mime type application/vnd.security.vulnerability.report; version=1.1: running trivy wrapper: running trivy: exit status 1: 2025-04-16T14:46:57.963Z [34mINFO[0m Need to update DB
2025-04-16T14:46:57.963Z [34mINFO[0m DB Repository: ghcr.io/aquasecurity/trivy-db
2025-04-16T14:46:57.963Z [34mINFO[0m Downloading DB...
2025-04-16T14:47:04.335Z [34mINFO[0m Vulnerability scanning is enabled
2025-04-16T14:47:04.555Z [31mFATAL[0m image scan error: scan error: unable to initialize a scanner: unable to initialize a docker scanner: 5 errors occurred:
* unable to inspect the image (harbor-registry-core:80/freshbrewedprivate/myghrunner@sha256:90841318bc60e5cc87e8f388da6adb5e458a449c21f9534aec7e8fe59a83ee64): Cannot connect to the Docker daemon at unix:///var/run/docker.sock. Is the docker daemon running?
* containerd socket not found: /run/containerd/containerd.sock
* unable to initialize Podman client: no podman socket found: stat podman/podman.sock: no such file or directory
* GET http://harbor-registry-core:80/v2/freshbrewedprivate/myghrunner/manifests/sha256:90841318bc60e5cc87e8f388da6adb5e458a449c21f9534aec7e8fe59a83ee64: MANIFEST_UNKNOWN: manifest unknown; map[Name:freshbrewedprivate/myghrunner Revision:sha256:90841318bc60e5cc87e8f388da6adb5e458a449c21f9534aec7e8fe59a83ee64]
* GET http://harbor-registry-core:80/v2/freshbrewedprivate/myghrunner/manifests/sha256:90841318bc60e5cc87e8f388da6adb5e458a449c21f9534aec7e8fe59a83ee64: UNAUTHORIZED: unauthorized to access repository: freshbrewedprivate/myghrunner, action: pull: unauthorized to access repository: freshbrewedprivate/myghrunner, action: pull
I still had some issues (even after temporarily making the repo public). I think this might just be a very old possibly corrupted image.
I used the current runner image which is much newer (1 year old) and had no issues scanning (albeit took some time)
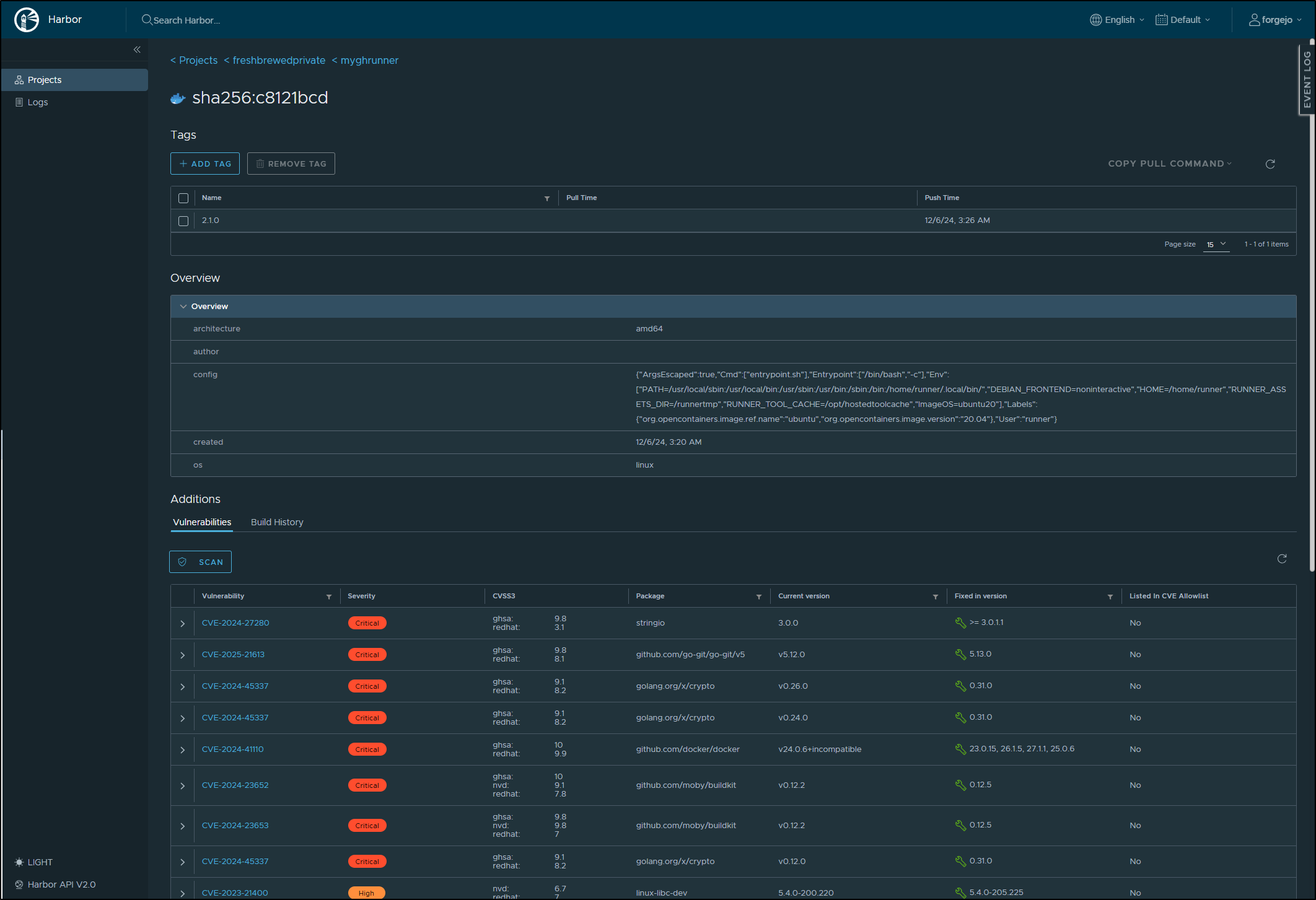
I can now go through the CVEs to see if any are relevant to my use of this container
In most cases, I don’t care as this is a build container, not a running app container.
