Published: Apr 1, 2025 by Isaac Johnson
In this article, I dig into two really good Open-Source productivity apps - Fluid Calendar and WPS-Office. Fluid Cal works great to front Google or O365 calendars with bi-directional syncing and tasks. WPS-Office is a very full featured Office suite with Documents, Spreadsheets and Presentations. I’ll cover basics, but also syncing files and printing.
Fluid Cal
FluidCalender is an open-source calendaring app that does have a SaaS option (coming soon).
If we go to their Github, we can see this is pretty easy to fire up with docker compose
$ git clone https://github.com/dotnetfactory/fluid-calendar.git
$ cd fluid-calendar
$ docker compose -f docker-compose.yml up -d
Docs didn’t quite play out as it seems to need an .env file, but I added that step:
builder@DESKTOP-QADGF36:~/Workspaces$ git clone https://github.com/dotnetfactory/fluid-calendar.git
Cloning into 'fluid-calendar'...
remote: Enumerating objects: 2587, done.
remote: Counting objects: 100% (537/537), done.
remote: Compressing objects: 100% (266/266), done.
remote: Total 2587 (delta 294), reused 388 (delta 227), pack-reused 2050 (from 1)
Receiving objects: 100% (2587/2587), 1.58 MiB | 6.96 MiB/s, done.
Resolving deltas: 100% (1380/1380), done.
builder@DESKTOP-QADGF36:~/Workspaces$ cd fluid-calendar
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ cp .env.example .env
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ docker compose -f docker-compose.yml up -d
[+] Running 31/31
✔ db Pulled 12.2s
✔ app Pulled 120.2s
[+] Running 4/4
✔ Network fluid-calendar_default Created 0.1s
✔ Volume "fluid-calendar_postgres_dev_data" Created 0.0s
✔ Container fluid-calendar-db-1 Healthy 7.2s
✔ Container fluid-calendar-app-1 Started 6.7s
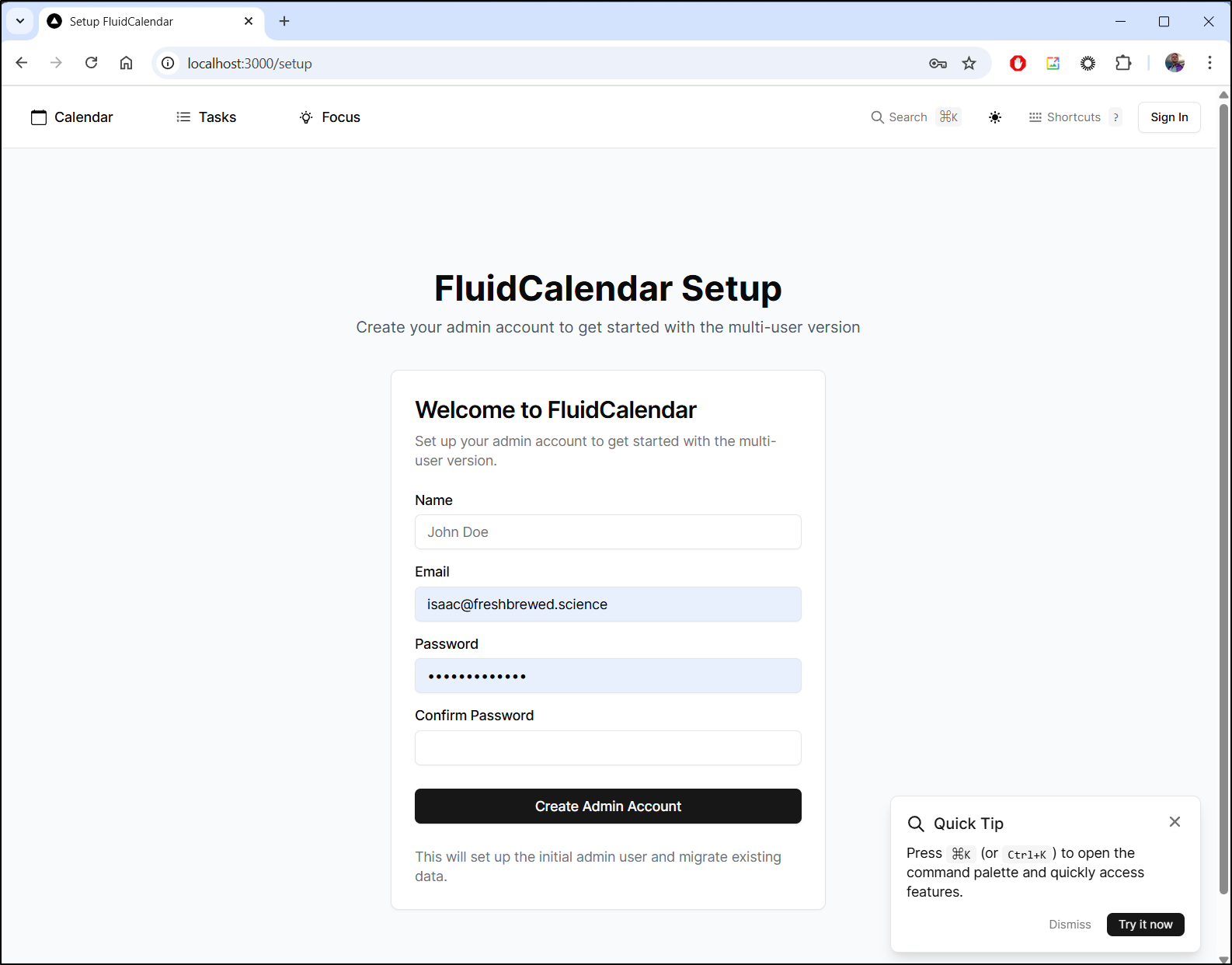
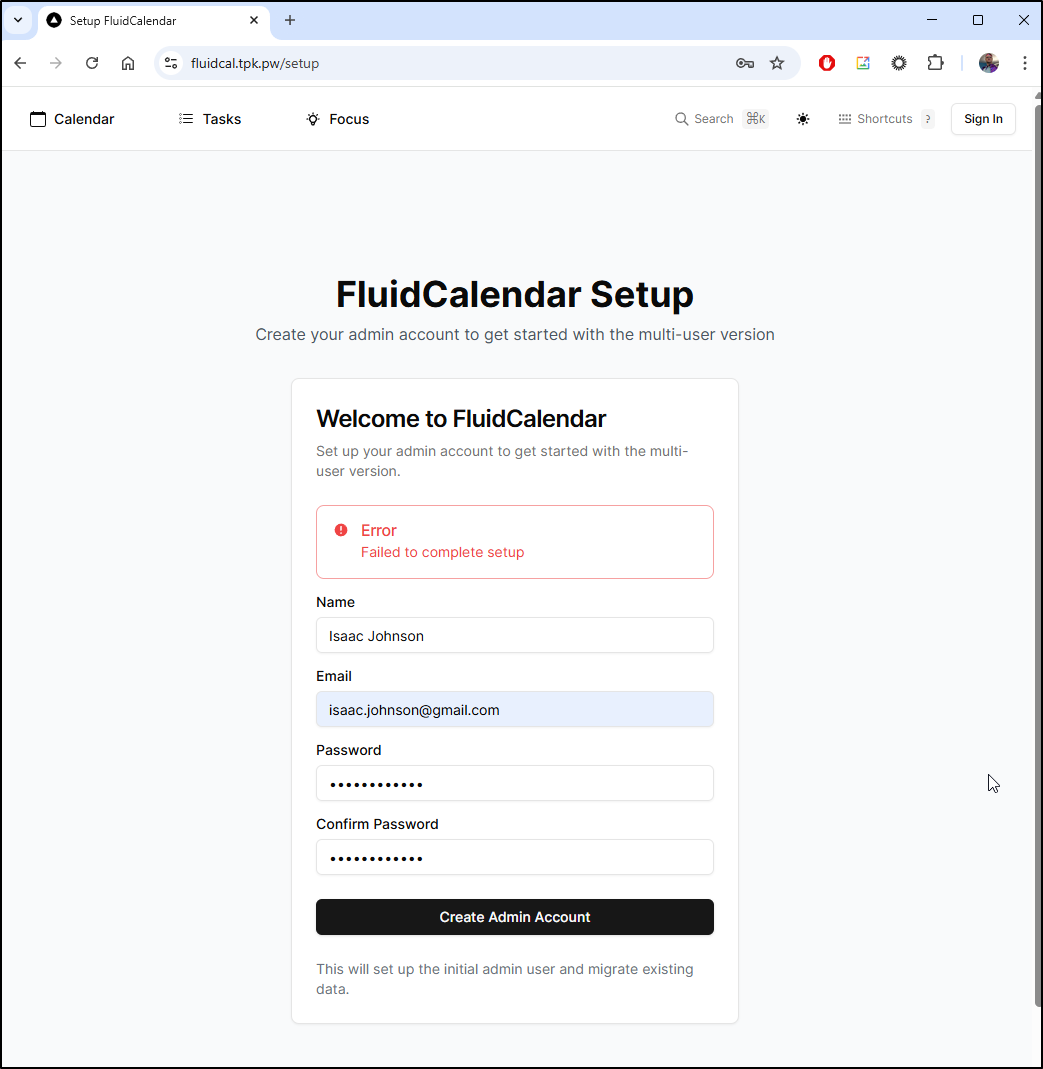
I’m now greated with a signin page
I can create an admin user
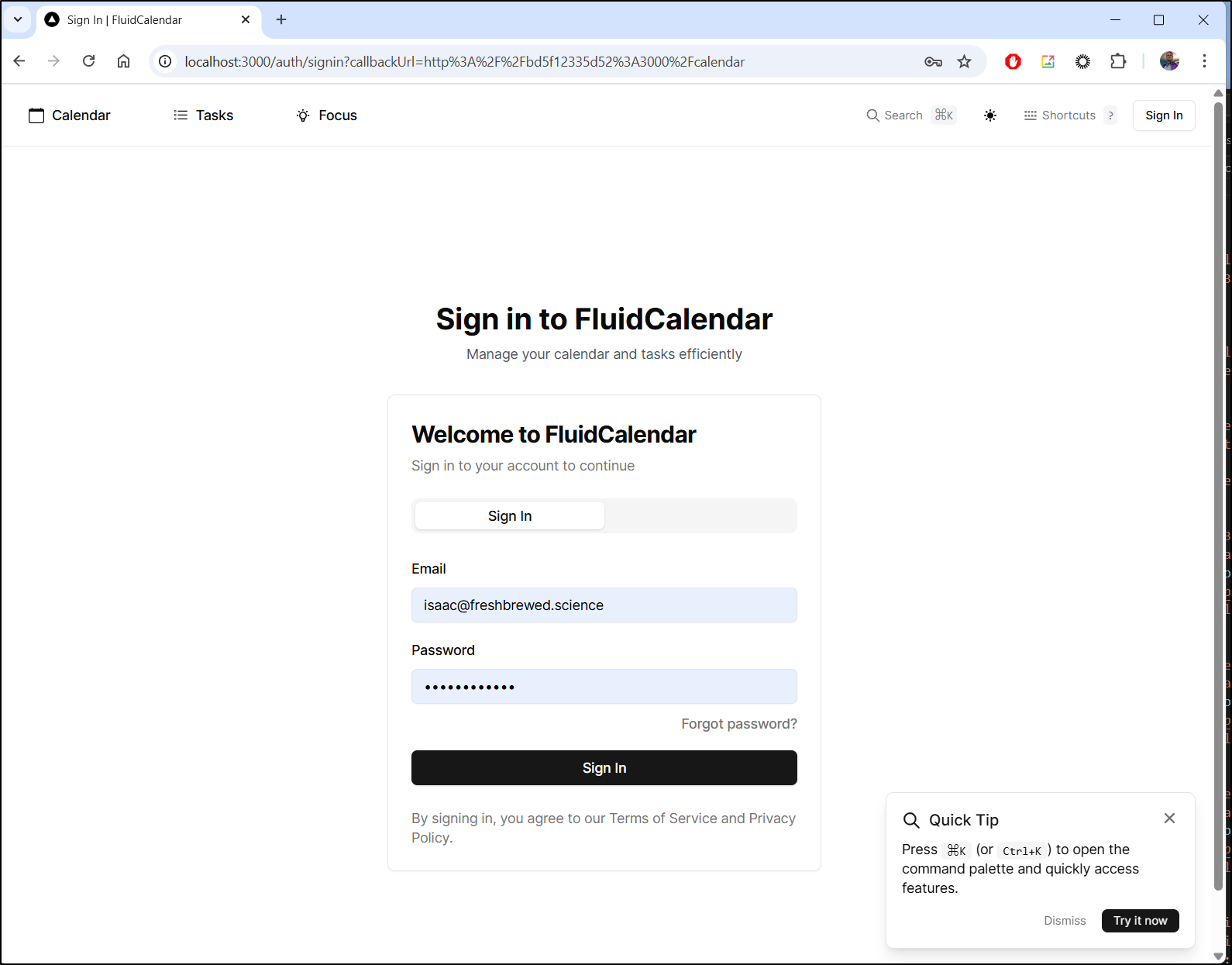
Which then has me turn around to sign in
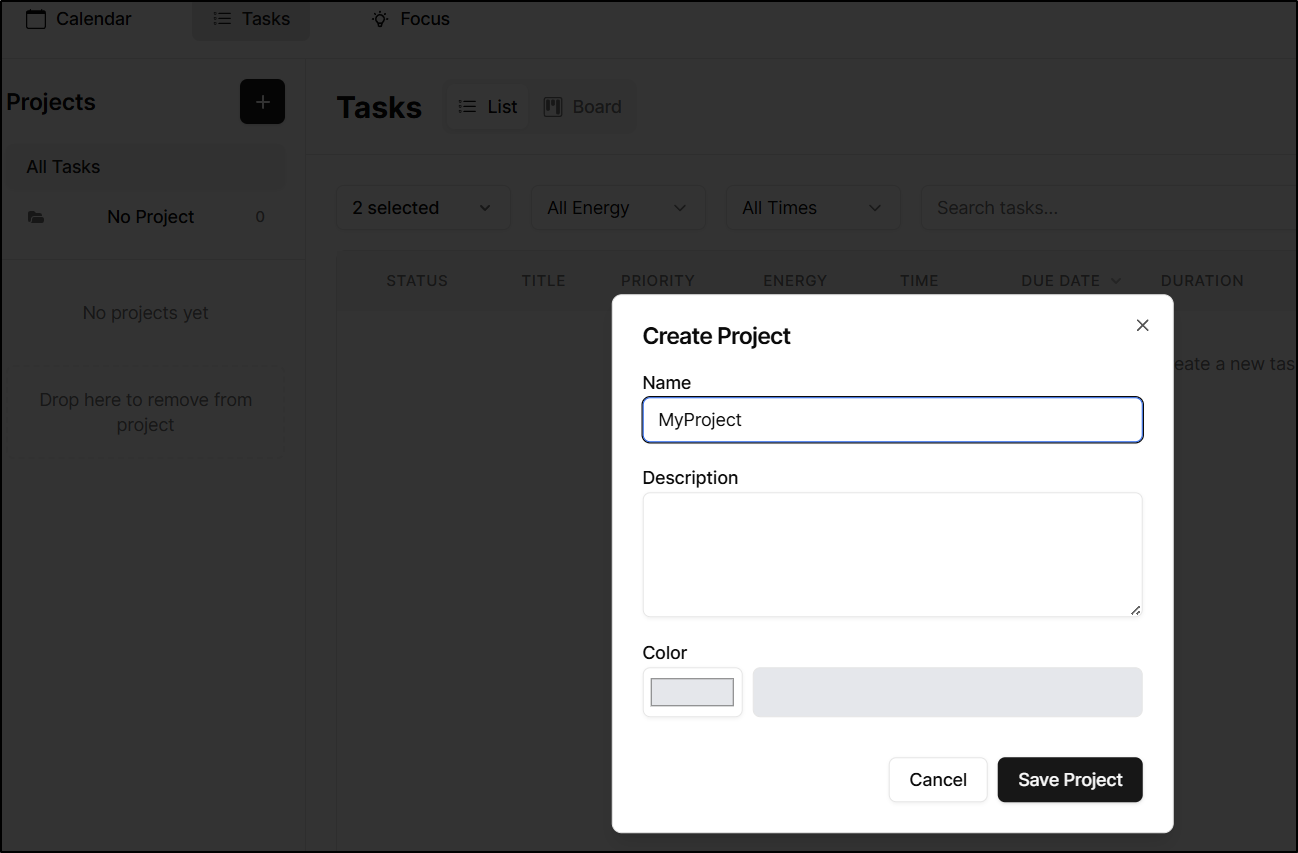
Usage
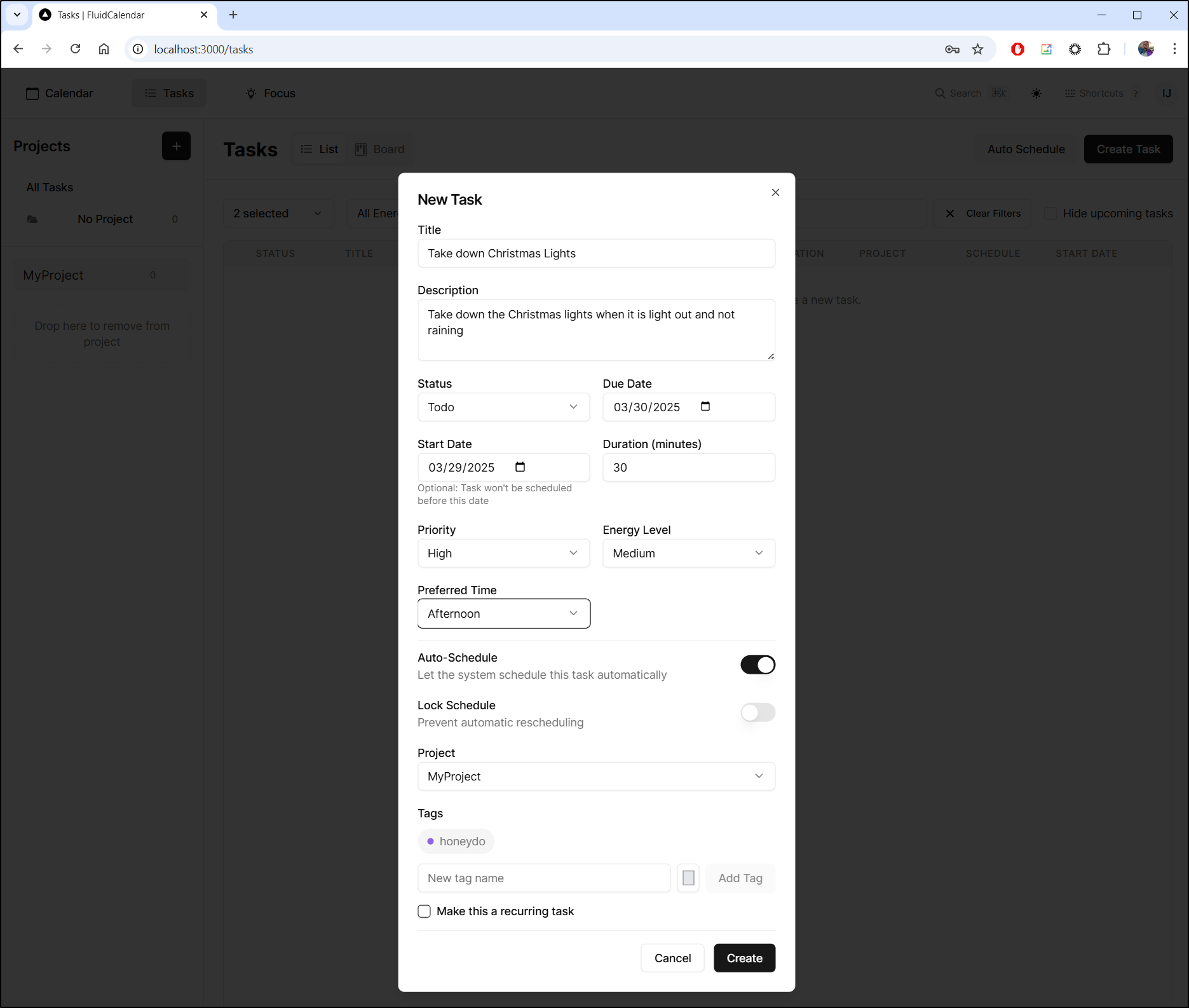
Let’s start with tasks. I’ll need to create a project
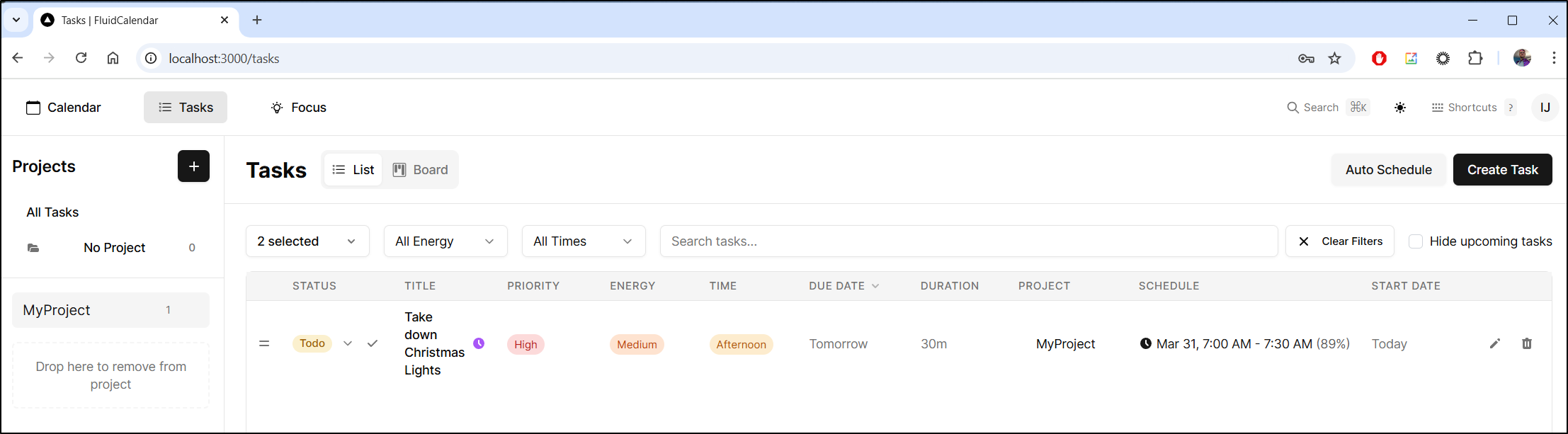
I can the add a task
It’s now on my list of to-dos
However, it does not show up on the calendar
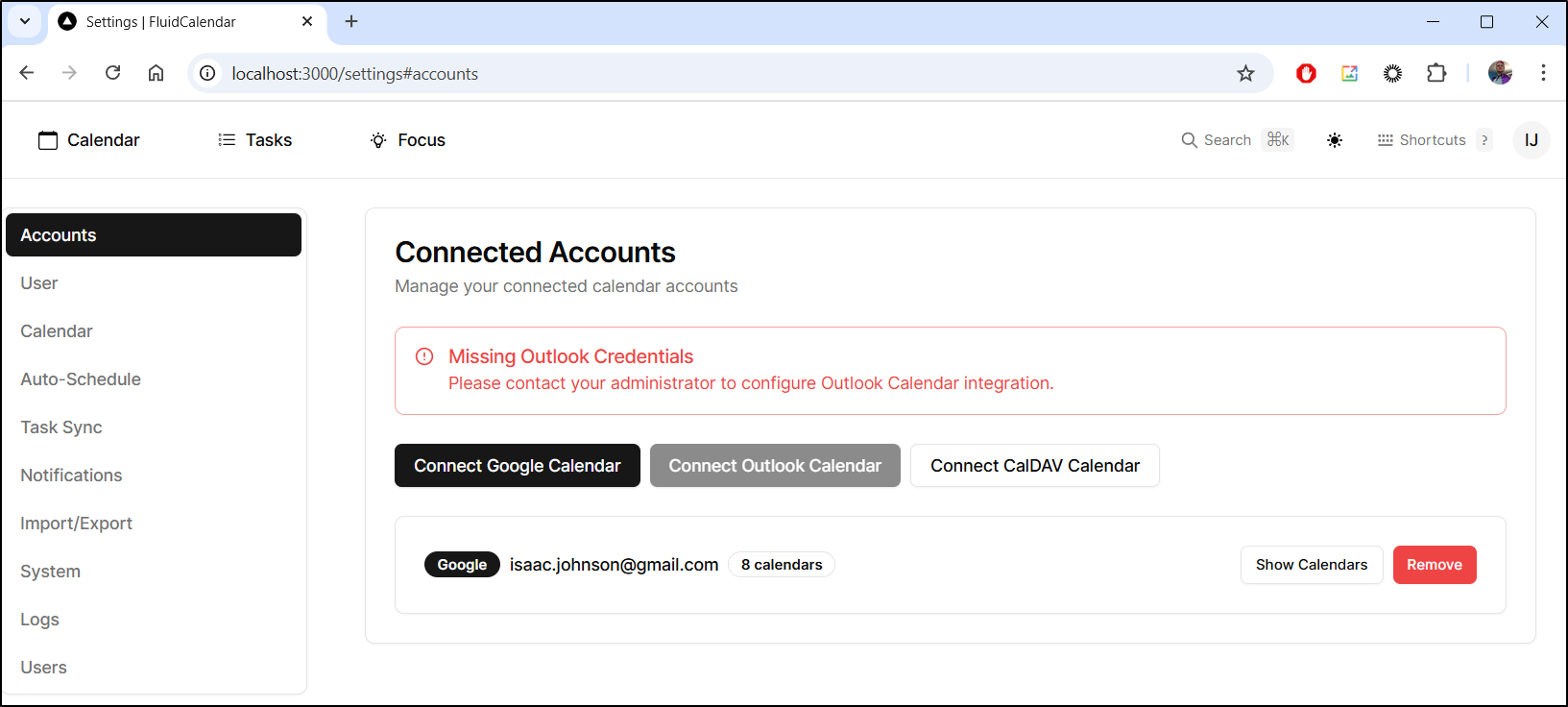
From what I can tell, I really cannot use this cal independent of a Google Calendar, CalDev or Outlook backend
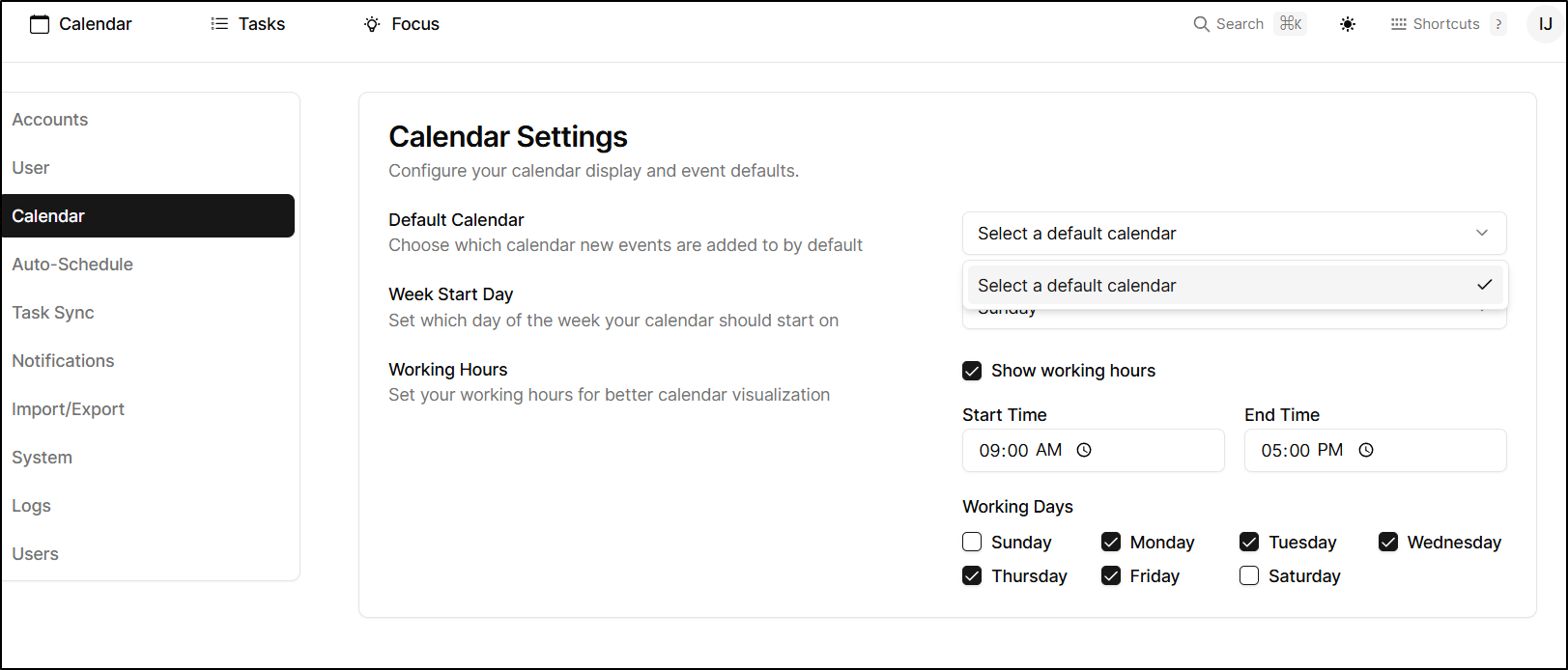
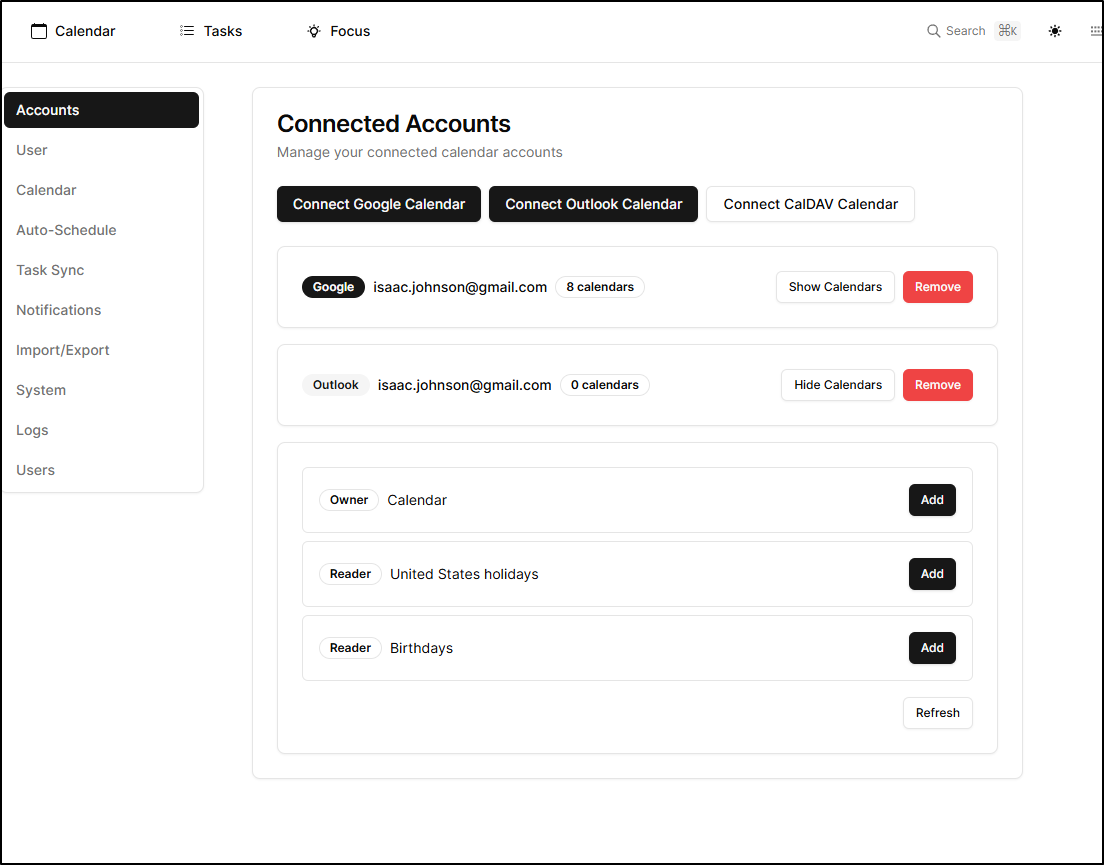
In settings we can pick a default calendar, but a default of those already added