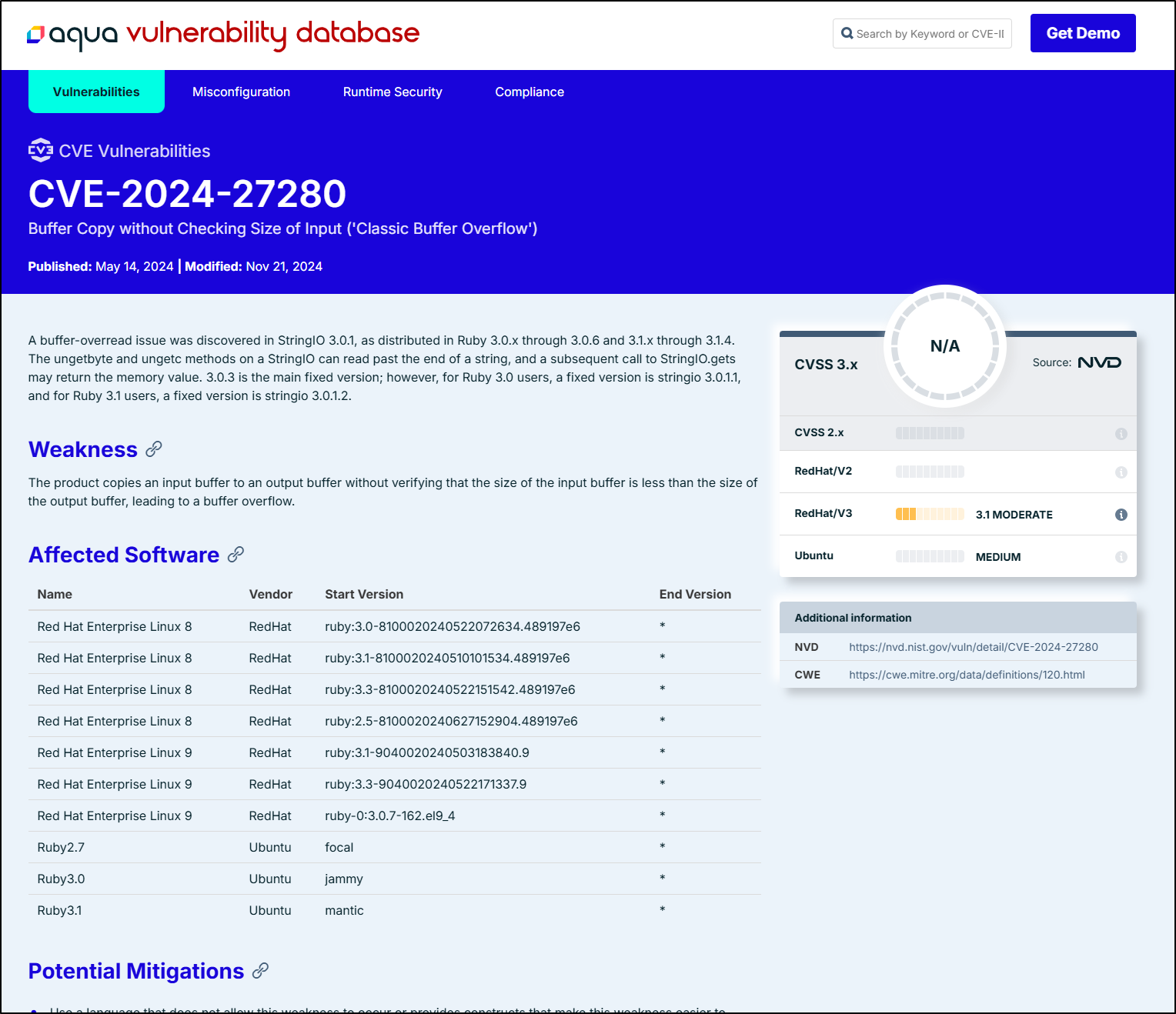
But assuming I did care about, for instance, the first listed CVE-2024-27280.
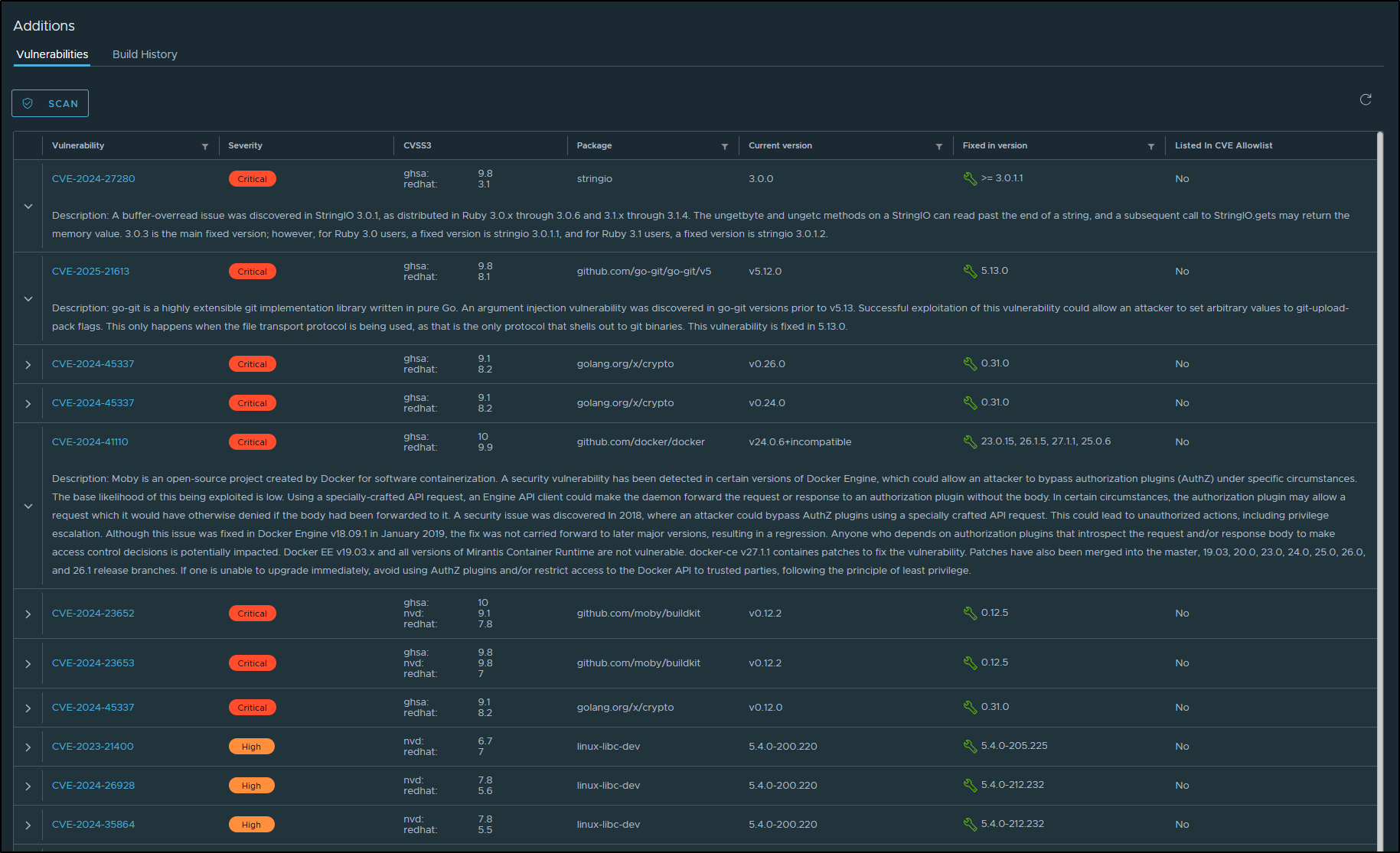
I could click that link and see lots more details:
I can pull up my GHRunnerImage Dockerfile and find the relevant section which pulls Ruby 3.0.0 which has this CVE
RUN curl -fsSL https://github.com/rbenv/rbenv-installer/raw/HEAD/bin/rbenv-installer | bash
RUN cat ~/.bashrc
# Install Ruby 3.0.0
RUN /bin/bash -c "eval ""$(~/.rbenv/bin/rbenv init - --no-rehash bash)"" && rbenv install 3.0.0 && rbenv global 3.0.0"
Looking at the Ruby Releases Page I found the latest 3.0.x would be 3.0.7
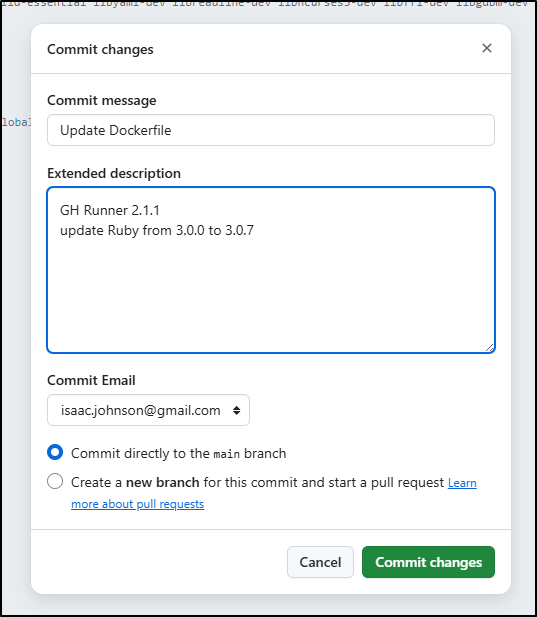
I can update that
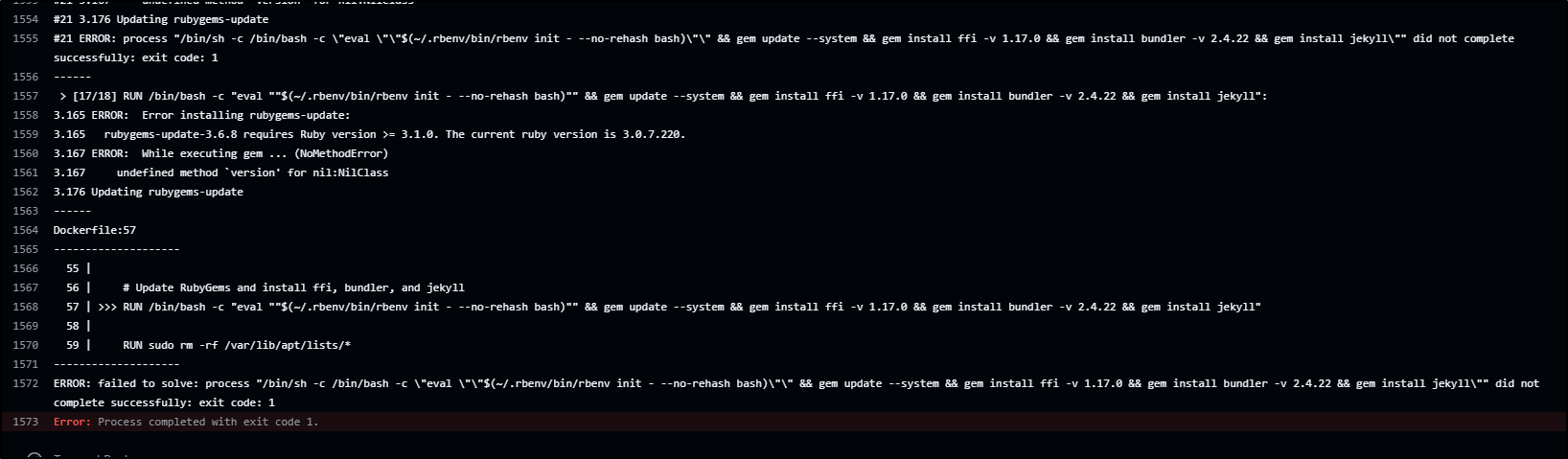
In fact, even that errored prompting me to move to Ruby 3.1.7
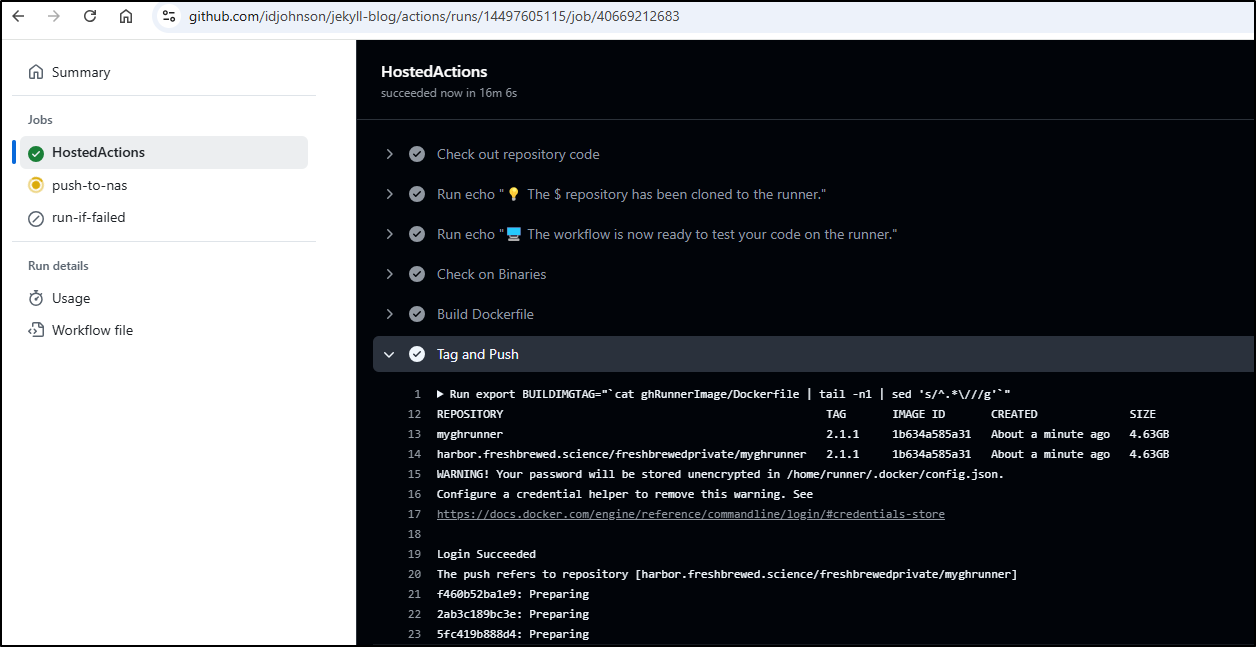
Once that built and pushed
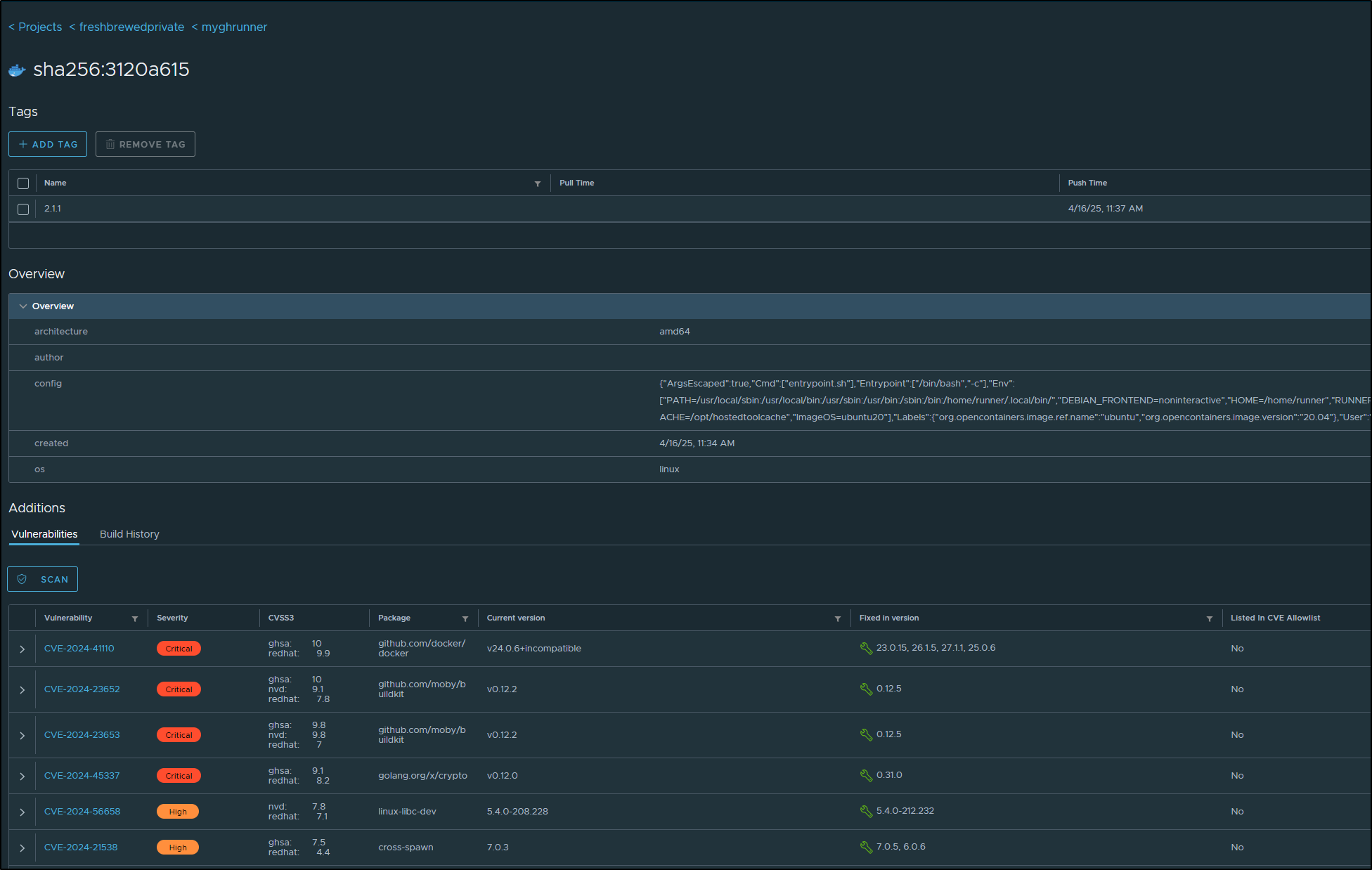
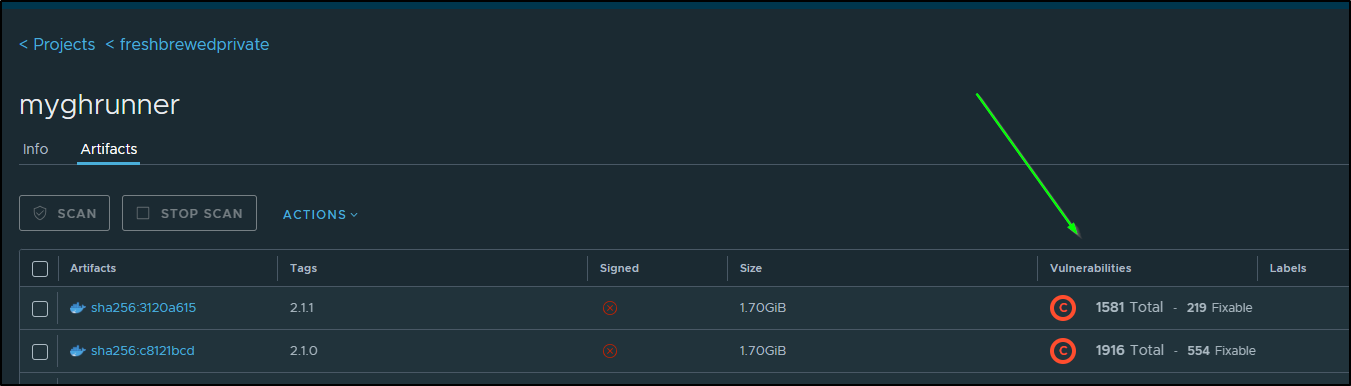
Once the scan completed, I saw we went from 1900+ CVEs in total to 1500+ and from 8 critical to 4
We can also see that on the list of tags page under the Vulnerabilities column
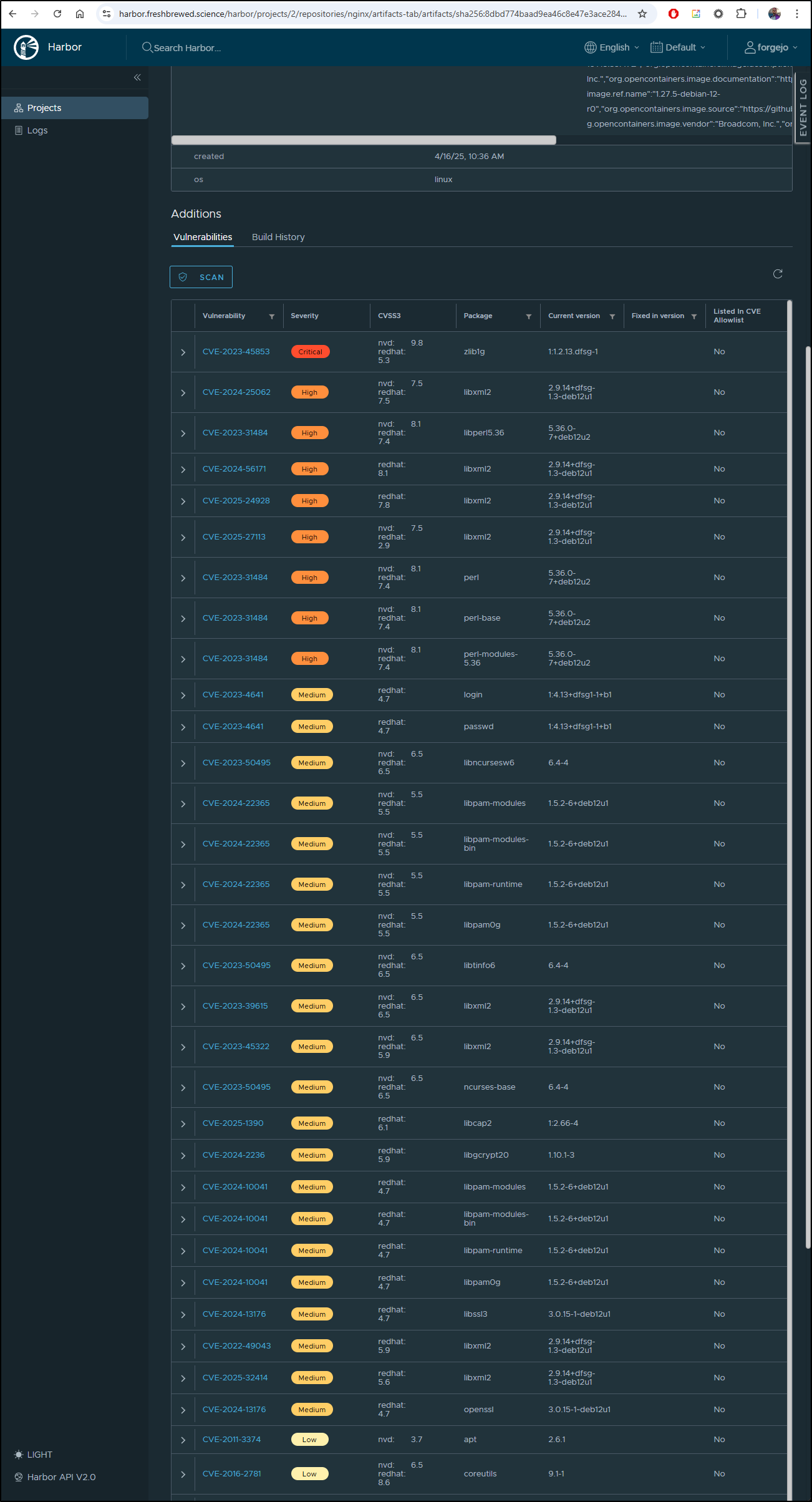
If we look at the Bitnami Nginx latest in more detail
we can see there is 1 Critical, 8 High, 21 Medium and the rest are low.
Docker Scout
If we pull up our latest images
$ docker images | more
REPOSITORY TAG
IMAGE ID CREATED SIZE
bitnami/nginx latest
c6f0f87a612f 32 hours ago 185MB
harbor.freshbrewed.science/freshbrewedprivate/nginx bitnami
c6f0f87a612f 32 hours ago 185MB
trogdor 0.2
fcc2da892a3d 11 days ago 225MB
idjohnson/trogdor latest
fcc2da892a3d 11 days ago 225MB
trogdor 0.1
db0d32ba31fc 11 days ago 225MB
cgr.dev/chainguard/nginx latest
3b2d1b032e20 11 days ago 22MB
harbor.freshbrewed.science/freshbrewedprivate/nginx chainguard
3b2d1b032e20 11 days ago 22MB