It would seem that really is just Google and Outlook:
Google Cal integration
For the sake of argument, let’s just say we wanted to tie this to Google Calendar
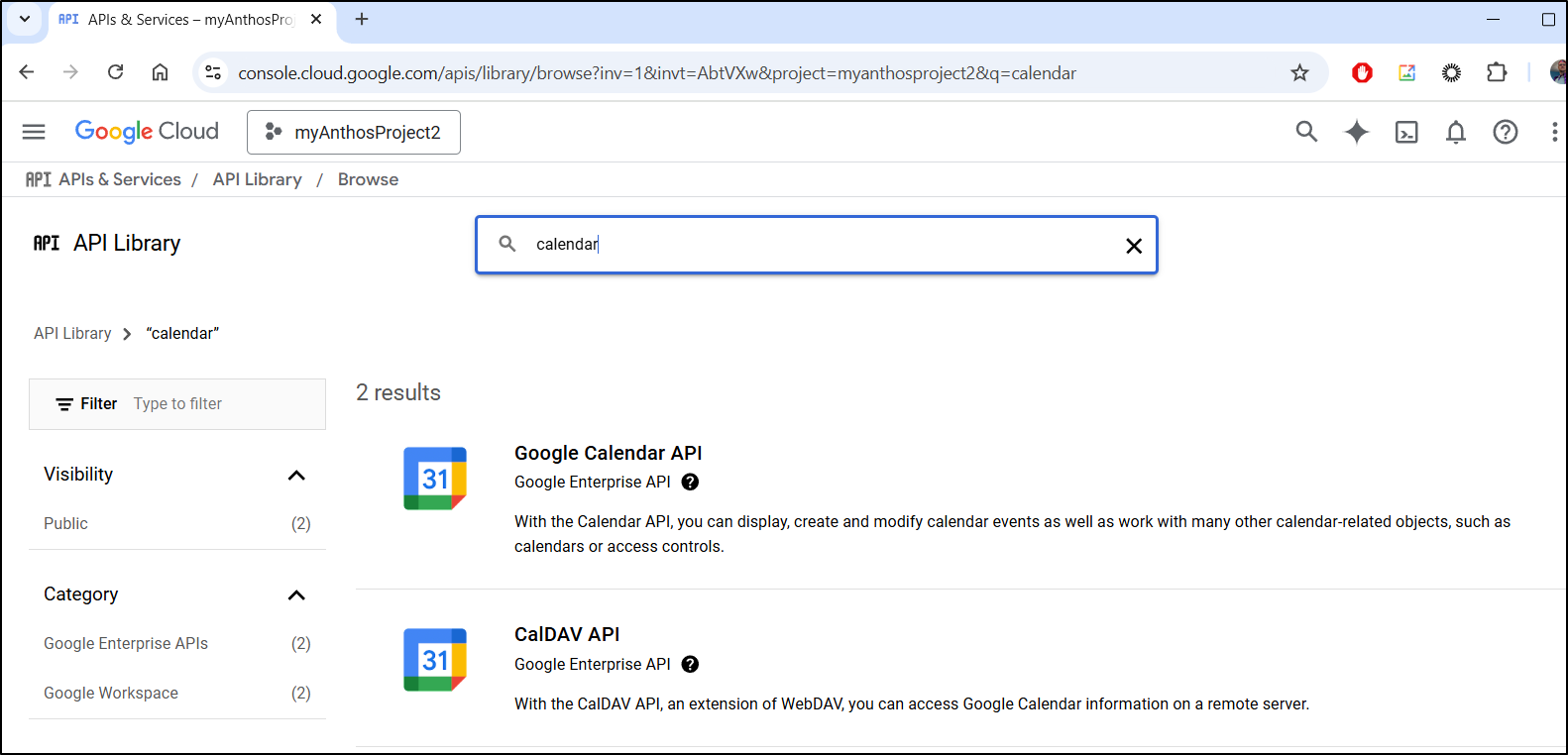
I would enable the “Google Calendar API” is the APIs section
Click enable
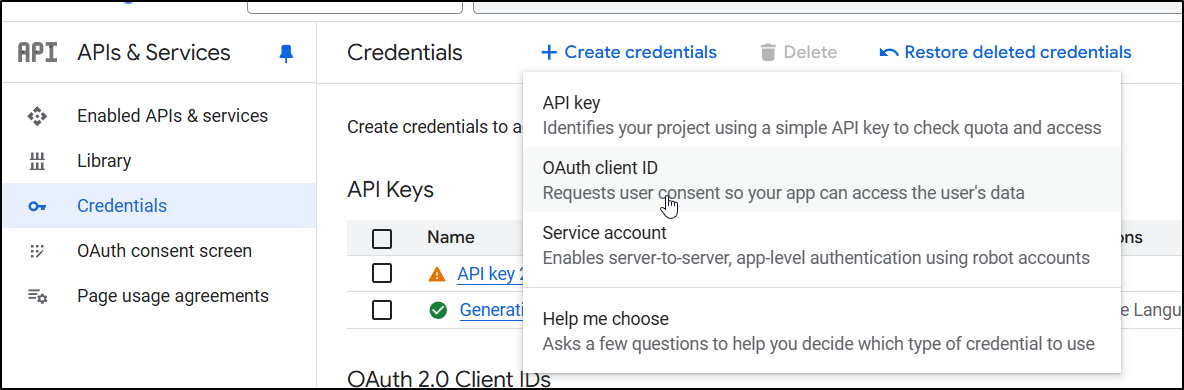
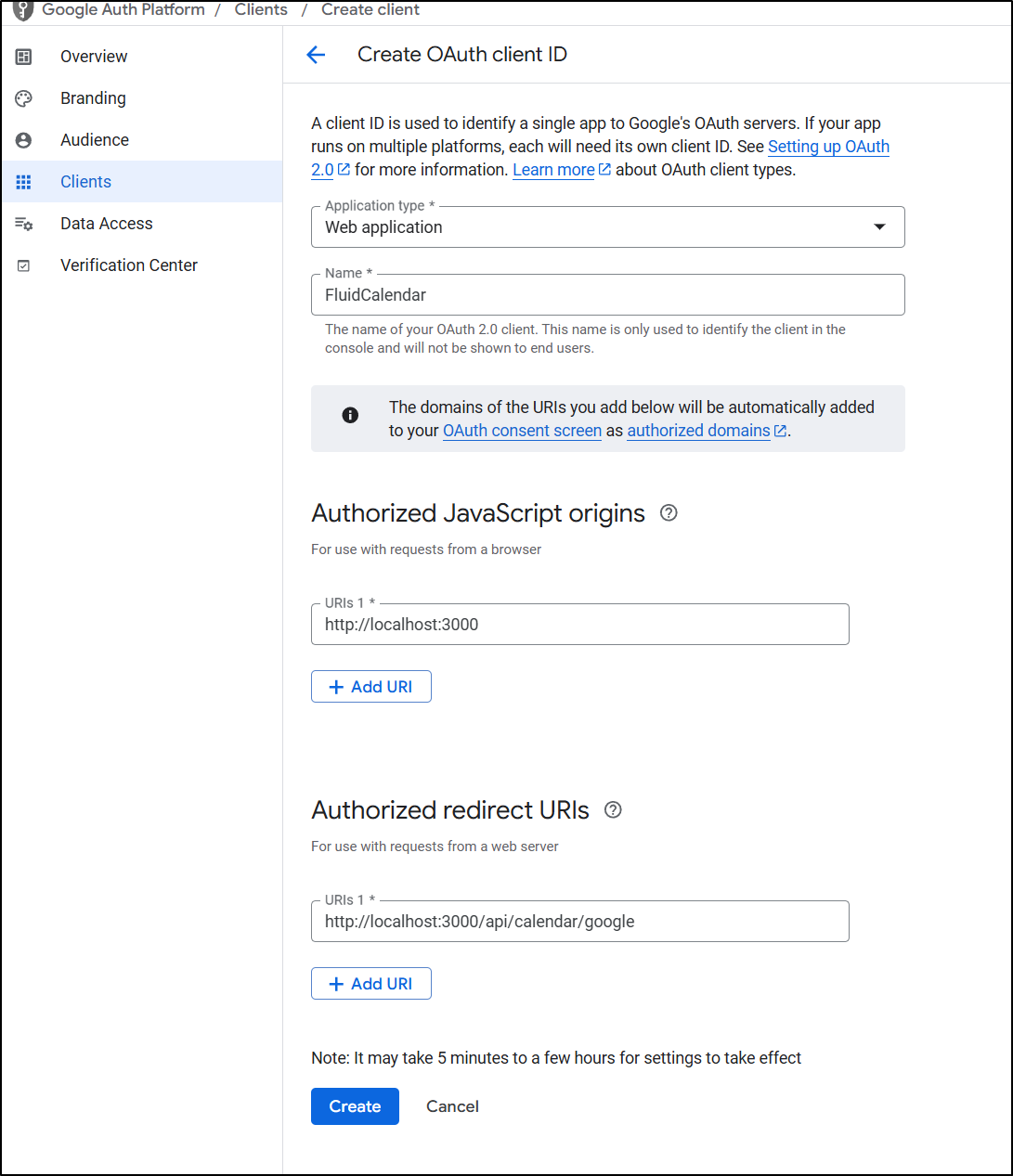
Then, in Credentials, generate a new OAuth 2 client
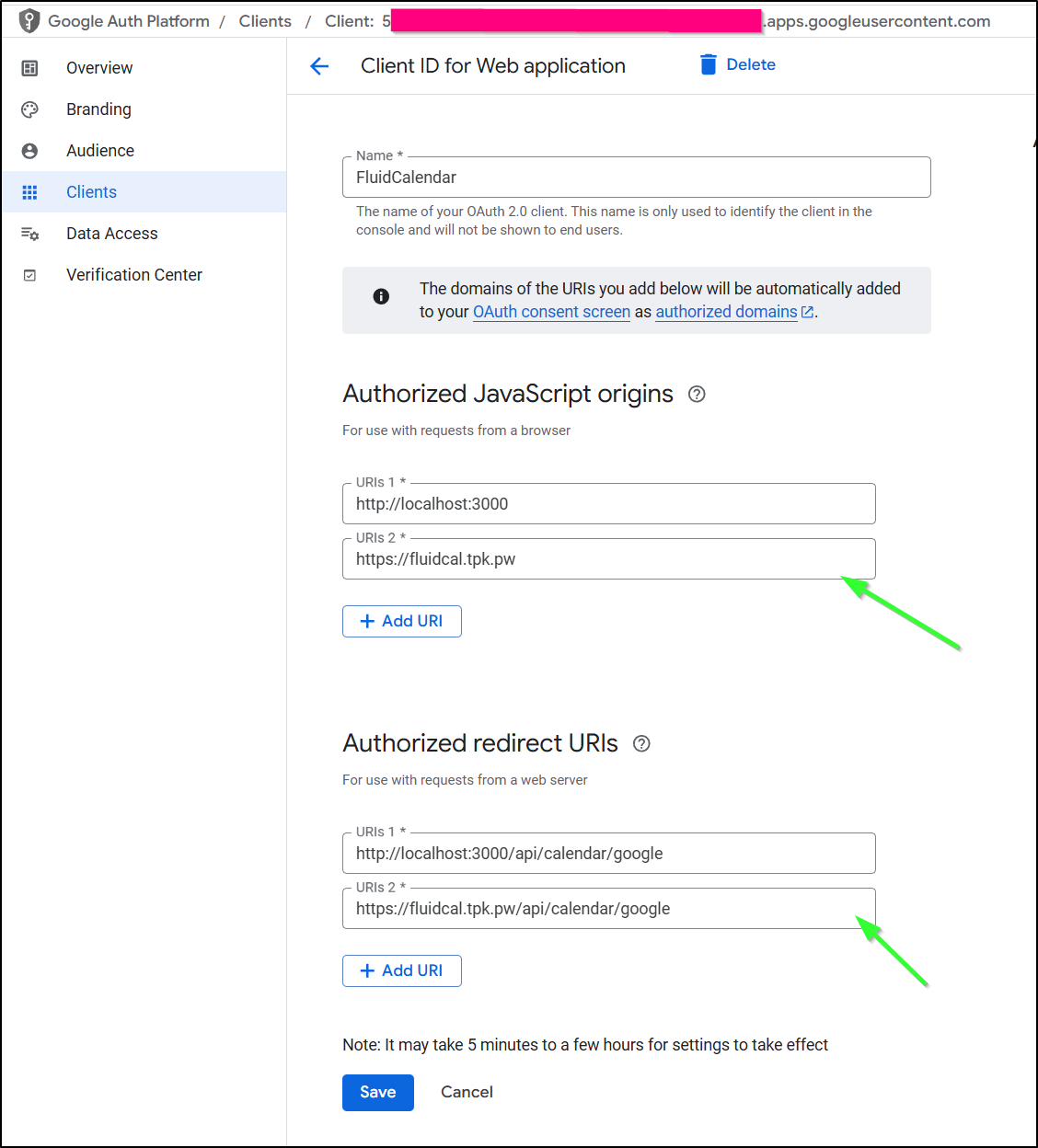
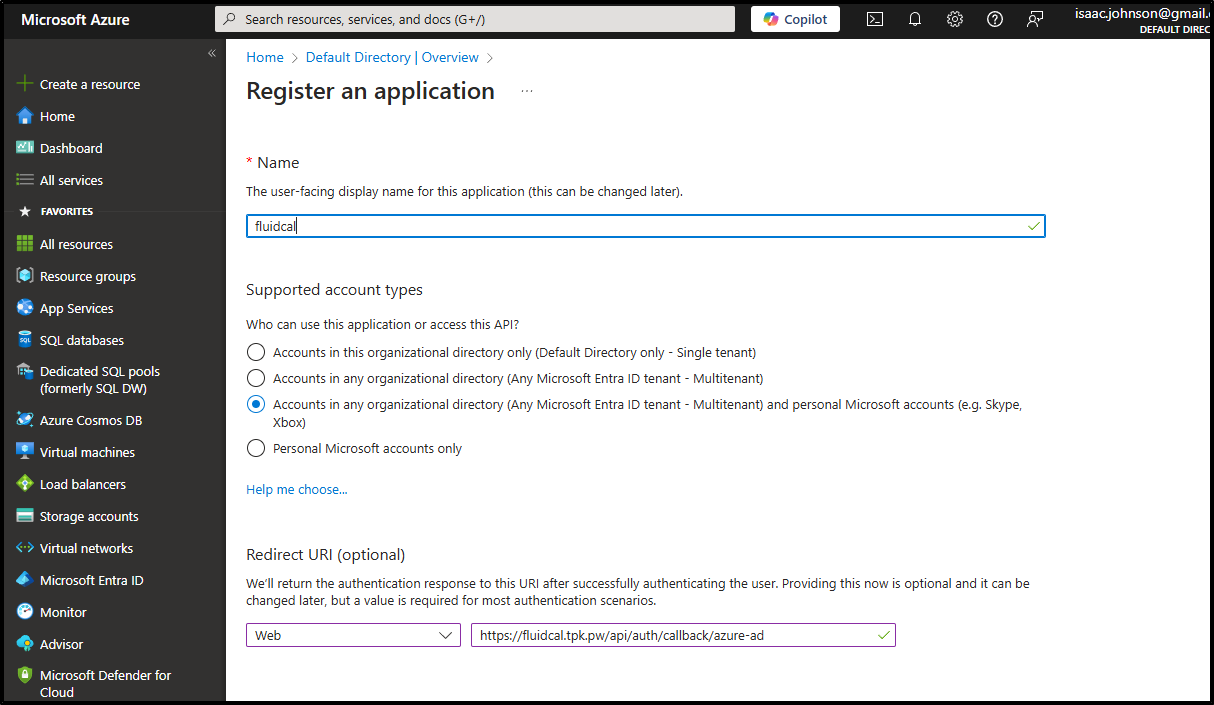
I’ll give it a name and add an authorized origin and redirect. If I were to keep this, I would at this time also add what I would assume the Domain would be (e.g. fluidcal.tpk.pw or whatever I might use)
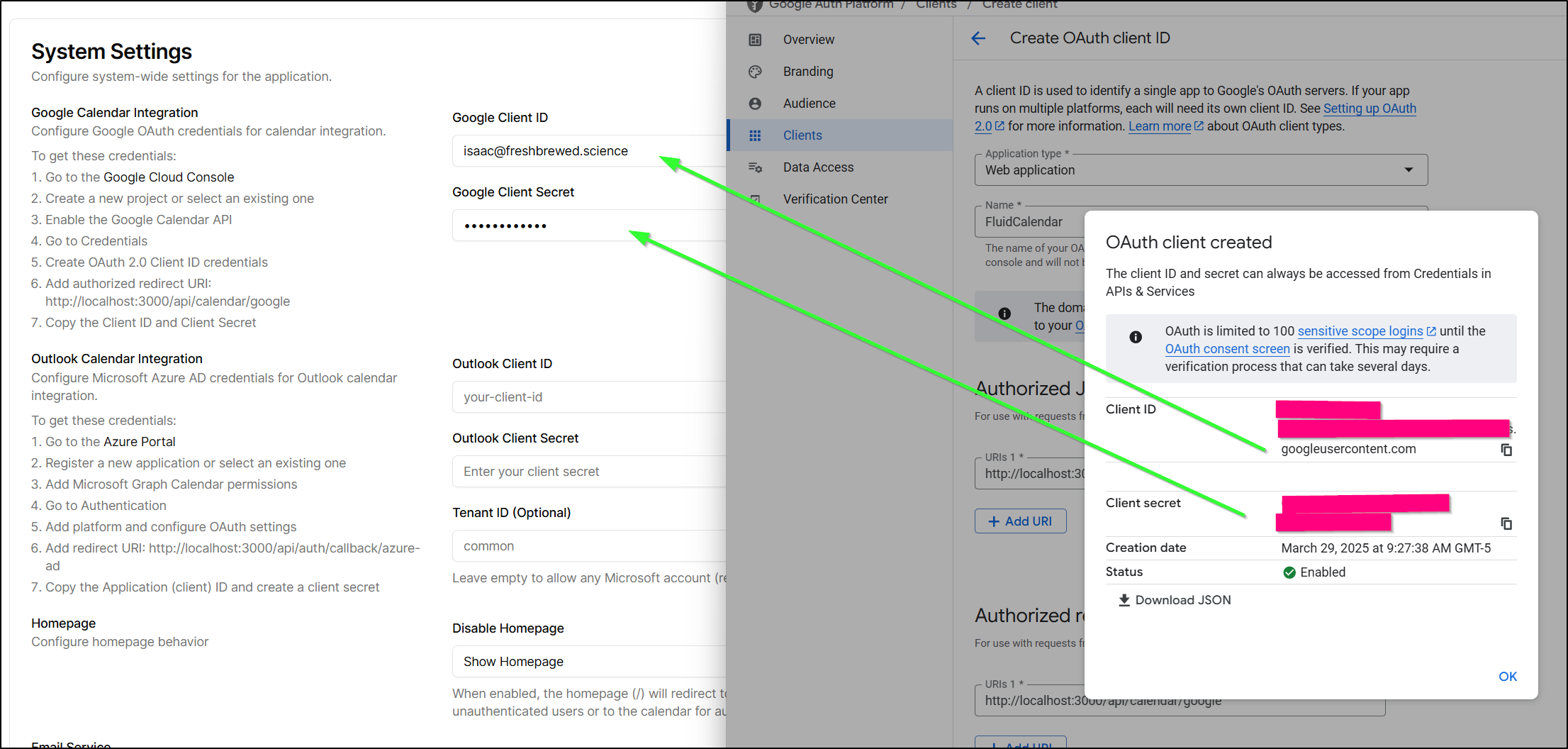
I can now copy over the client secret and id
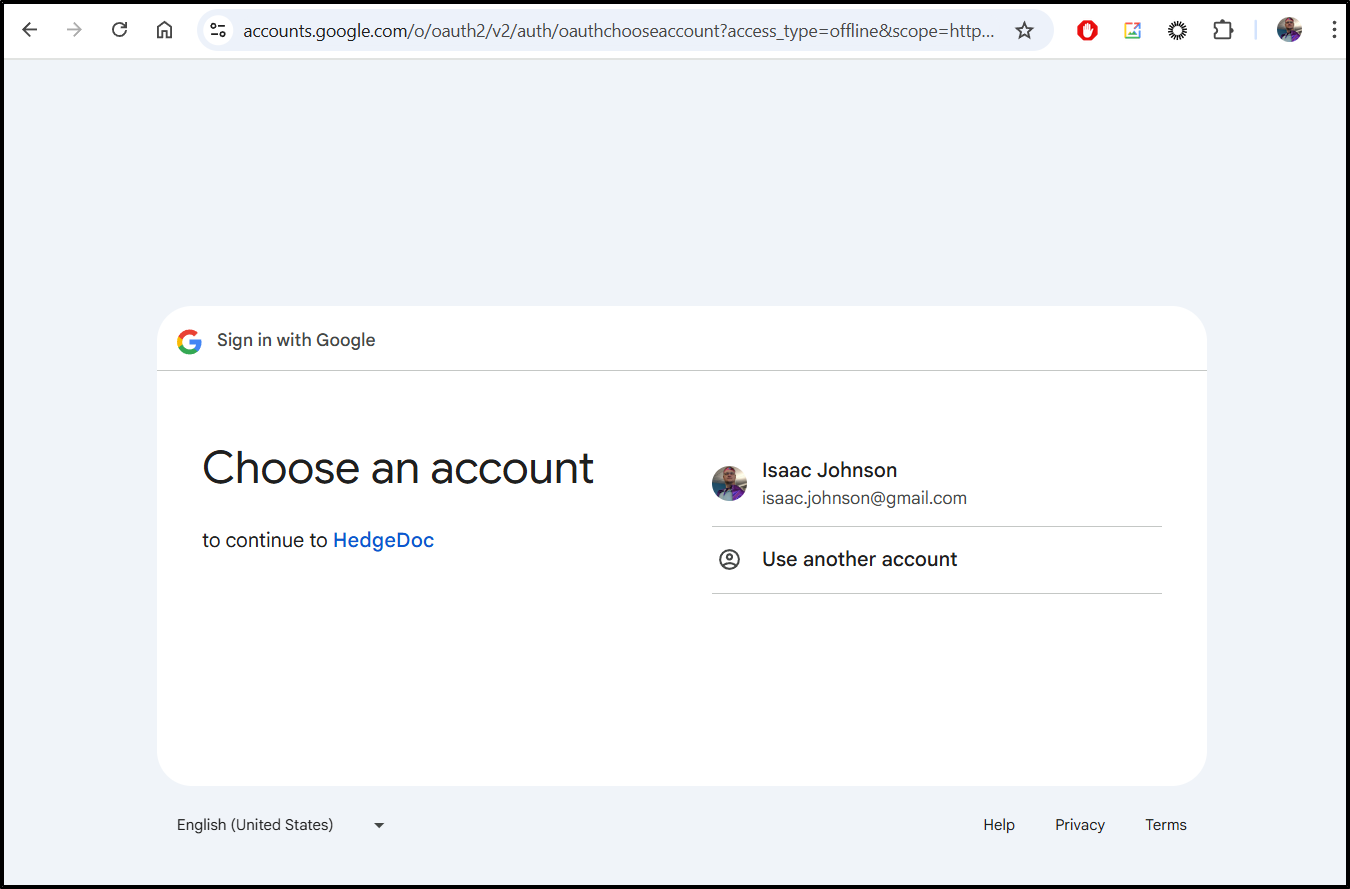
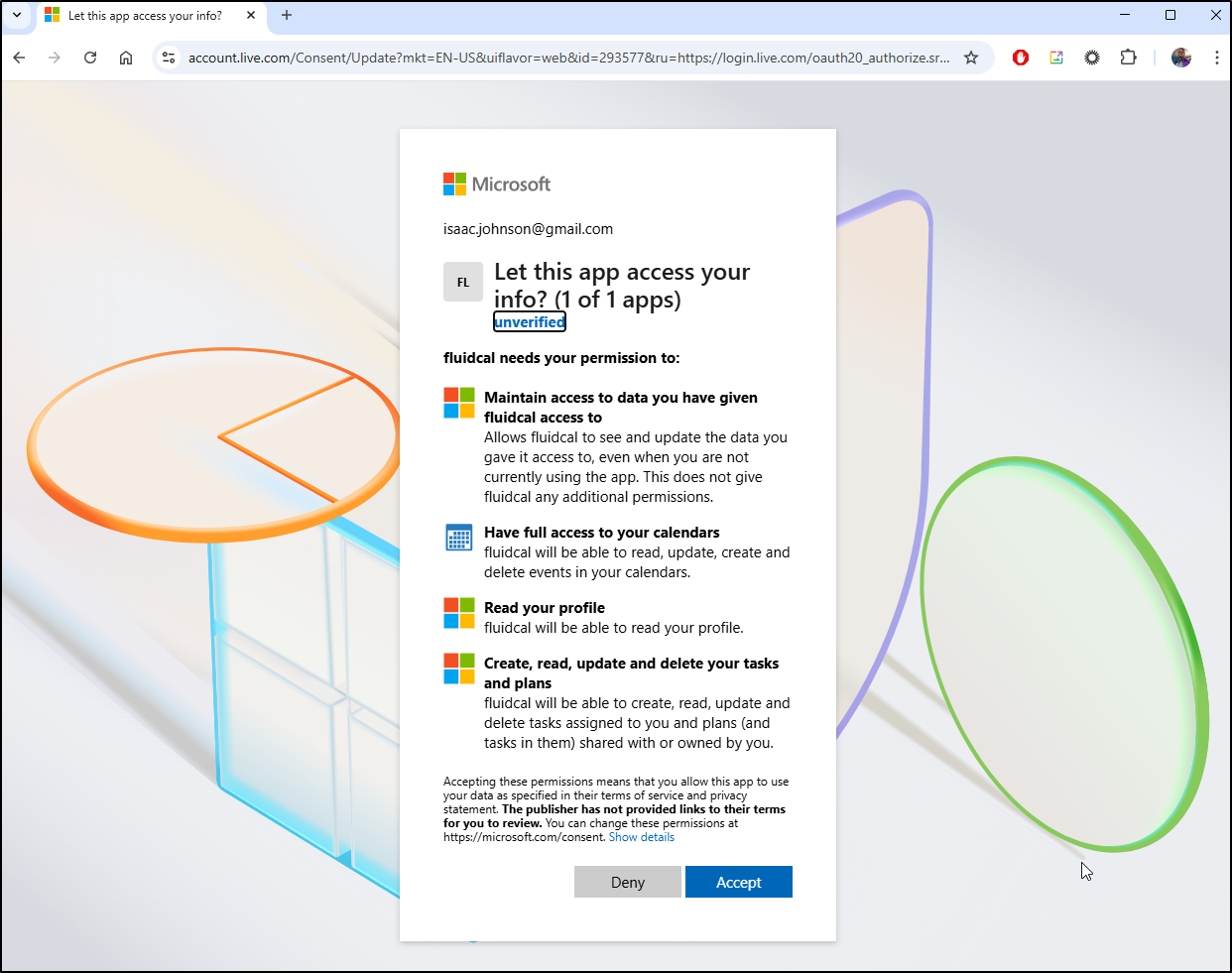
Now when I go to Calendars and click “Connect to Google”, I’m prompted for a login
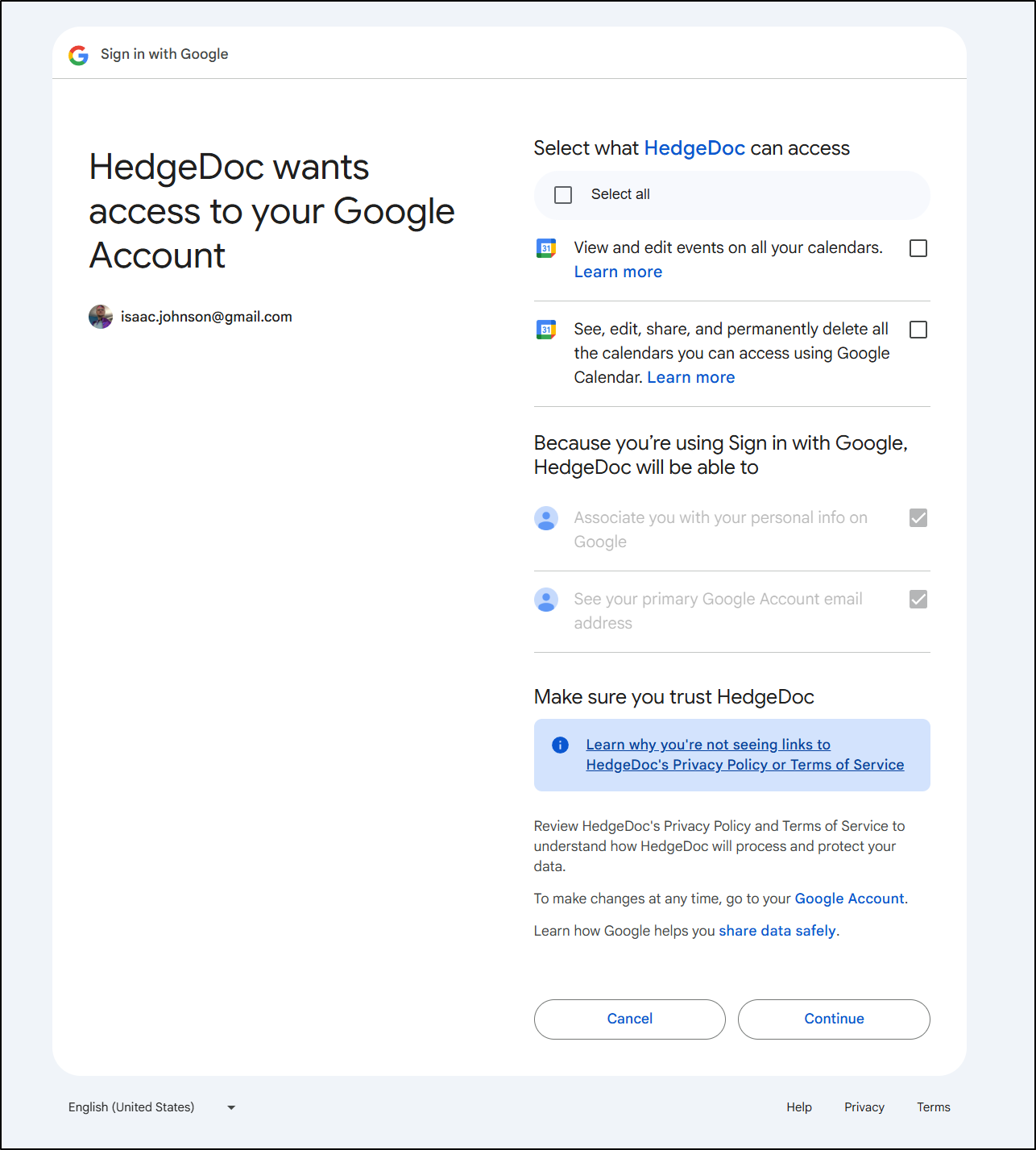
Even though it says “HedgeDoc” (must just be confusing the last time i used “localhost”), I agreed and had to work past a “this is unsafe” (Since I’m using http). I then click to share cal
And it returns that it is connected
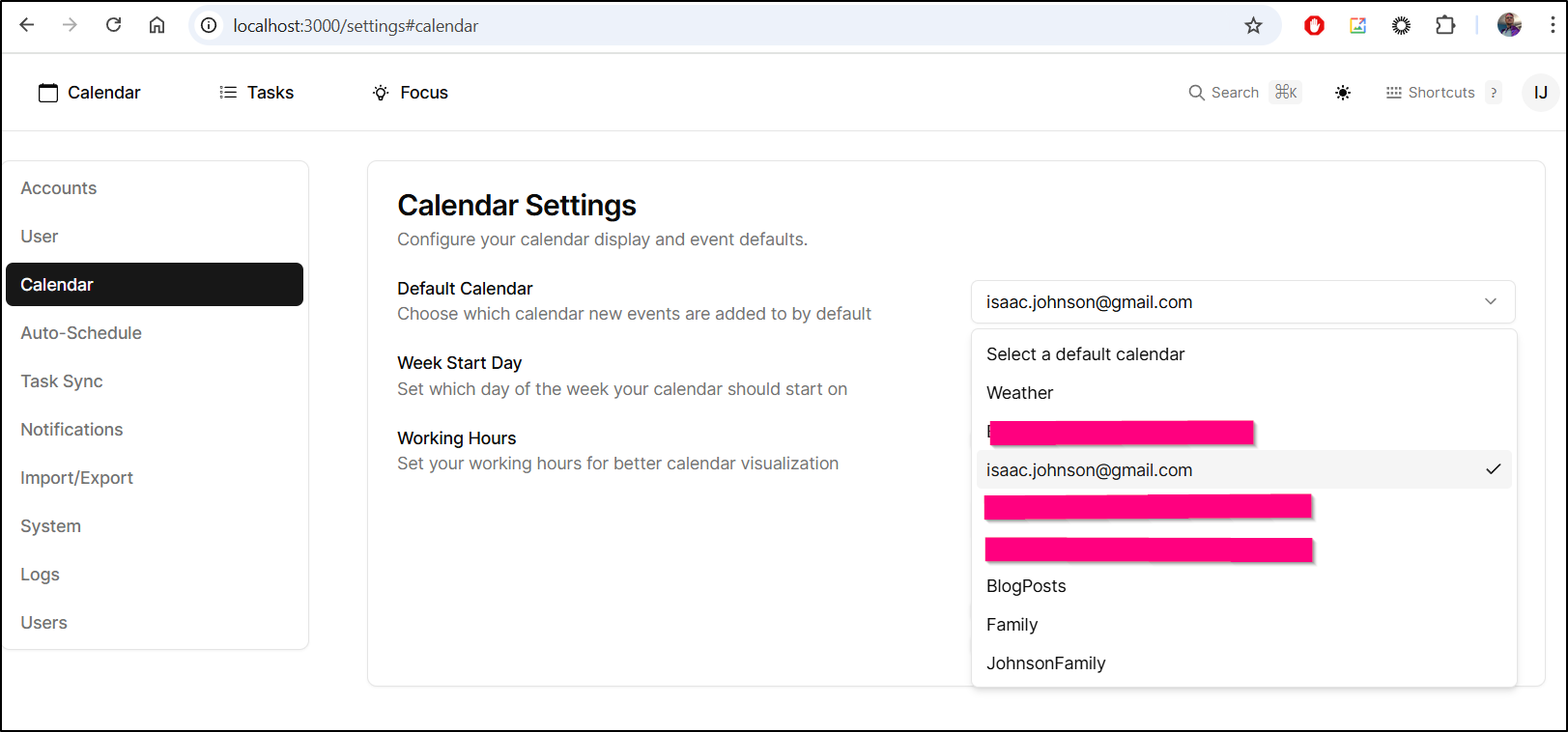
I can now pick a default calendar (for adding events)
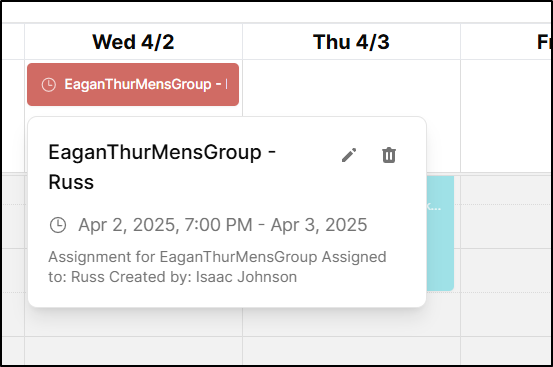
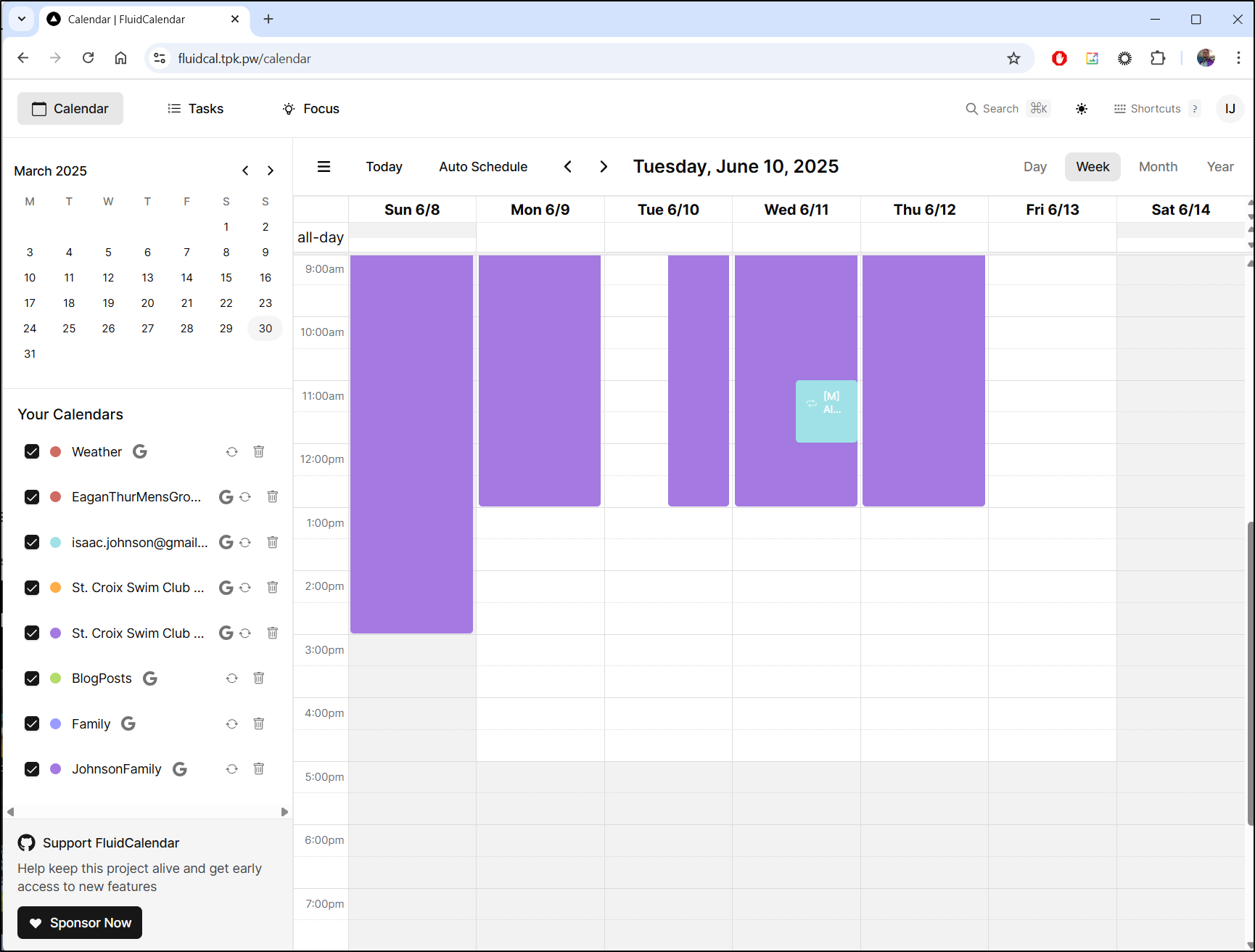
Once I clicked Sync, I saw all my calendars sync, including pulling over the one from Fika.
Which is pretty cool as I can click the day and see it was assigned to Russ which matches that particular day in the Meet/Fika app
hosting
I wanted to host the instance in k8s next, but needed a database.
I fired off the OOTB Bitnami chart
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ kubectl create ns fluidcal
namespace/fluidcal created
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ helm install postgres -n fluidcal oci://registry-1.docker.io/bitnamicharts/postgres
ql
Pulled: registry-1.docker.io/bitnamicharts/postgresql:16.6.0
Digest: sha256:0f651f09ac23251aef4f914e8d82427ffc8d31ce60964bfe721885dc5aa6b241
NAME: postgres
LAST DEPLOYED: Sat Mar 29 09:58:46 2025
NAMESPACE: fluidcal
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
CHART NAME: postgresql
CHART VERSION: 16.6.0
APP VERSION: 17.4.0
Did you know there are enterprise versions of the Bitnami catalog? For enhanced secure software supply chain features, unlimited pulls from Docker, LTS support, or application customization, see Bitnami Premium or Tanzu Application Catalog. See https://www.arrow.com/globalecs/na/vendors/bitnami for more information.
** Please be patient while the chart is being deployed **
PostgreSQL can be accessed via port 5432 on the following DNS names from within your cluster:
postgres-postgresql.fluidcal.svc.cluster.local - Read/Write connection
To get the password for "postgres" run:
export POSTGRES_PASSWORD=$(kubectl get secret --namespace fluidcal postgres-postgresql -o jsonpath="{.data.postgres-password}" | base64 -d)
To connect to your database run the following command:
kubectl run postgres-postgresql-client --rm --tty -i --restart='Never' --namespace fluidcal --image docker.io/bitnami/postgresql:17.4.0-debian-12-r11 --env="PGPASSWORD=$POSTGRES_PASSWORD" \
--command -- psql --host postgres-postgresql -U postgres -d postgres -p 5432
> NOTE: If you access the container using bash, make sure that you execute "/opt/bitnami/scripts/postgresql/entrypoint.sh /bin/bash" in order to avoid the error "psql: local user with ID 1001} does not exist"
To connect to your database from outside the cluster execute the following commands:
kubectl port-forward --namespace fluidcal svc/postgres-postgresql 5432:5432 &
PGPASSWORD="$POSTGRES_PASSWORD" psql --host 127.0.0.1 -U postgres -d postgres -p 5432
WARNING: The configured password will be ignored on new installation in case when previous PostgreSQL release was deleted through the helm command. In that case, old PVC will have an old password, and setting it through helm won't take effect. Deleting persistent volumes (PVs) will solve the issue.
WARNING: There are "resources" sections in the chart not set. Using "resourcesPreset" is not recommended for production. For production installations, please set the following values according to your workload needs:
- primary.resources
- readReplicas.resources
Then did a port-forward to create a proper user
builder@DESKTOP-QADGF36:~$ kubectl port-forward --namespace fluidcal svc/postgres-postgresql 5432:5432 &
builder@DESKTOP-QADGF36:~$ psql --host 127.0.0.1 -U postgres -d postgres -p 5433
Handling connection for 5433
Password for user postgres:
Handling connection for 5433
psql (12.20 (Ubuntu 12.20-0ubuntu0.20.04.1), server 17.4)
WARNING: psql major version 12, server major version 17.
Some psql features might not work.
Type "help" for help.
postgres=# create database fluid_calendar;
CREATE DATABASE
postgres=# create user fluidcal with encrypted password 'notthepassword';
CREATE ROLE
postgres=# grant all privileges on database fluid_calendar to fluidcal;