eibrahim/fluid-calendar latest
51134afc854d 3 weeks ago 2.49GB
postgres 16-alpine
2875f9e036c2 7 weeks ago 275MB
docker/desktop-kubernetes kubernetes-v1.32.2-cni-v1.6.0-critools-v1.31.1-cri-docke
rd-v0.3.16-1-debian eeef9515fbfb 8 weeks ago 412MB
ghcr.io/remsky/kokoro-fastapi-cpu v0.2.2
f2b9e8a9e998 2 months ago 3.81GB
registry.k8s.io/kube-apiserver v1.32.2
We can see above that c6f0f87a612f represents the same Bitnami Nginx latest image.
I can now ask Docker Scout to investigate it:
$ docker scout cves c6f0f87a612f
i New version 1.17.1 available (installed version is 1.16.3) at https://github.com/docker/scout-cli
✓ Image stored for indexing
✓ Indexed 164 packages
✗ Detected 15 vulnerable packages with a total of 35 vulnerabilities
## Overview
│ Analyzed Image
────────────────────┼──────────────────────────────
Target │ c6f0f87a612f:latest
digest │ c6f0f87a612f
platform │ linux/amd64
vulnerabilities │ 0C 3H 0M 32L
size │ 76 MB
packages │ 164
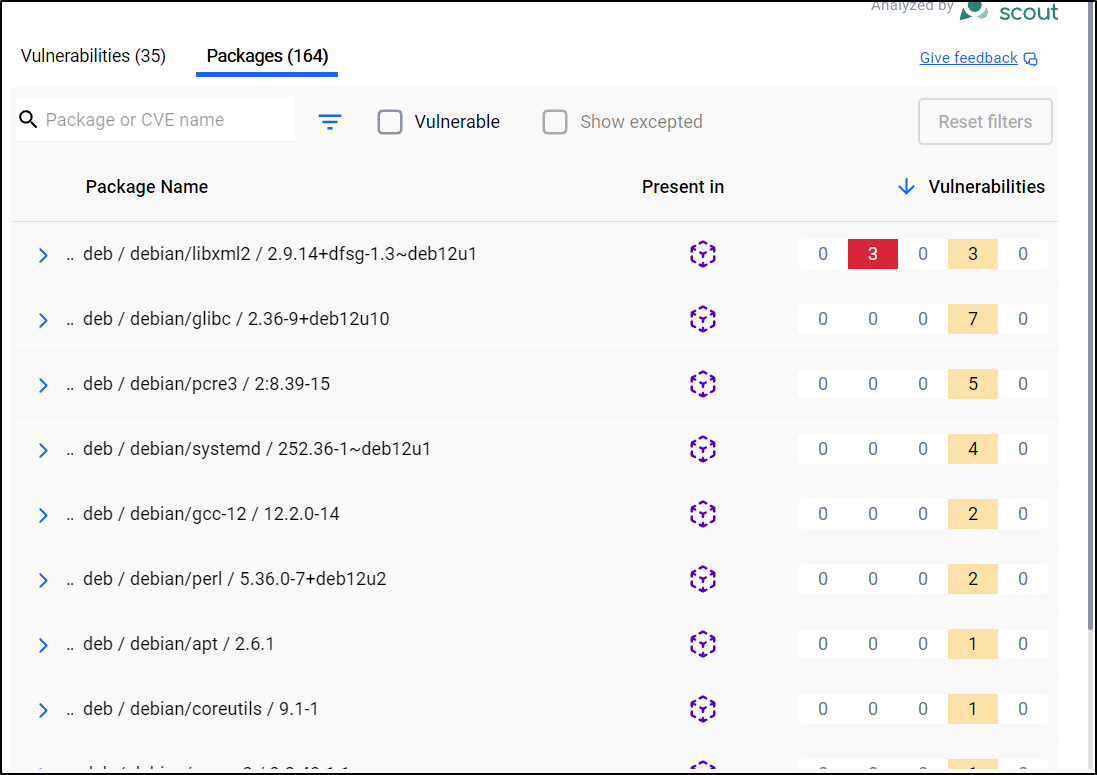
## Packages and Vulnerabilities
0C 3H 0M 3L libxml2 2.9.14+dfsg-1.3~deb12u1
pkg:deb/debian/libxml2@2.9.14%2Bdfsg-1.3~deb12u1?os_distro=bookworm&os_name=debian&os_version=12
✗ HIGH CVE-2022-49043
https://scout.docker.com/v/CVE-2022-49043
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
✗ HIGH CVE-2025-24928
https://scout.docker.com/v/CVE-2025-24928
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
✗ HIGH CVE-2024-56171
https://scout.docker.com/v/CVE-2024-56171
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
✗ LOW CVE-2025-32415
https://scout.docker.com/v/CVE-2025-32415
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
✗ LOW CVE-2025-27113
https://scout.docker.com/v/CVE-2025-27113
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
✗ LOW CVE-2024-34459
https://scout.docker.com/v/CVE-2024-34459