GRANT
postgres=# \q
I can now create the system with a simple k8s manifest:
$ cat k8s.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: app-config
data:
DATABASE_URL: "postgresql://fluidcal:notthepassword@postgres-postgresql:5432/fluid_calendar"
NEXTAUTH_URL: "https://fluidcal.tpk.pw"
NEXT_PUBLIC_APP_URL: "https://fluidcal.tpk.pw"
NEXTAUTH_SECRET: "your-secret-key-min-32-chars"
NEXT_PUBLIC_SITE_URL: "https://fluidcal.tpk.pw"
NEXT_PUBLIC_ENABLE_SAAS_FEATURES: "false"
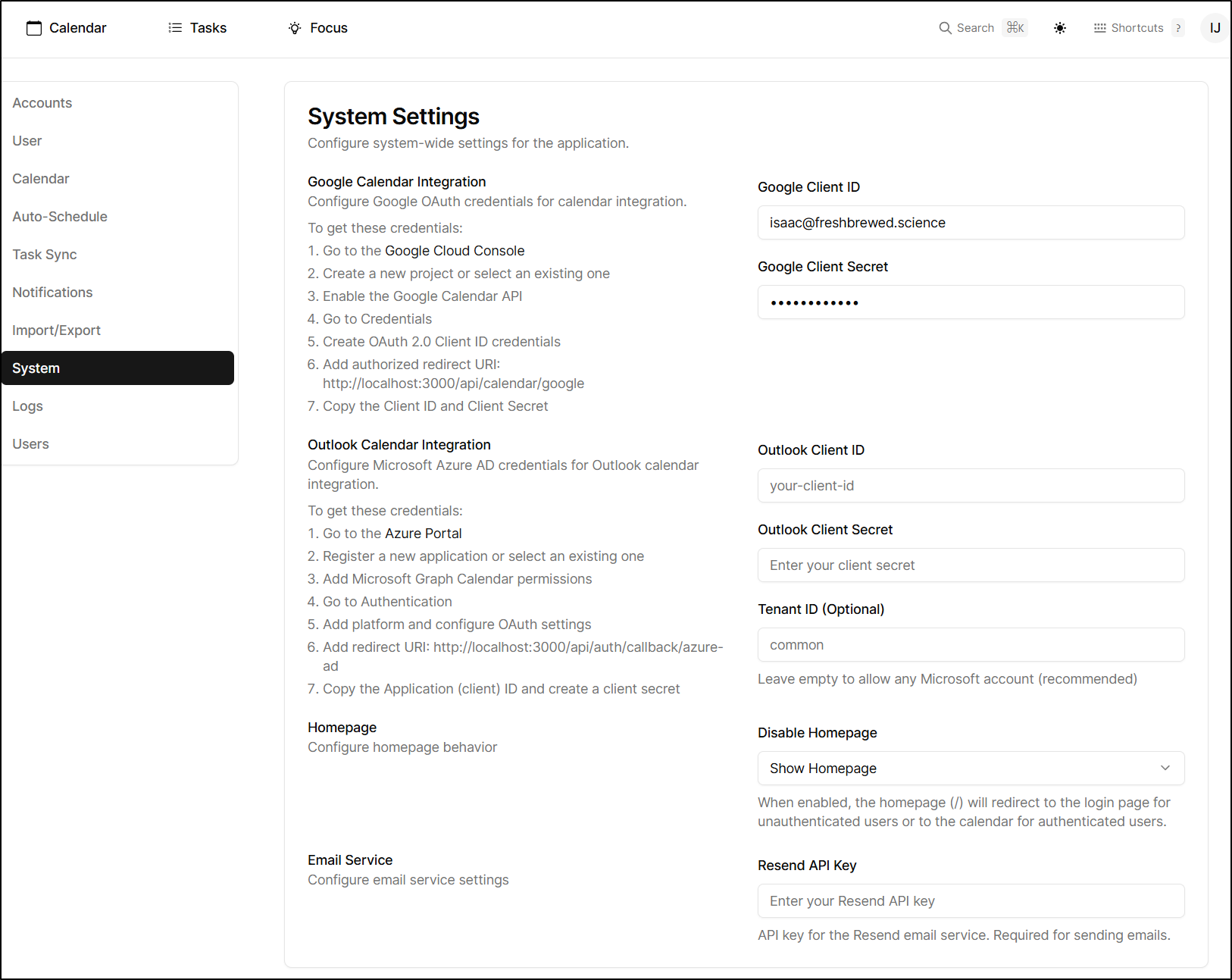
RESEND_API_KEY: "re_xxxxxxxxxxxxxxxxxxxxxx"
RESEND_FROM_EMAIL: "isaac@freshbrewed.science"
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: fluid-calendar
labels:
app: fluid-calendar
spec:
replicas: 1
selector:
matchLabels:
app: fluid-calendar
template:
metadata:
labels:
app: fluid-calendar
spec:
containers:
- name: fluid-calendar
image: eibrahim/fluid-calendar:latest
ports:
- containerPort: 3000
envFrom:
- configMapRef:
name: app-config
readinessProbe:
httpGet:
path: /
port: 3000
initialDelaySeconds: 10
periodSeconds: 5
resources:
requests:
memory: "256Mi"
cpu: "100m"
limits:
memory: "512Mi"
cpu: "500m"
---
apiVersion: v1
kind: Service
metadata:
name: fluid-calendar
spec:
selector:
app: fluid-calendar
ports:
- port: 80
targetPort: 3000
protocol: TCP
type: ClusterIP
Then fired off the manifest deployment
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ kubectl apply -f ./k8s.yaml -n fluidcal
configmap/app-config created
deployment.apps/fluid-calendar created
service/fluid-calendar created
I’ll make a DNS record
$ az account set --subscription "Pay-As-You-Go" && az network dns record-set a add-record -g idjdnsrg -z tpk.pw -a 75.73.224.240 -n fluidcal
{
"ARecords": [
{
"ipv4Address": "75.73.224.240"
}
],
"TTL": 3600,
"etag": "eacd455b-ca7d-4c9b-a119-ad514b441a9a",
"fqdn": "fluidcal.tpk.pw.",
"id": "/subscriptions/d955c0ba-13dc-44cf-a29a-8fed74cbb22d/resourceGroups/idjdnsrg/providers/Microsoft.Network/dnszones/tpk.pw/A/fluidcal",
"name": "fluidcal",
"provisioningState": "Succeeded",
"resourceGroup": "idjdnsrg",
"targetResource": {},
"trafficManagementProfile": {},
"type": "Microsoft.Network/dnszones/A"
}
I’ll now want to add the URL to my OAuth 2.0 client so Google will respond when we use it
Circling back to the deployment, I can see the pod is up
$ kubectl get po -n fluidcal
NAME READY STATUS RESTARTS AGE
postgres-postgresql-0 1/1 Running 0 94m
fluid-calendar-59687bdcb6-24dfx 1/1 Running 0 87m
I can add an ingress block now to my k8s.yaml file
... snip ...
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: azuredns-tpkpw
ingress.kubernetes.io/ssl-redirect: "true"
kubernetes.io/ingress.class: nginx
kubernetes.io/tls-acme: "true"
nginx.ingress.kubernetes.io/proxy-read-timeout: "3600"
nginx.ingress.kubernetes.io/proxy-send-timeout: "3600"
nginx.org/websocket-services: fluid-calendar
name: fluidcalingress
spec:
rules:
- host: fluidcal.tpk.pw
http:
paths:
- backend:
service:
name: fluid-calendar
port:
number: 80
path: /
pathType: ImplementationSpecific
tls:
- hosts:
- fluidcal.tpk.pw
secretName: fluidcal-tls
Then apply it
builder@DESKTOP-QADGF36:~/Workspaces/fluid-calendar$ kubectl apply -f ./k8s.yaml -n fluidcal
configmap/app-config unchanged
deployment.apps/fluid-calendar unchanged
service/fluid-calendar unchanged
ingress.networking.k8s.io/fluidcalingress created
When I see the cert satisfied
$ kubectl get cert -n fluidcal
NAME READY SECRET AGE
fluidcal-tls True fluidcal-tls 17m
I can now sign-in
However, it wouldn’t let me create the admin account
I actually fought this a bit. I tried adding more roles to the bespoke user:
builder@DESKTOP-QADGF36:~$ psql --host 127.0.0.1 -U postgres -d postgres -p 5433
Handling connection for 5433
Password for user postgres:
Handling connection for 5433
psql (12.20 (Ubuntu 12.20-0ubuntu0.20.04.1), server 17.4)
WARNING: psql major version 12, server major version 17.
Some psql features might not work.
Type "help" for help.
postgres=# GRANT USAGE ON SCHEMA public TO fluidcal;
GRANT
postgres=# GRANT CREATE ON SCHEMA public TO fluidcal;
GRANT
postgres=# ALTER DEFAULT PRIVILEGES IN SCHEMA public GRANT ALL ON TABLES TO fluidcal;
ALTER DEFAULT PRIVILEGES
postgres=# ALTER DEFAULT PRIVILEGES IN SCHEMA public GRANT ALL ON SEQUENCES TO fluidcal;
ALTER DEFAULT PRIVILEGES
postgres=# ALTER DEFAULT PRIVILEGES IN SCHEMA public GRANT ALL ON FUNCTIONS TO fluidcal;
ALTER DEFAULT PRIVILEGES
postgres=# ALTER SCHEMA public OWNER TO fluidcal;
ALTER SCHEMA
postgres=# \q
However, in the end, I had to fallback to the postgres superuser. Even then, it hung a couple times before it finally kicked in
$ kubectl logs fluid-calendar-59687bdcb6-ph4qk -n fluidcal
Waiting for database to be ready...
Connection to postgres-postgresql (10.43.142.42) 5432 port [tcp/postgresql] succeeded!
Database is ready!
Generating Prisma Client...
Prisma schema loaded from prisma/schema.prisma
✔ Generated Prisma Client (v6.3.1) to ./node_modules/@prisma/client in 3.31s
Start by importing your Prisma Client (See: https://pris.ly/d/importing-client)
Tip: Interested in query caching in just a few lines of code? Try Accelerate today! https://pris.ly/tip-3-accelerate
warn Versions of prisma@6.5.0 and @prisma/client@6.3.1 don't match.
This might lead to unexpected behavior.
Please make sure they have the same version.
npm notice
npm notice New major version of npm available! 10.8.2 -> 11.2.0
npm notice Changelog: https://github.com/npm/cli/releases/tag/v11.2.0
npm notice To update run: npm install -g npm@11.2.0
npm notice
Running database migrations...
Prisma schema loaded from prisma/schema.prisma
Datasource "db": PostgreSQL database "fluidcal", schema "public" at "postgres-postgresql:5432"
34 migrations found in prisma/migrations
Applying migration `20250223154645_init`
Applying migration `20250224085326_add_logging_system`
Applying migration `20250225165028_add_postponed_until`
Applying migration `20250225201435_add_completed_at_to_tasks`
Applying migration `20250227022935_add_caldav_support`
Applying migration `20250305163745_add_all_settings`
Applying migration `20250305165916_add_role_to_user`
Applying migration `20250305211517_add_user_id_to_all_models`
Applying migration `20250305212848_add_public_signup_to_system_settings`
Applying migration `20250308142038_add_waitlist_model`
Applying migration `20250308200254_add_waitlist_name`
Applying migration `20250309034029_enhanced_waitlist`
Applying migration `20250309034054_update_waitlist_entries`
Applying migration `20250309155528_add_last_position`
Applying migration `20250310205309_update_tag_unique_constraint`
Applying migration `20250311093456_add_pending_waitlist`
Applying migration `20250311150536_allow_multiple_users_same_account`
Applying migration `20250311151155_make_external_list_id_unique_per_project`
Applying migration `20250311231626_add_job_records`
Applying migration `20250314121833_update_email_templates`
Applying migration `20250314161820_add_lifetime_interest_flag`
Applying migration `20250319140154_add_task_start_date`
Applying migration `20250320211949_task_sync_schema`
Applying migration `20250321124208_add_disable_homepage`
Applying migration `20250321141735_add_account_id_to_task_provider`
Applying migration `20250321141823_add_default_project_id_to_task_provider`
Applying migration `20250321154854_add_task_change_tracking`
Applying migration `20250324120310_remove_outlook_task_list_mapping`
Applying migration `20250324122710_remove_cascade_on_task_change`
Applying migration `20250324123219_make_taskid_nullable_in_taskchange`
Applying migration `20250325010020_add_resend_api_key`
Applying migration `20250325013837_add_password_reset`
Applying migration `20250325015626_add_queue_notifications_enabled`
Applying migration `20250325020728_add_daily_email_setting`
The following migration(s) have been applied:
migrations/
└─ 20250223154645_init/
└─ migration.sql
└─ 20250224085326_add_logging_system/
└─ migration.sql
└─ 20250225165028_add_postponed_until/
└─ migration.sql
└─ 20250225201435_add_completed_at_to_tasks/
└─ migration.sql
└─ 20250227022935_add_caldav_support/
└─ migration.sql
└─ 20250305163745_add_all_settings/
└─ migration.sql
└─ 20250305165916_add_role_to_user/
└─ migration.sql
└─ 20250305211517_add_user_id_to_all_models/
└─ migration.sql
└─ 20250305212848_add_public_signup_to_system_settings/
└─ migration.sql
└─ 20250308142038_add_waitlist_model/
└─ migration.sql
└─ 20250308200254_add_waitlist_name/
└─ migration.sql
└─ 20250309034029_enhanced_waitlist/
└─ migration.sql
└─ 20250309034054_update_waitlist_entries/
└─ migration.sql
└─ 20250309155528_add_last_position/
└─ migration.sql
└─ 20250310205309_update_tag_unique_constraint/
└─ migration.sql
└─ 20250311093456_add_pending_waitlist/
└─ migration.sql
└─ 20250311150536_allow_multiple_users_same_account/
└─ migration.sql
└─ 20250311151155_make_external_list_id_unique_per_project/
└─ migration.sql
└─ 20250311231626_add_job_records/
└─ migration.sql
└─ 20250314121833_update_email_templates/
└─ migration.sql
└─ 20250314161820_add_lifetime_interest_flag/
└─ migration.sql
└─ 20250319140154_add_task_start_date/
└─ migration.sql
└─ 20250320211949_task_sync_schema/
└─ migration.sql
└─ 20250321124208_add_disable_homepage/
└─ migration.sql
└─ 20250321141735_add_account_id_to_task_provider/
└─ migration.sql
└─ 20250321141823_add_default_project_id_to_task_provider/
└─ migration.sql
└─ 20250321154854_add_task_change_tracking/
└─ migration.sql
└─ 20250324120310_remove_outlook_task_list_mapping/
└─ migration.sql
└─ 20250324122710_remove_cascade_on_task_change/
└─ migration.sql
└─ 20250324123219_make_taskid_nullable_in_taskchange/
└─ migration.sql
└─ 20250325010020_add_resend_api_key/
└─ migration.sql
└─ 20250325013837_add_password_reset/
└─ migration.sql
└─ 20250325015626_add_queue_notifications_enabled/
└─ migration.sql
└─ 20250325020728_add_daily_email_setting/
└─ migration.sql
All migrations have been successfully applied.
Starting the application...
▲ Next.js 15.2.3
- Local: http://fluid-calendar-59687bdcb6-ph4qk:3000
- Network: http://fluid-calendar-59687bdcb6-ph4qk:3000
✓ Starting...
✓ Ready in 1070ms
However, it’s now up and running
As before, I can setup the Google Client ID and Secret and authorize this instance.
After which I can easily sync calendars
One thing I have yet to test is syncing back to Google.
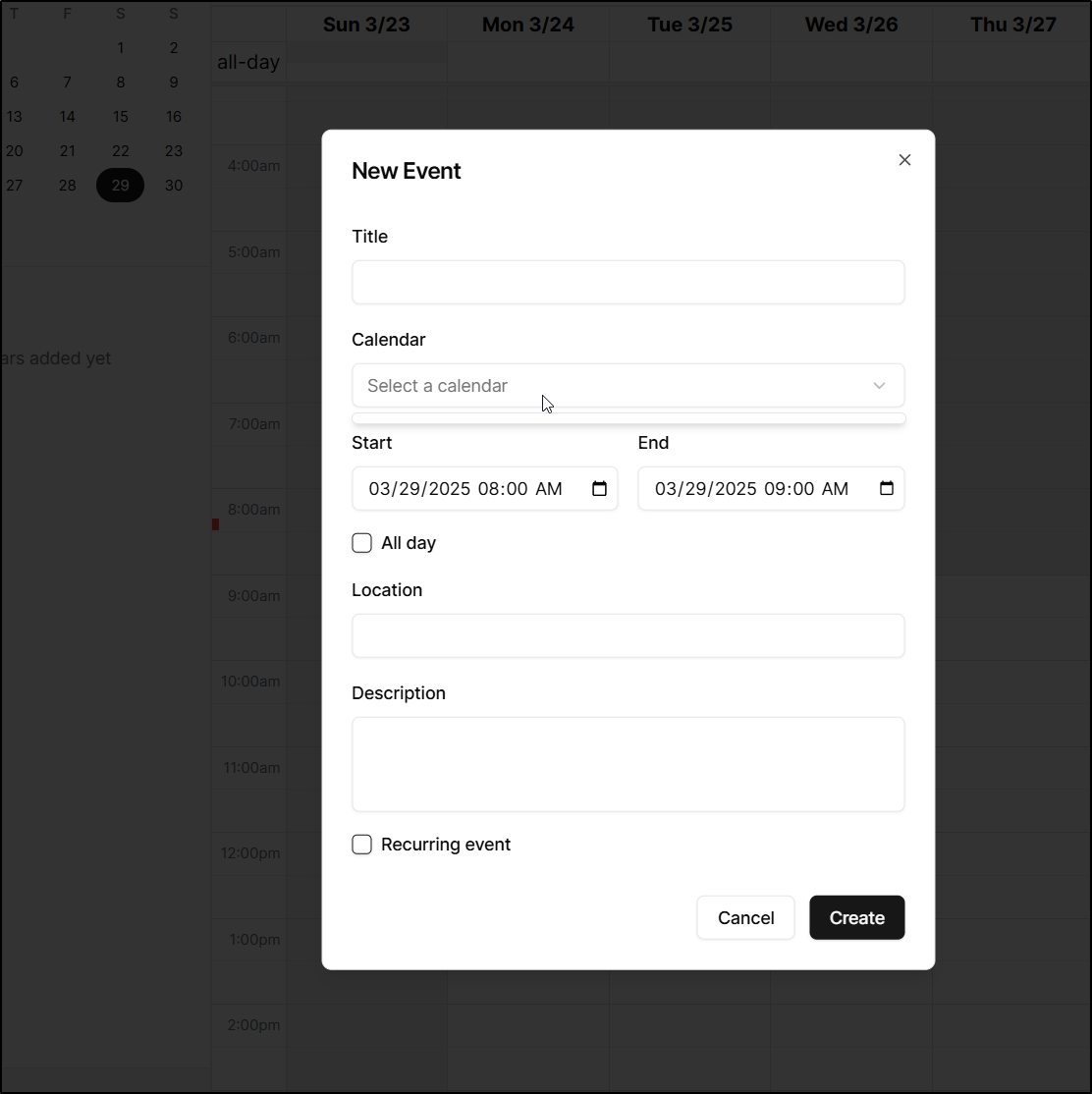
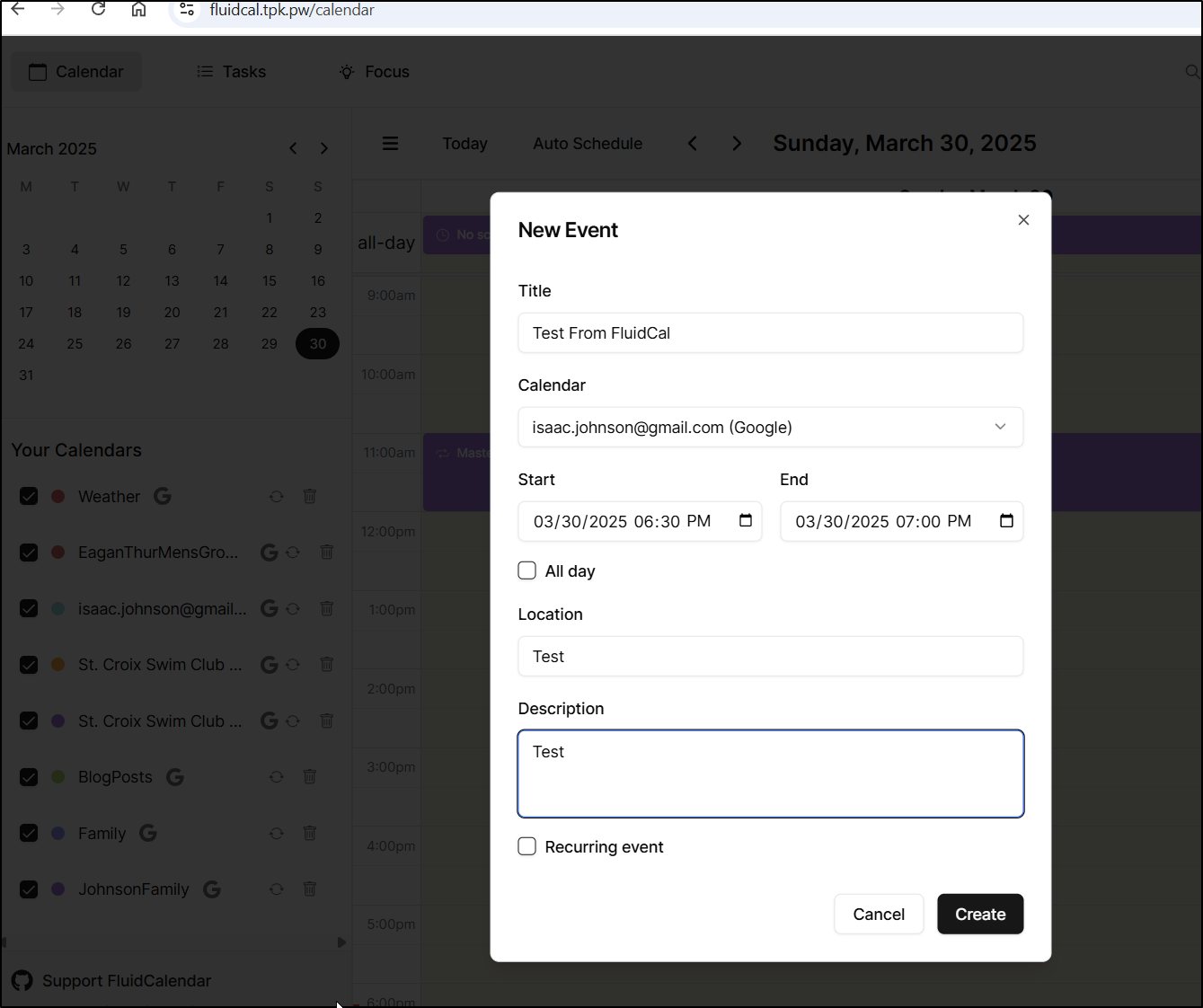
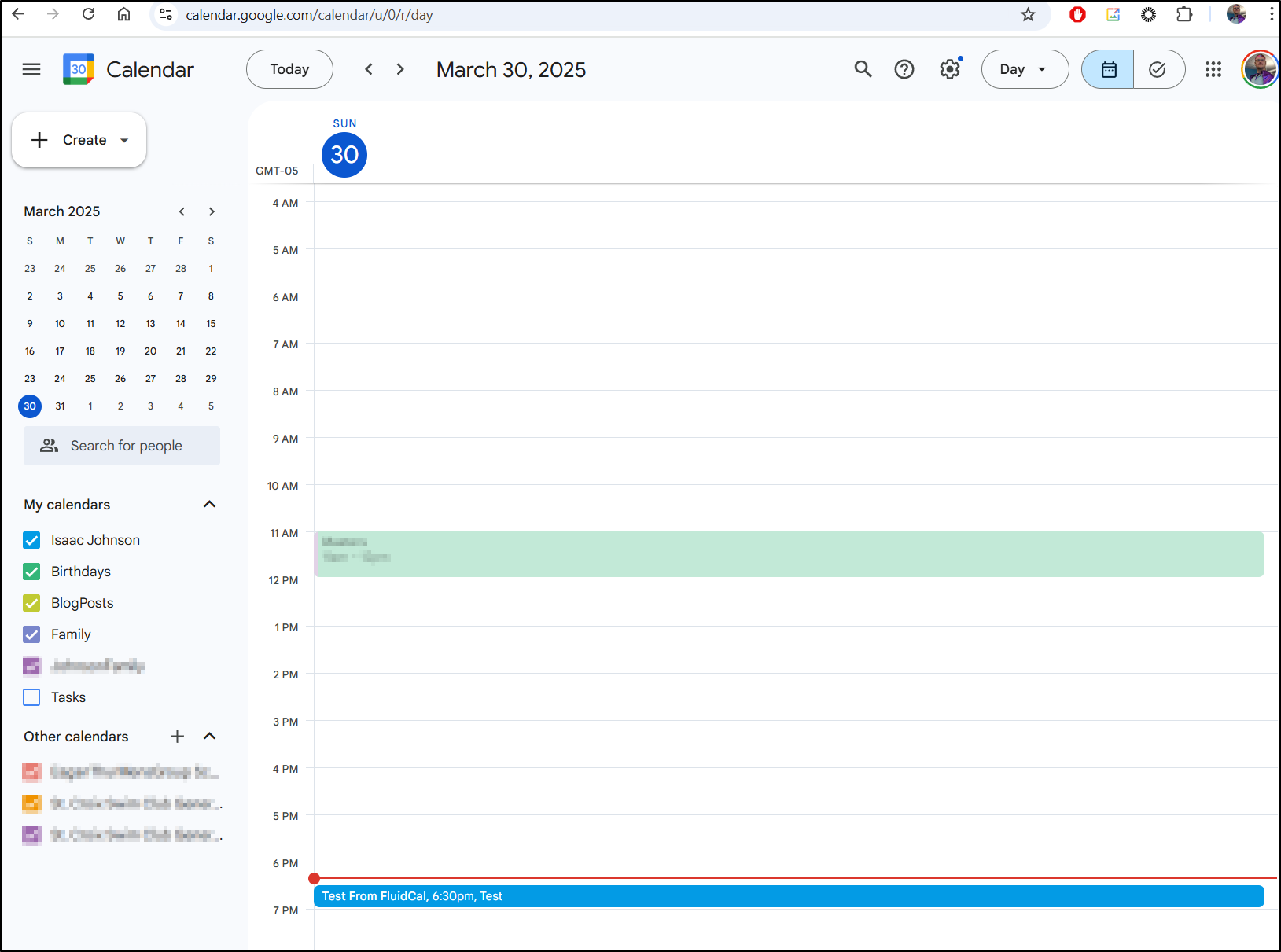
Here I’ll create a new test event
And it was nearly instant that I saw it show up on Google Cal (and then buzz my watch with a 15m alert)
I can also verify removing it works just as well.