Affected range : >=2.9.14+dfsg-1.3~deb12u1
Fixed version : not fixed
0C 0H 0M 7L glibc 2.36-9+deb12u10
pkg:deb/debian/glibc@2.36-9%2Bdeb12u10?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2019-9192
https://scout.docker.com/v/CVE-2019-9192
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2019-1010025
https://scout.docker.com/v/CVE-2019-1010025
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2019-1010024
https://scout.docker.com/v/CVE-2019-1010024
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2019-1010023
https://scout.docker.com/v/CVE-2019-1010023
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2019-1010022
https://scout.docker.com/v/CVE-2019-1010022
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2018-20796
https://scout.docker.com/v/CVE-2018-20796
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
✗ LOW CVE-2010-4756
https://scout.docker.com/v/CVE-2010-4756
Affected range : >=2.36-9+deb12u10
Fixed version : not fixed
0C 0H 0M 5L pcre3 2:8.39-15
pkg:deb/debian/pcre3@2%3A8.39-15?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2019-20838
https://scout.docker.com/v/CVE-2019-20838
Affected range : >=2:8.39-15
Fixed version : not fixed
✗ LOW CVE-2017-7246
https://scout.docker.com/v/CVE-2017-7246
Affected range : >=2:8.39-15
Fixed version : not fixed
✗ LOW CVE-2017-7245
https://scout.docker.com/v/CVE-2017-7245
Affected range : >=2:8.39-15
Fixed version : not fixed
✗ LOW CVE-2017-16231
https://scout.docker.com/v/CVE-2017-16231
Affected range : >=2:8.39-15
Fixed version : not fixed
✗ LOW CVE-2017-11164
https://scout.docker.com/v/CVE-2017-11164
Affected range : >=2:8.39-15
Fixed version : not fixed
0C 0H 0M 4L systemd 252.36-1~deb12u1
pkg:deb/debian/systemd@252.36-1~deb12u1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2023-31439
https://scout.docker.com/v/CVE-2023-31439
Affected range : >=252.36-1~deb12u1
Fixed version : not fixed
✗ LOW CVE-2023-31438
https://scout.docker.com/v/CVE-2023-31438
Affected range : >=252.36-1~deb12u1
Fixed version : not fixed
✗ LOW CVE-2023-31437
https://scout.docker.com/v/CVE-2023-31437
Affected range : >=252.36-1~deb12u1
Fixed version : not fixed
✗ LOW CVE-2013-4392
https://scout.docker.com/v/CVE-2013-4392
Affected range : >=252.36-1~deb12u1
Fixed version : not fixed
0C 0H 0M 2L gcc-12 12.2.0-14
pkg:deb/debian/gcc-12@12.2.0-14?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2023-4039
https://scout.docker.com/v/CVE-2023-4039
Affected range : >=12.2.0-14
Fixed version : not fixed
✗ LOW CVE-2022-27943
https://scout.docker.com/v/CVE-2022-27943
Affected range : >=12.2.0-14
Fixed version : not fixed
0C 0H 0M 2L perl 5.36.0-7+deb12u2
pkg:deb/debian/perl@5.36.0-7%2Bdeb12u2?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2023-31486
https://scout.docker.com/v/CVE-2023-31486
Affected range : >=5.36.0-7+deb12u1
Fixed version : not fixed
✗ LOW CVE-2011-4116
https://scout.docker.com/v/CVE-2011-4116
Affected range : >=5.36.0-7+deb12u1
Fixed version : not fixed
0C 0H 0M 1L gnupg2 2.2.40-1.1
pkg:deb/debian/gnupg2@2.2.40-1.1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2022-3219
https://scout.docker.com/v/CVE-2022-3219
Affected range : >=2.2.40-1.1
Fixed version : not fixed
0C 0H 0M 1L openssl 3.0.15-1~deb12u1
pkg:deb/debian/openssl@3.0.15-1~deb12u1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2010-0928
https://scout.docker.com/v/CVE-2010-0928
Affected range : >=3.0.11-1~deb12u2
Fixed version : not fixed
0C 0H 0M 1L shadow 1:4.13+dfsg1-1
pkg:deb/debian/shadow@1%3A4.13%2Bdfsg1-1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2007-5686
https://scout.docker.com/v/CVE-2007-5686
Affected range : >=1:4.13+dfsg1-1
Fixed version : not fixed
0C 0H 0M 1L apt 2.6.1