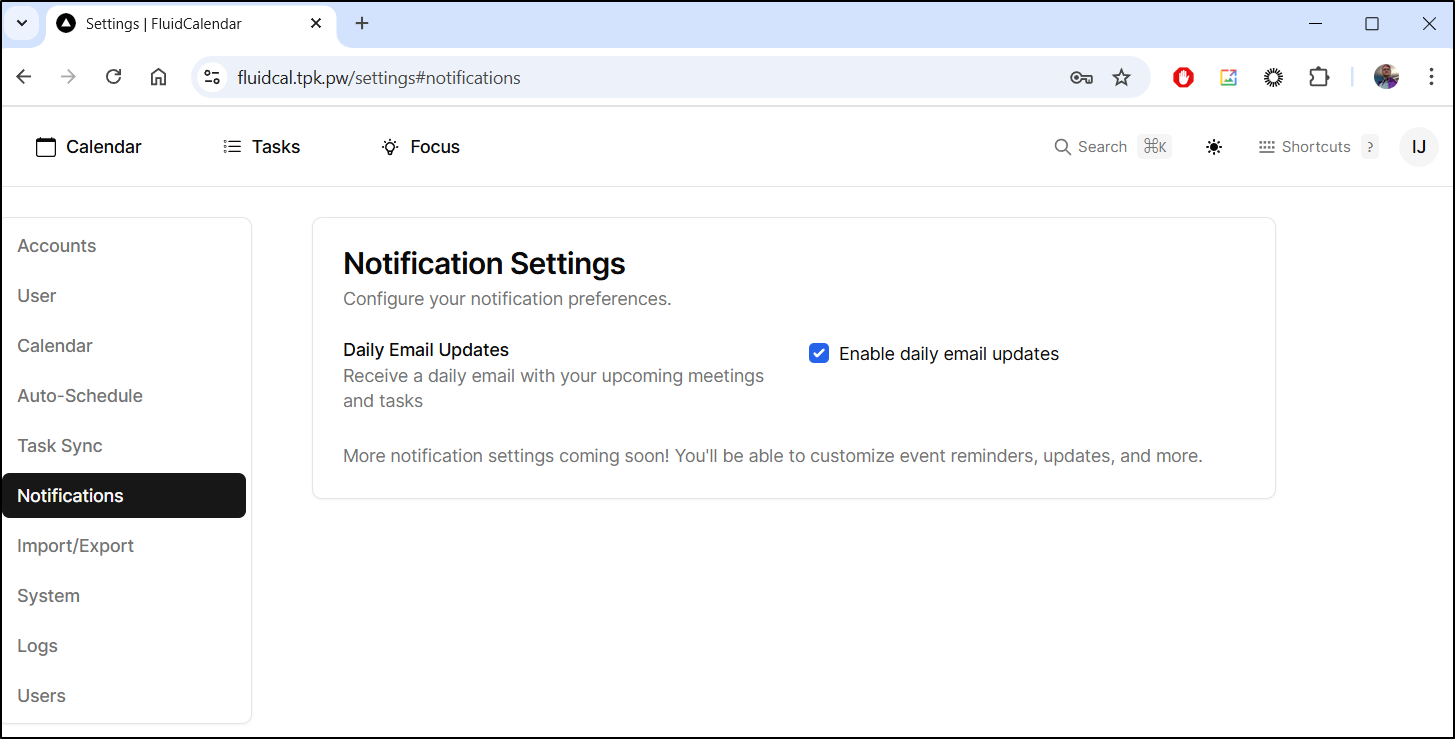
I have daily updates enabled so I’ll just need to circle back in a day to see if they are working
Microsoft AAD (Entra ID) permissions
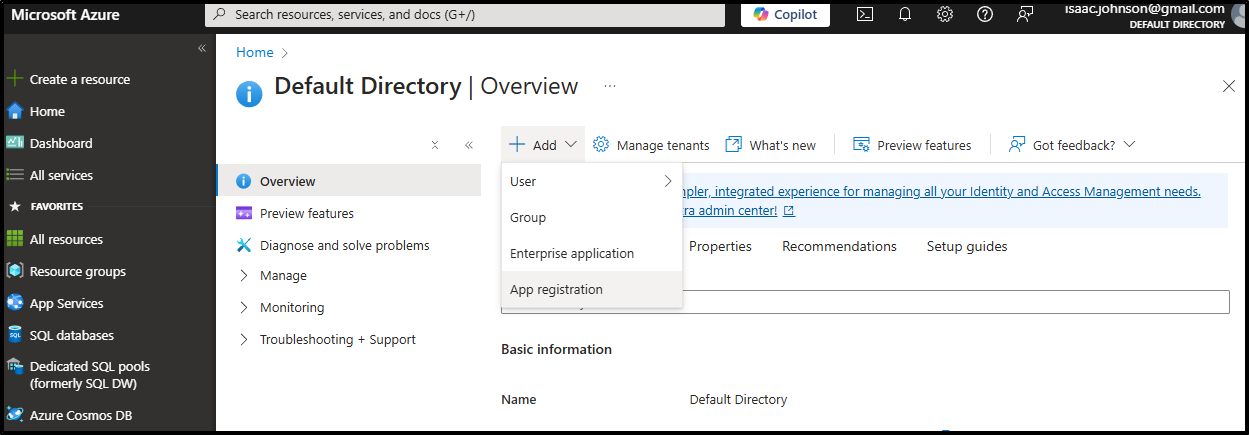
Let’s start with adding a new Service Principal (App Registration)
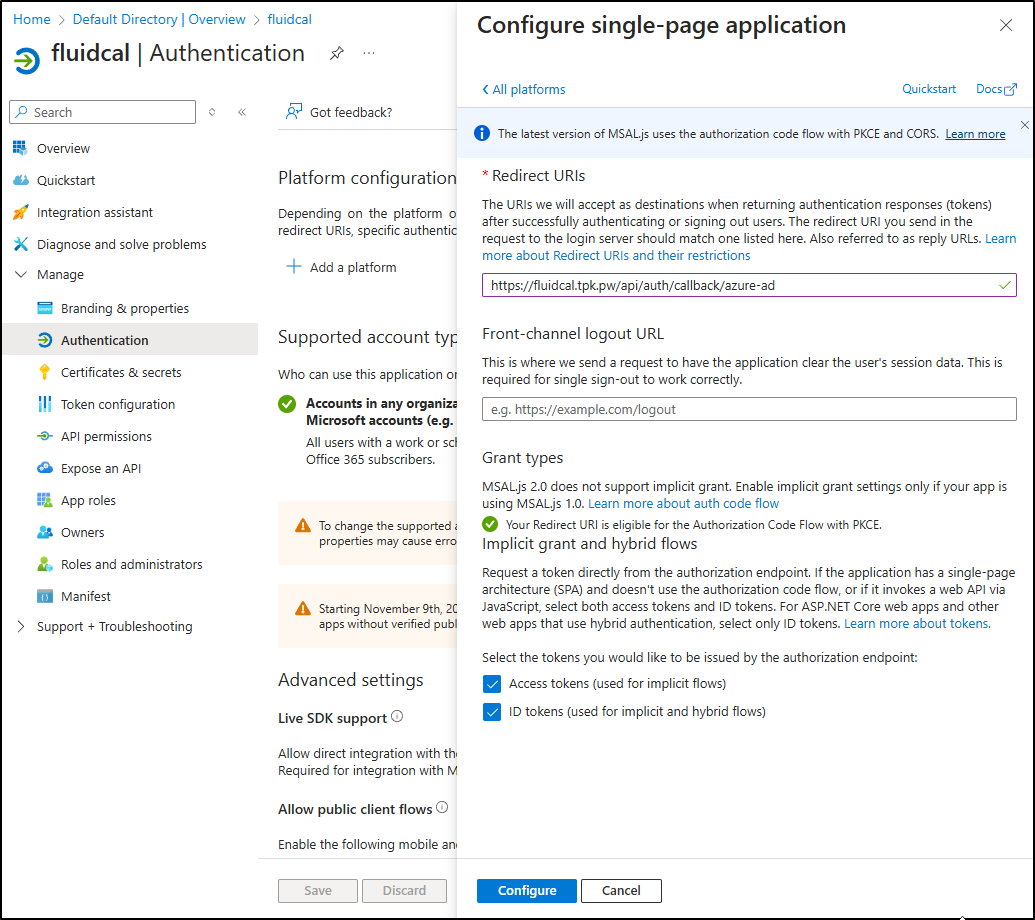
I’m probably fine single-tenant, but in case I crossed Tenants for calendaring, i opted for the wider scope. I also set the OAuth return URL
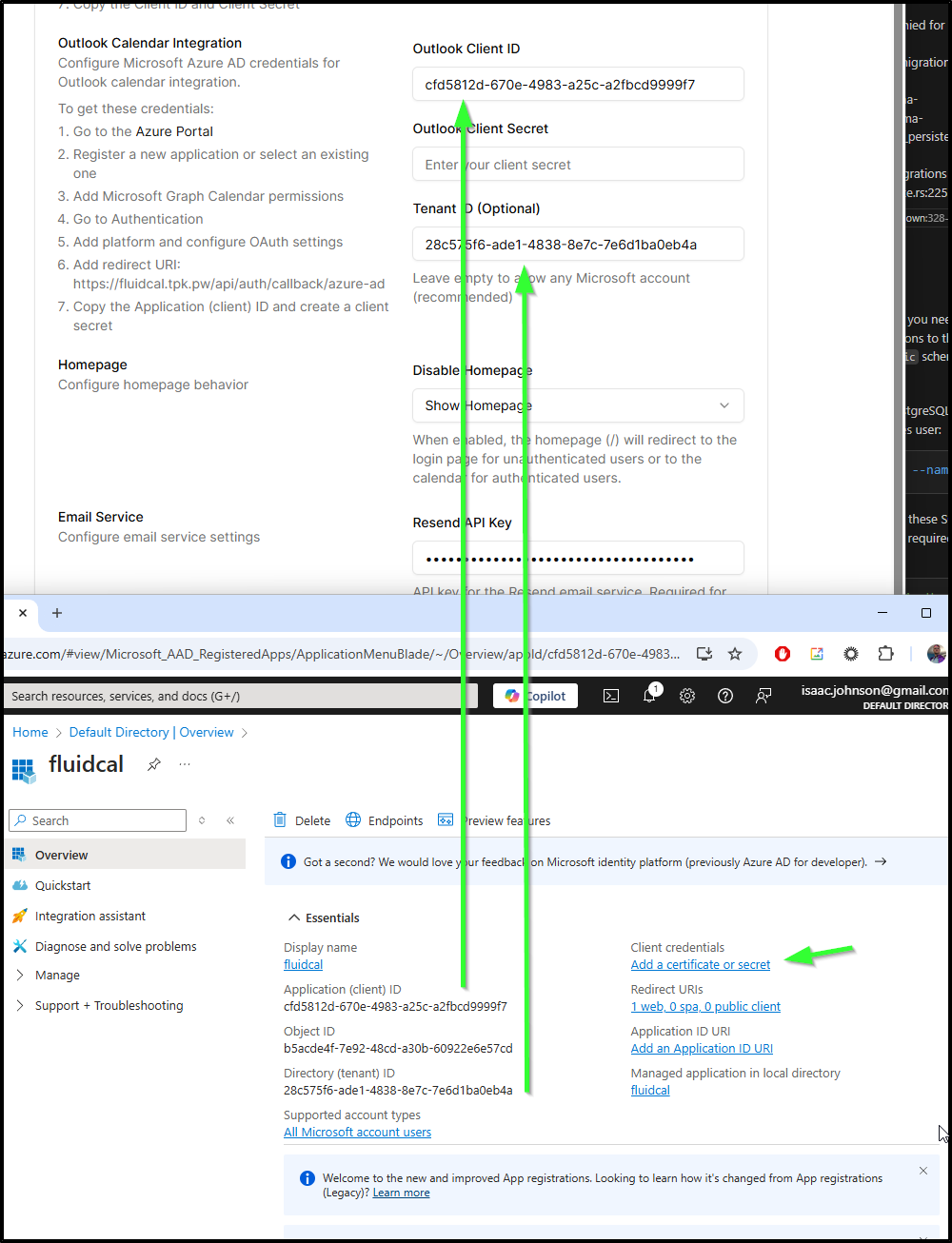
Once created, I copied over the values for the Client ID and Tenant, then created a Client secret I could use
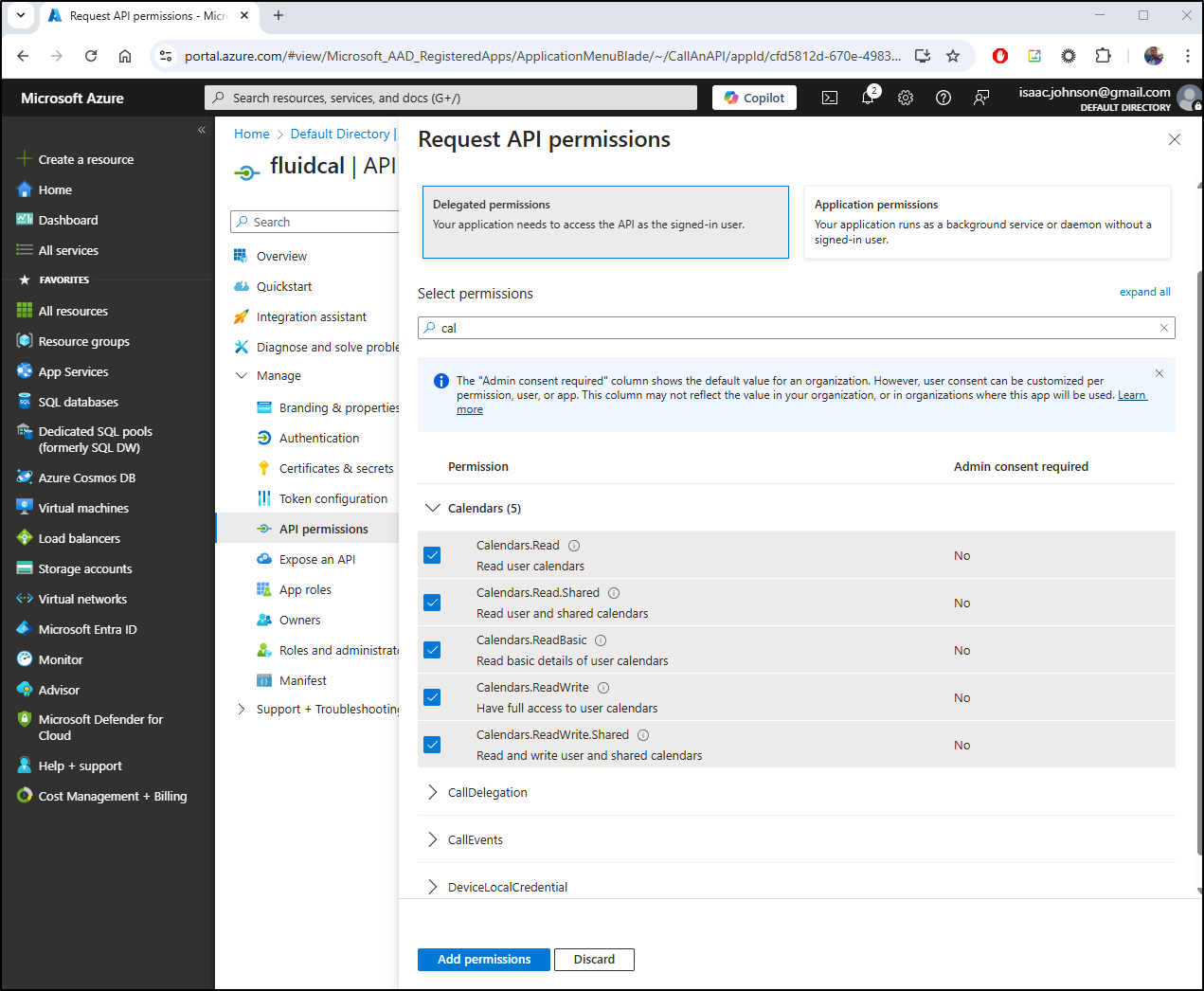
Lastly, I opted to expand permissions to full Microsoft Graph for calendar operations
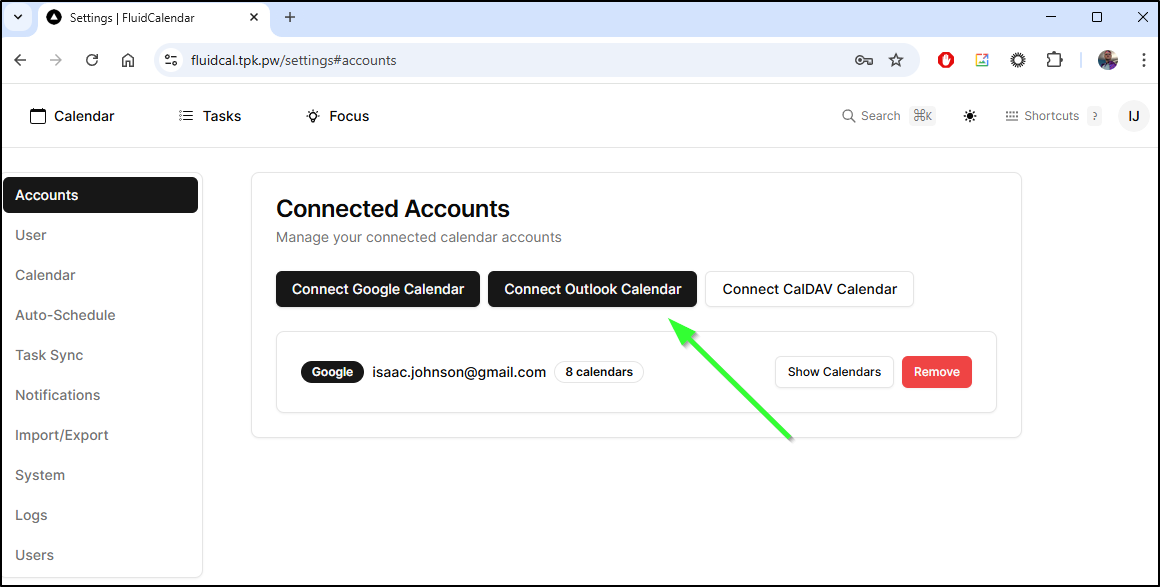
I’ll now try to add an Outlook Calendar
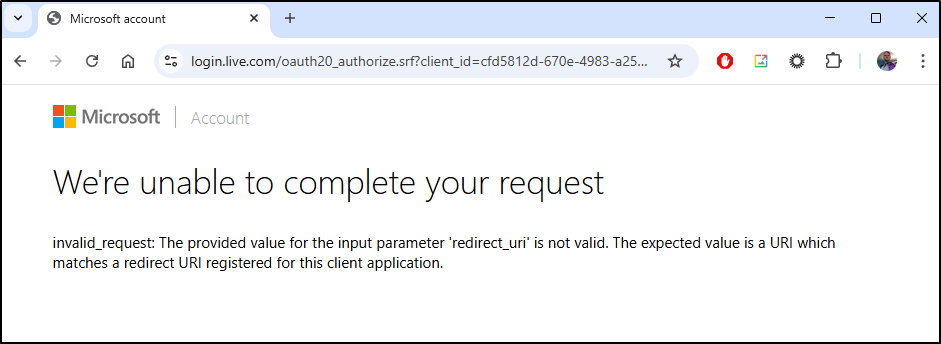
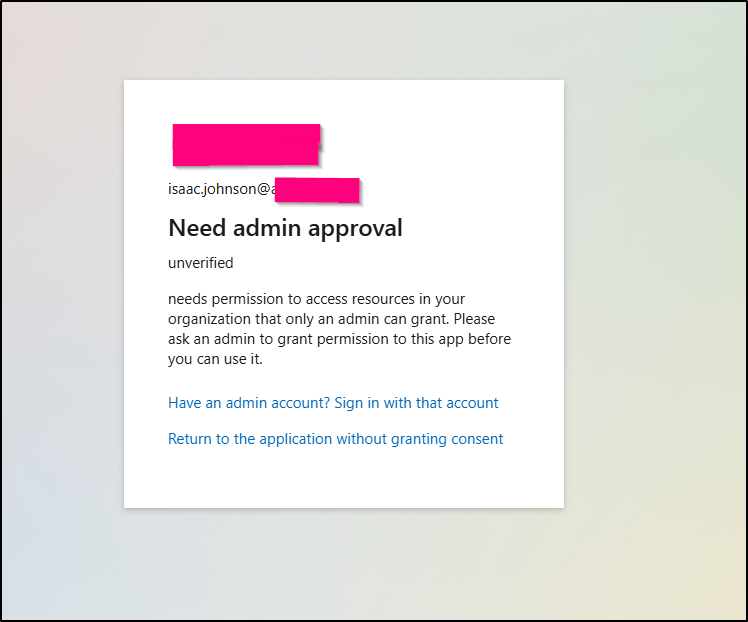
I tried to use it with a business account, but was rejected (not surprised). However, trying to use it with a personal one showed an error:
I tried deleting and re-adding
But after searching and parsing the error (invalid_request: The provided value for the input parameter ‘redirect_uri’ is not valid. The expected value is a URI which matches a…)
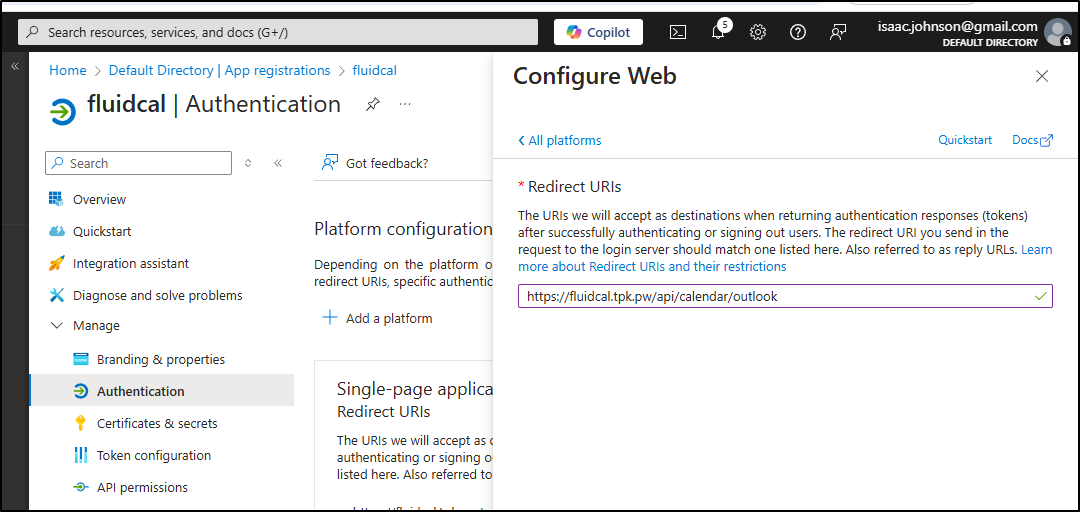
I realized the URL for redirect did not match the system message in Fluid Calendar (https://fluidcal.tpk.pw/api/auth/callback/azure-ad)/
I used instead https://fluidcal.tpk.pw/api/calendar/outlook
This time it worked
I can now add my O365 calendars
As before, it would not work with my work account (which is pretty locked down)
WPS Office
I saw WPS-Office from just looking around at LinuxServer’s Docker Hub page.
It can be launched with
docker run -d \
--name=wps-office \
--security-opt seccomp=unconfined `#optional` \
-e PUID=1000 \
-e PGID=1000 \
-e TZ=Etc/UTC \
-p 3000:3000 \
-p 3001:3001 \
-v /path/to/config:/config \
--shm-size="1gb" \
--restart unless-stopped \
lscr.io/linuxserver/wps-office:latest
That can easily be turned into a Kubernetes YAML Manifest:
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: wps-config
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: wps-office
labels:
app: wps-office
spec:
replicas: 1
selector:
matchLabels:
app: wps-office
template:
metadata:
labels:
app: wps-office
spec:
containers:
- name: wps-office
image: lscr.io/linuxserver/wps-office:latest
env:
- name: PUID
value: "1000"
- name: PGID
value: "1000"
- name: TZ
value: "Etc/UTC"
ports:
- containerPort: 3000
name: http
- containerPort: 3001
name: extra
volumeMounts:
- name: wps-config
mountPath: /config
resources:
limits:
memory: "2Gi"
requests:
memory: "1Gi"
securityContext:
seccompProfile:
type: Unconfined
volumes:
- name: wps-config
persistentVolumeClaim:
claimName: wps-config
---
apiVersion: v1
kind: Service
metadata:
name: wps-office
spec:
selector:
app: wps-office
ports:
- port: 3000
targetPort: 3000
name: http
- port: 3001
targetPort: 3001
name: extra
type: ClusterIP
Looking at the docs, I know I’ll want to change the username and password as well:
env:
- name: PUID
value: "1000"
- name: PGID
value: "1000"
- name: TZ
value: "US/Central"
- name: CUSTOM_USER
value: "myuser"
- name: PASSWORD
value: "mypass"
I’ll apply
$ kubectl apply -f ./wpoffice.k8s.yaml
persistentvolumeclaim/wps-config created
deployment.apps/wps-office created
service/wps-office created
Once I saw the pod running
$ kubectl get po -l app=wps-office
NAME READY STATUS RESTARTS AGE
wps-office-55ccbf8cd4-vww2l 0/1 ContainerCreating 0 43s
$ kubectl get po -l app=wps-office
NAME READY STATUS RESTARTS AGE
wps-office-55ccbf8cd4-vww2l 1/1 Running 0 2m14s
I can now port-forward
$ kubectl port-forward svc/wps-office 3033:3000
Forwarding from 127.0.0.1:3033 -> 3000
Forwarding from [::1]:3033 -> 3000
Handling connection for 3033
Handling connection for 3033
Handling connection for 3033
Handling connection for 3033
Handling connection for 3033
Handling connection for 3033
And login with the basic auth to see the WPS Office suite
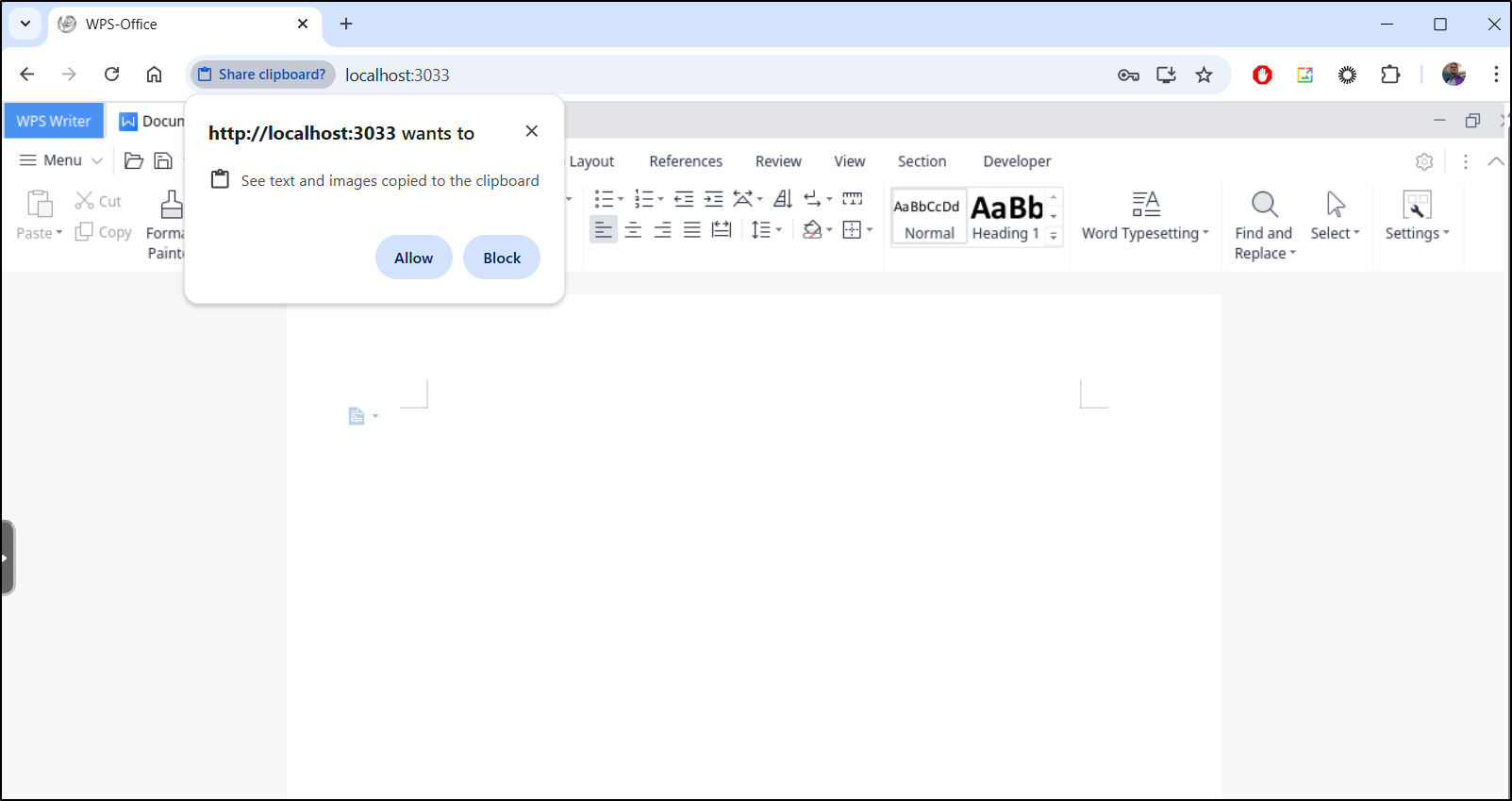
I found I needed to right-click for “paste-special” to get images to paste, but then they worked just fine
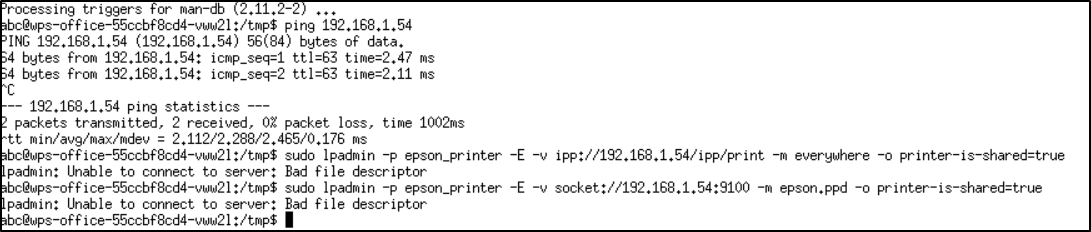
I was really hoping to get local printing working with cups
sudo lpadmin -p epson_printer \
-E \
-v ipp://192.168.1.54/ipp/print \
-m everywhere \
-o printer-is-shared=true
But unfortunately, it just gives errors.
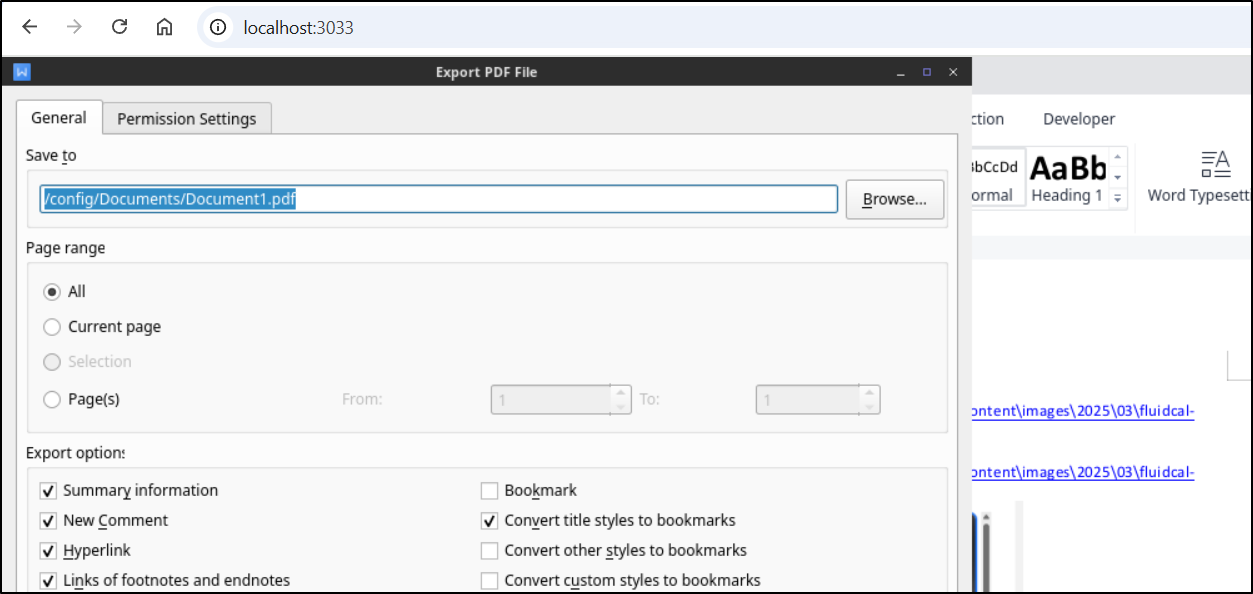
That said, we can save our files to PDF (/config/Documents/Document1.pdf)
However, I refused to give up.
I found this script from Amith Chandrappa.
I applied the commented fix for the base64 attachments
#!/bin/bash
# Author: Amith Chandrappa
# Usage
# Options:
# -t: To Emails, Separated by ";"
# -c: CC Emails, Separated by ";"
# -b: BCC Emails, Separated by ";"
# -s: Subject
# -o: Email body
# -a: Attachment Files, Separated by ";"
#
# Example:
# sh sendEmail.sh
# -t 'to1@gmail.com;to2@gmail.com'
# -c 'cc1@gmail.com;cc2@gmail.com'
# -b 'bcc1@gmail.com;bcc2@gmail.com'
# -s 'FINAL SCRIPT'
# -o '<p>Email body goes here</p>'
# -a '/tmp/test.sh;/tmp/test2.sh'
# Your Sendgrid API Key
SENDGRID_API_KEY="<YOUR API KEY>"
FROM_NAME="<FROM NAME>"
FROM_EMAIL="<FROM EMAIL ADDRESS>"
# Get the arguments
while getopts t:c:b:s:o:a: flag
do
case "${flag}" in
t) to=${OPTARG};;
c) cc=${OPTARG};;
b) bcc=${OPTARG};;
s) subject=${OPTARG};;
o) body=${OPTARG};;
a) attachments=${OPTARG};;
esac
done
# Start building the JSON
sendGridJson="{\"personalizations\": [{";
# Convert the String to Array, with the delimiter as ";"
IFS='; ' read -r -a to_array <<< "$to"
IFS='; ' read -r -a cc_array <<< "$cc"
IFS='; ' read -r -a bcc_array <<< "$bcc"
IFS='; ' read -r -a attachments_array <<< "$attachments"
if [ ${#to_array[@]} != 0 ]
then
sendGridJson="${sendGridJson} \"to\": ["
for email in "${to_array[@]}"
do
sendGridJson="${sendGridJson} {\"email\": \"$email\"},"
done
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
sendGridJson="${sendGridJson} ],"
if [ ${#cc_array[@]} == 0 ] && [ ${#bcc_array[@]} == 0 ]
then
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
fi
fi
if [ ${#cc_array[@]} != 0 ]
then
sendGridJson="${sendGridJson} \"cc\": ["
for email in "${cc_array[@]}"
do
sendGridJson="${sendGridJson} {\"email\": \"$email\"},"
done
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
sendGridJson="${sendGridJson} ],"
if [ ${#bcc_array[@]} == 0 ]
then
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
fi
fi
if [ ${#bcc_array[@]} != 0 ]
then
sendGridJson="${sendGridJson} \"bcc\": ["
for email in "${bcc_array[@]}"
do
sendGridJson="${sendGridJson} {\"email\": \"$email\"},"
done
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
sendGridJson="${sendGridJson} ]"
fi
sendGridJson="${sendGridJson} }],\"from\": {\"email\": \"${FROM_EMAIL}\",\"name\": \"${FROM_NAME}\"},\"subject\":\"${subject}\",\"content\": [{\"type\": \"text/html\",\"value\": \"${body}\"}],"
if [ ${#attachments_array[@]} != 0 ]
then
sendGridJson="${sendGridJson} \"attachments\": ["
for attachment in "${attachments_array[@]}"
# Converting the File Content to Base64
# For OSX use base64 <fileName>
# For linux use base64 -w 0 <fileName>
do
# base64_content=$(base64 -w 0${attachment})
# corrected:
base64_content=$(base64 -w 0 < ${attachment})
fileName="$(basename $attachment)"
sendGridJson="${sendGridJson} {\"content\": \"${base64_content}\",\"type\": \"text/plain\",\"filename\": \"${fileName}\"},"
done
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
sendGridJson="${sendGridJson} ]"
else
sendGridJson=`echo ${sendGridJson} | sed 's/.$//'`
fi
sendGridJson="${sendGridJson} }"
#Generate a Random File to hole the POST data
tfile=$(mktemp /tmp/sendgrid.XXXXXXXXX)
echo $sendGridJson > $tfile
# Send the http request to SendGrid
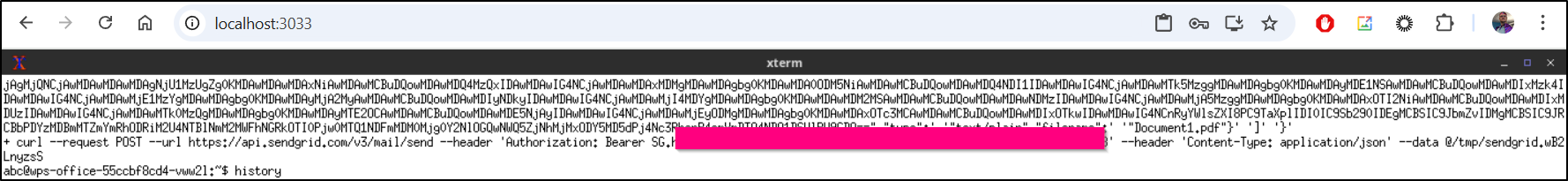
curl --request POST \
--url https://api.sendgrid.com/v3/mail/send \
--header 'Authorization: Bearer '$SENDGRID_API_KEY \
--header 'Content-Type: application/json' \
--data @$tfile
In copying and pasting over, i did have some issues with windows new lines (\r) so I used dos2unix to fix.