pkg:deb/debian/apt@2.6.1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2011-3374
https://scout.docker.com/v/CVE-2011-3374
Affected range : >=2.6.1
Fixed version : not fixed
0C 0H 0M 1L util-linux 2.38.1-5+deb12u3
pkg:deb/debian/util-linux@2.38.1-5%2Bdeb12u3?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2022-0563
https://scout.docker.com/v/CVE-2022-0563
Affected range : >=2.38.1-5+deb12u3
Fixed version : not fixed
0C 0H 0M 1L gnutls28 3.7.9-2+deb12u4
pkg:deb/debian/gnutls28@3.7.9-2%2Bdeb12u4?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2011-3389
https://scout.docker.com/v/CVE-2011-3389
Affected range : >=3.7.9-2+deb12u4
Fixed version : not fixed
0C 0H 0M 1L coreutils 9.1-1
pkg:deb/debian/coreutils@9.1-1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2017-18018
https://scout.docker.com/v/CVE-2017-18018
Affected range : >=9.1-1
Fixed version : not fixed
0C 0H 0M 1L libgcrypt20 1.10.1-3
pkg:deb/debian/libgcrypt20@1.10.1-3?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2018-6829
https://scout.docker.com/v/CVE-2018-6829
Affected range : >=1.10.1-3
Fixed version : not fixed
0C 0H 0M 1L tar 1.34+dfsg-1.2+deb12u1
pkg:deb/debian/tar@1.34%2Bdfsg-1.2%2Bdeb12u1?os_distro=bookworm&os_name=debian&os_version=12
✗ LOW CVE-2005-2541
https://scout.docker.com/v/CVE-2005-2541
Affected range : >=1.34+dfsg-1.2+deb12u1
Fixed version : not fixed
35 vulnerabilities found in 15 packages
CRITICAL 0
HIGH 3
MEDIUM 0
LOW 32
What's next:
View base image update recommendations → docker scout recommendations c6f0f87a612f:latest
What I find interesting is that it found far less issues than Harbor.
| Tool | Critical | High | Medium | Low |
|---|---|---|---|---|
| Harbor | 1 | 8 | 21 | 74 |
| Docker Scout | 0 | 3 | 0 | 32 |
I thought perhaps it was a subset (and it is), but Scout classifies the severities different.
We can also use the CLI to create Markdown docs (really HTML) of our output to bundle in a build report, for instance
Or use it to find any HIGH vulnerabilities and perhaps put in a build gate to fail if Highs or Critical CVEs are found:
$ docker scout cves c6f0f87a612f --format sarif | jq | grep cvssV3_severity | sort -u | grep "HIGH"
i New version 1.17.1 available (installed version is 1.17.0) at https://github.com/docker/scout-cli
✓ SBOM of image already cached, 164 packages indexed
✗ Detected 15 vulnerable packages with a total of 35 vulnerabilities
What's next:
View base image update recommendations → docker scout recommendations c6f0f87a612f:latest
"cvssV3_severity": "HIGH",
Via Docker Desktop
We don’t just have to use the CLI.
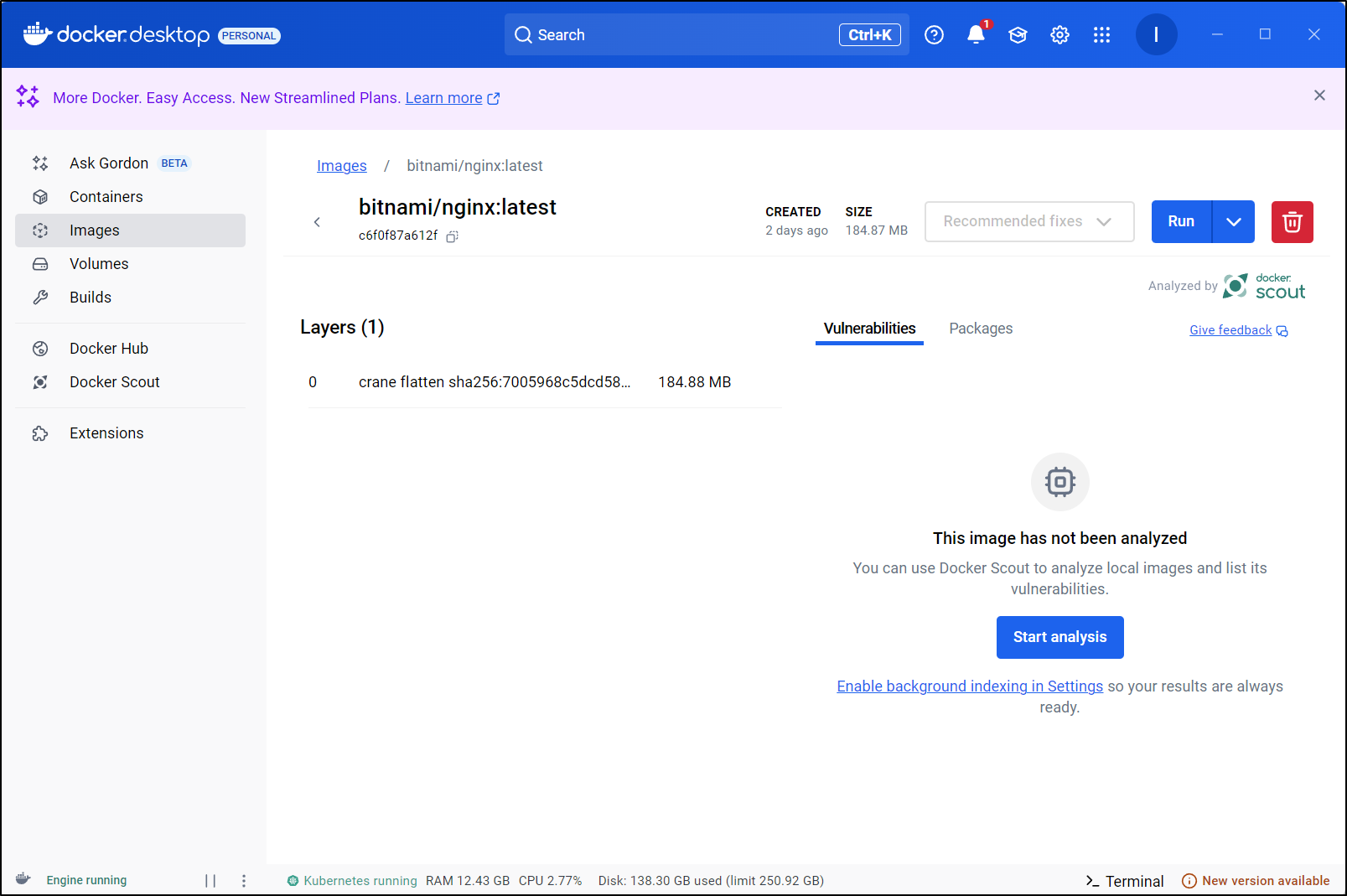
In Docker Desktop, we can pull up an image and click “Start Analysis” in the Vulnerabilities section for the Image
It failed at the Bitnami Nginx (as well as the others I had downloaded)
I tried a dozen more of various sizes and ages and all ended up showing “This image couldn’t be analyzed”
I then realized that a Docker Desktop update was pending and that can sometimes hold things up.
I updated to the latest (as of this writing) 4.40.0 and tried again - this time it worked:
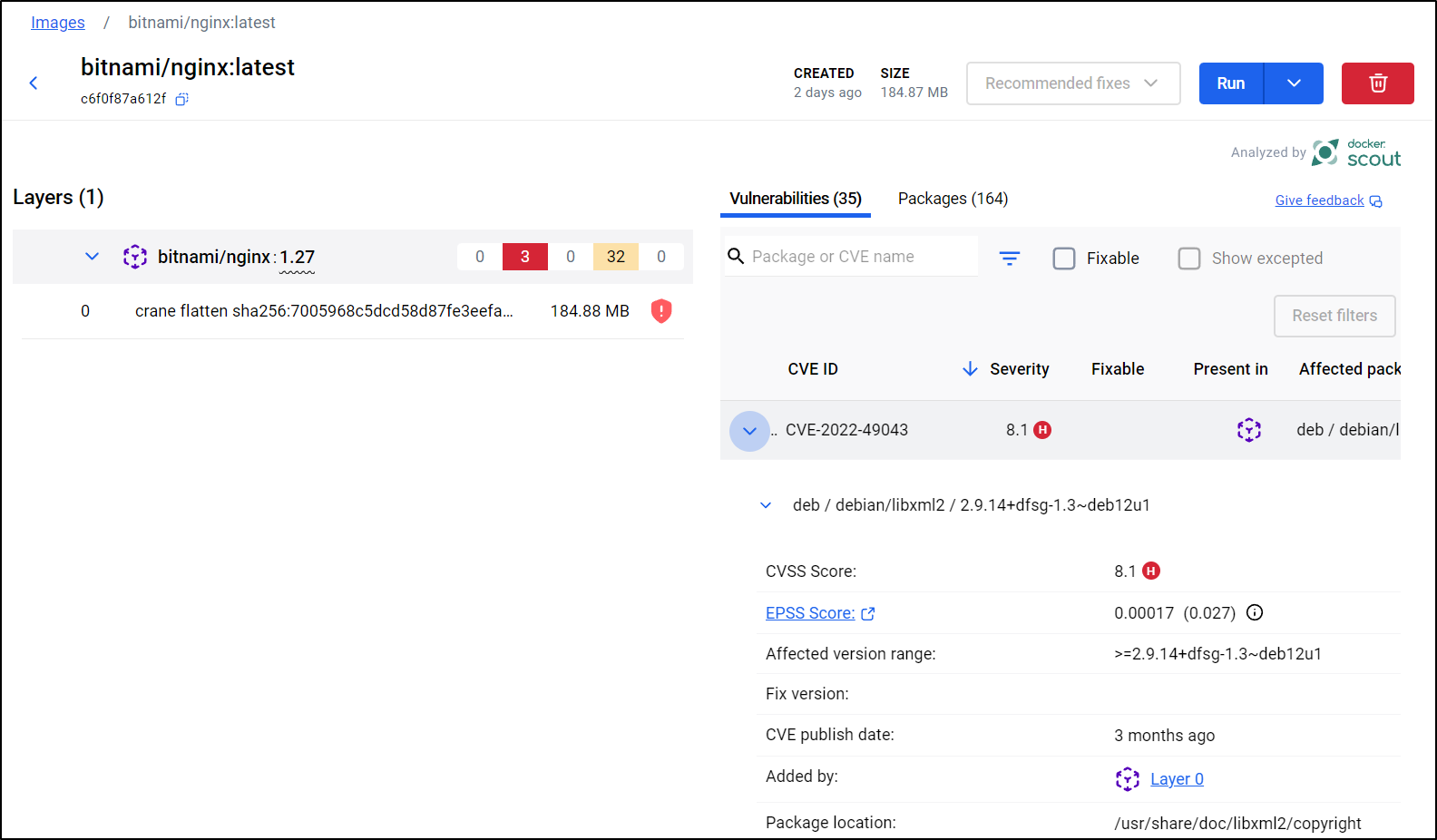
We can use the Image view to now see results for Bitnami’s Nginx
One feature that is nice here is the ability to view by Packages instead of just CVEs
This is helpful as most of the critical come from Libxml2 and as the CVE description of, CVE-2022-49043 for instance, says “xmlXIncludeAddNode in xinclude.c in libxml2 before 2.11.0 has a use-after-free.”, I could just look to update libxml2 to a version greater than 2.11 like the latest 2.13.8 or 2.14.2 (as of this writing).
On Scores (and politics)
For instance, Harbor, by way of [AcquaSec] calls CVE-2022-49043 a Moderate severity issue with a CVSS 3.x of “5.9 Moderate”
Whereas, Scout calls CVE-2022-49043 a High Priority issue with a CVSS Score of 8.1 High
This might be interesting as I believe the US system of NIST here linked by Aqua still has it listed as “Awaiting Analysis”
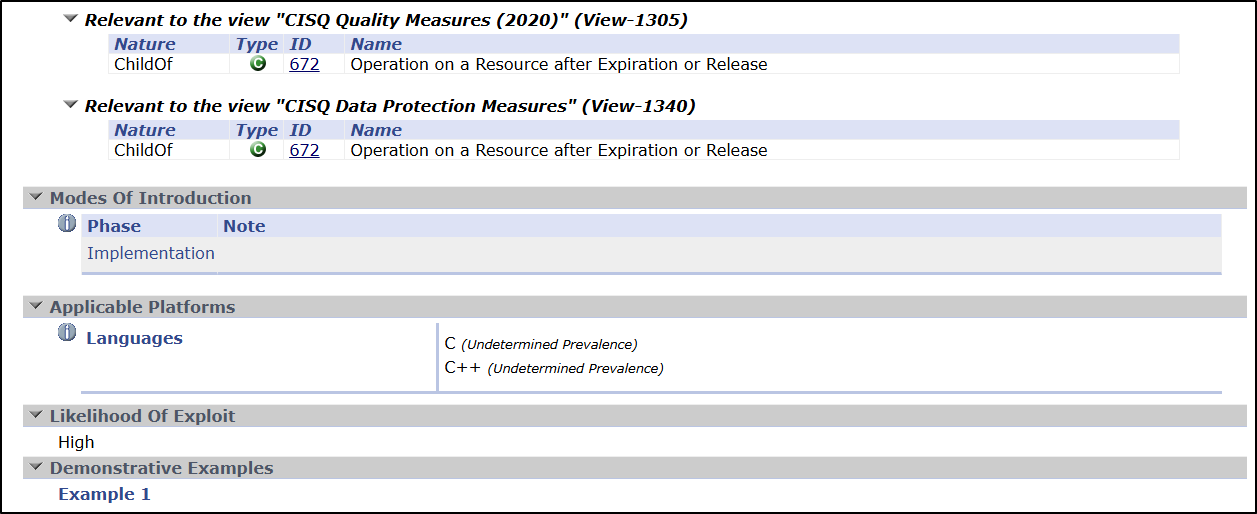
Mitre’s CWE on the other hand does mark this as High in “Likelihood of Exploit”, so perhaps that’s where Scout marked it high.
A few more references:
- Redhat’s portal marks it Moderate Impace and a CVSS v3 score of 5.9
- Ubuntu gives it Medium Priority
- Amazon gives it Important with a CVSS v3 score of 7.4
- Github gives it High Severity with a score of 8.2
So I guess this is an example of the fact that “scores” are not 100% agreed upon, even by industry leaders. While MITRE, a defense contractor of the US Government assigns IDs, the actual database is in NIST.gov hands.
There are current political issues with the US Government and thus after it appeared the Mitre contract might expire (as well as a general gutting of the US Government which I will push down my rage and bile and avoid talking about) (see more), just this week a new CVE Foundation was formed to take over this work in the future.
Summary
Today we attempted to scan images in ACR using Defender for Cloud. After pushing a new image, we did see some results, but the fact they are disconnected from the Repository view altogether means I wouldn’t rely on it.
I showed how we can use Harbor, an Open-Source container registry to scan for CVEs and then lastly we looked at Docker Scout, both in the CLI and Docker Desktop.