But then I was able to run the command
And you can see it printed (the background is just because the kids kick of endless colouring sheets so i grabbed some scrap paper for testing)
Presentations
Let’s create a Presentation instead. I’ll click new Document and select “Presentation”
Here you can see an interface like most office apps that have Presentations. We can do things like change layouts
Or select from a handful of themes
I was curious how easy it might be to copy in a PPTX to continue work on it.
I’ll take a talk I have in 2023
builder@DESKTOP-QADGF36:/$ aws s3 ls s3://freshbrewed.science/OSN2023/
2023-05-26 05:28:28 0
2023-05-26 05:29:49 1077279124 OSN2023-Trimmed.mp4
2023-05-26 05:29:49 81429143 OSN2023-Trimmed.pptx
builder@DESKTOP-QADGF36:/$ aws s3 cp s3://freshbrewed.science/OSN2023/OSN2023-Trimmed.pptx /tmp/OSN2023-Trimmed.pptx
download: s3://freshbrewed.science/OSN2023/OSN2023-Trimmed.pptx to tmp/OSN2023-Trimmed.pptx
Then copy to the container
builder@DESKTOP-QADGF36:/$ kubectl cp /tmp/OSN2023-Trimmed.pptx wps-office-55ccbf8cd4-vww2l:/config/Documents/OSN2023-Trimmed.pptx
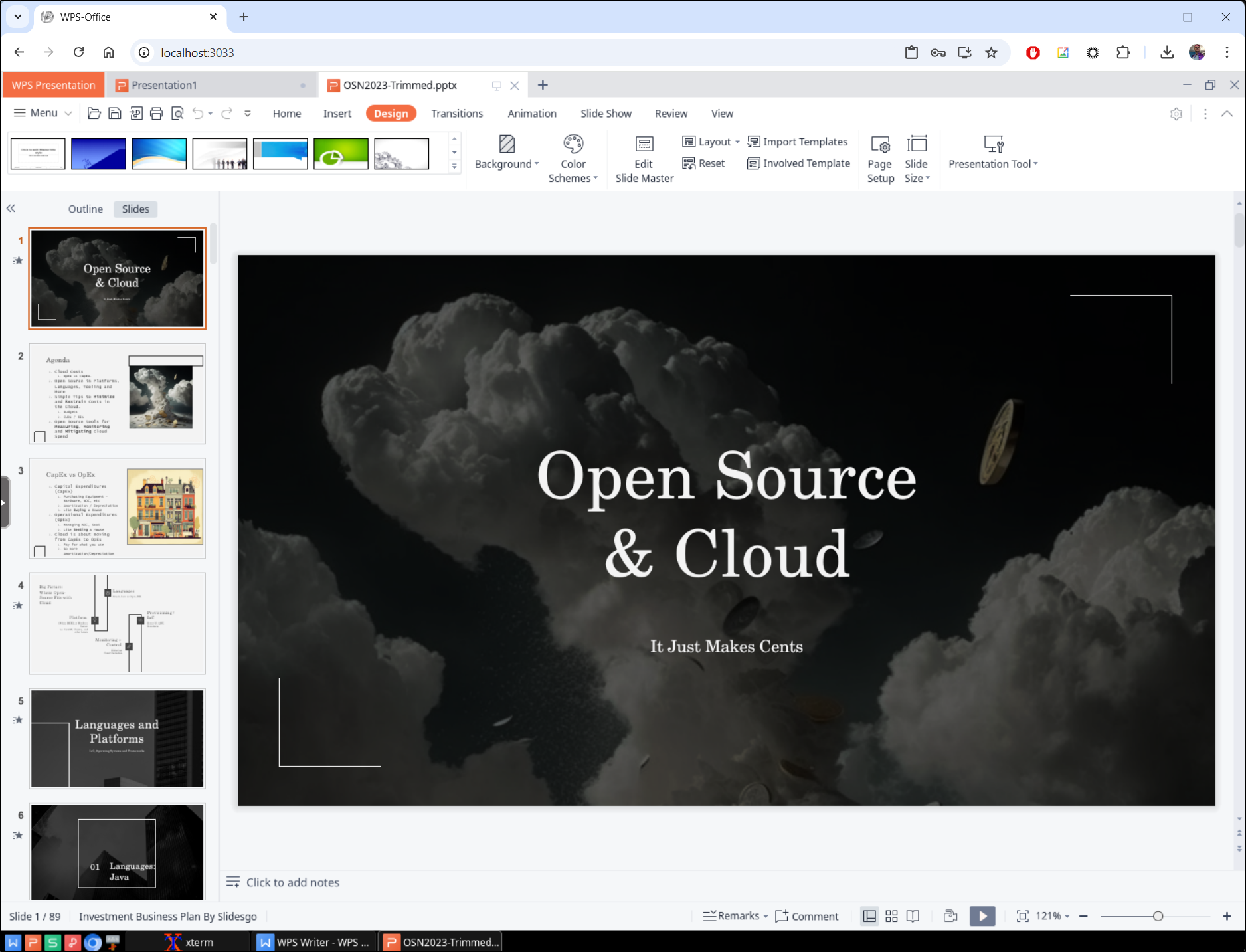
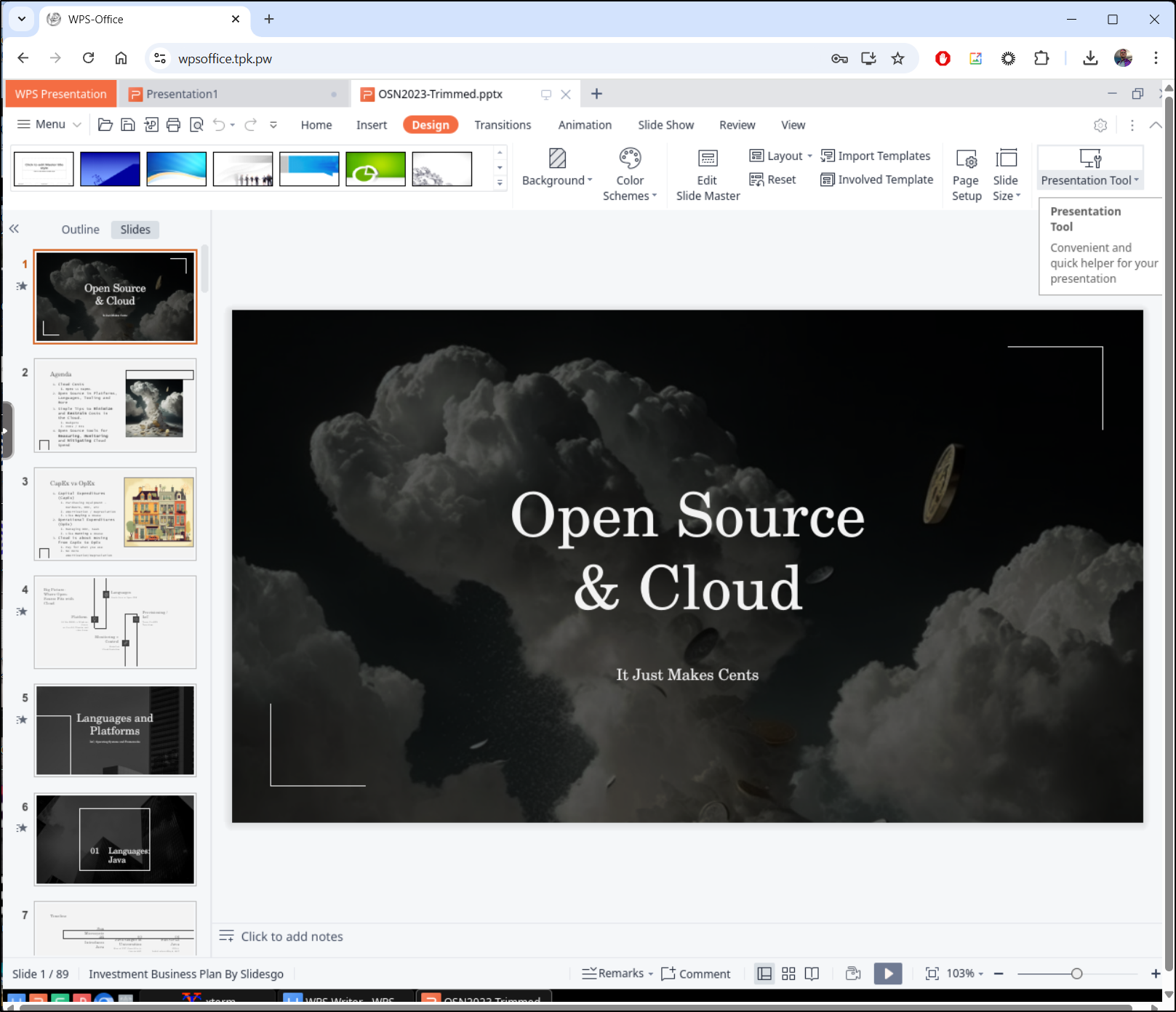
I can now open it
and indeed, see the full presentation
Ingress
Like above, let’s create a route there via Azure DNS
$ az account set --subscription "Pay-As-You-Go" && az network dns record-set a add-record -g idjdnsrg -z tpk.pw -a 75.73.224.240 -n wpsoffice
{
"ARecords": [
{
"ipv4Address": "75.73.224.240"
}
],
"TTL": 3600,
"etag": "51d4a3dc-dbfb-4c33-ad54-3527445b9805",
"fqdn": "wpsoffice.tpk.pw.",
"id": "/subscriptions/d955c0ba-13dc-44cf-a29a-8fed74cbb22d/resourceGroups/idjdnsrg/providers/Microsoft.Network/dnszones/tpk.pw/A/wpsoffice",
"name": "wpsoffice",
"provisioningState": "Succeeded",
"resourceGroup": "idjdnsrg",
"targetResource": {},
"trafficManagementProfile": {},
"type": "Microsoft.Network/dnszones/A"
}
Then create and apply an ingress
$ cat ./wpsoffice.ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: azuredns-tpkpw
ingress.kubernetes.io/ssl-redirect: "true"
kubernetes.io/ingress.class: nginx
kubernetes.io/tls-acme: "true"
nginx.ingress.kubernetes.io/proxy-read-timeout: "3600"
nginx.ingress.kubernetes.io/proxy-send-timeout: "3600"
nginx.org/websocket-services: wps-office
name: wpsofficeingress
spec:
rules:
- host: wpsoffice.tpk.pw
http:
paths:
- backend:
service:
name: wps-office
port:
number: 3000
path: /
pathType: ImplementationSpecific
tls:
- hosts:
- wpsoffice.tpk.pw
secretName: wpsoffice-tls
$ kubectl apply -f ./wpsoffice.ingress.yaml
ingress.networking.k8s.io/wpsofficeingress created
Once the cert is satisfied
$ kubectl get cert wpsoffice-tls
NAME READY SECRET AGE
wpsoffice-tls True wpsoffice-tls 81s
Logging in shows us right where we left off!
This actually gave me an idea. I could just login to a presentation laptop and use a phone for a remote, or a second laptop for a remote
You can see the firefox window moves alongside the presentation.
Sheets
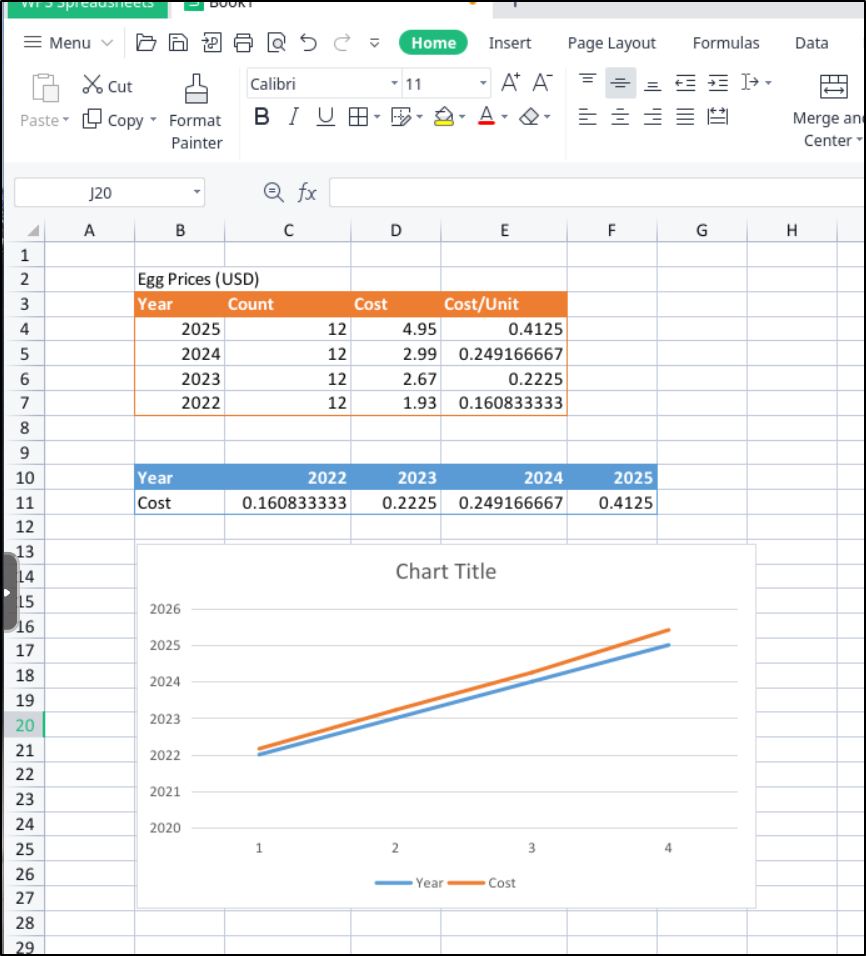
I did test sheets/excel. It worked fine, though the graph making wasn’t the easiest. I had to make a pivot table to get the graph to show up.
Summary
Today we setup two pretty nice Office/Productivity related apps. The first was FluidCalender which worked great to sync with Google and Outlook. However, in my testing, it worked fine for my own O365 but not a more locked down corporate account. I also would have wished for it to work without needing to tie it to a Google calendar. That said, I used it throughout the day to expose my home calendar at work which was nice.
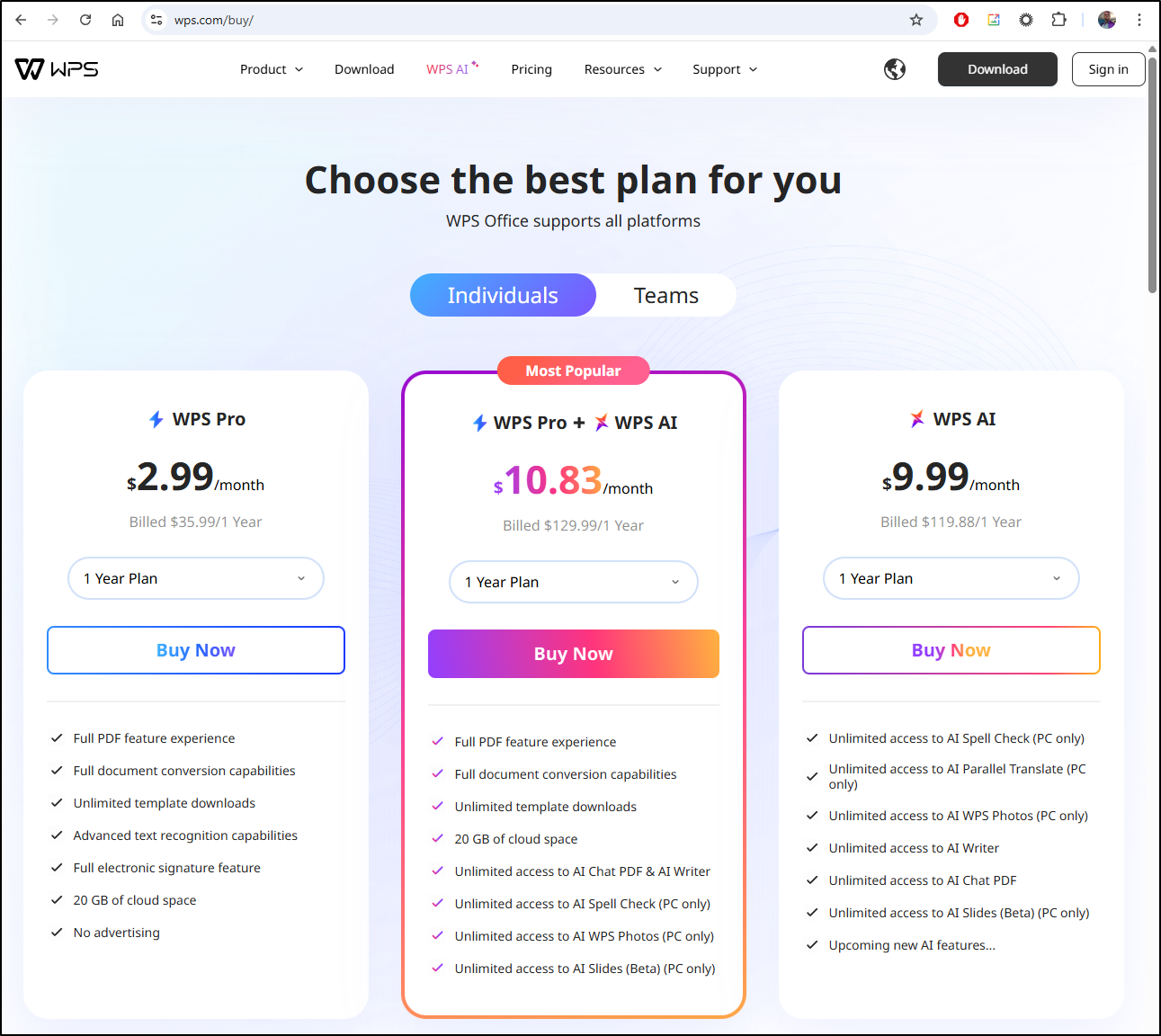
The other tool was a containerized instance of WPS-Office. It is the packed Open-Source version of WPS Office tool which now has “AI” features galore. If you wanted to download and buy the commercial instance of WSP Office, the costs are about US$36/year and include some cloud storage as well
Well, sort of. If you want the “AI”, which I imagine is pushed a bit, that is US$10.83/mo
That is a bit of a challenge when we add “AI” to products - someone has to pay for the constant backend compute.
Overall, I find it pretty handy and as the /config directory on the containerized Open-Source version is on a safer PVC, I don’t mind saving files locally and pulling them as desired.
For instance, we could create a cron job that would back this up for us
#!/bin/bash
# filepath: /usr/local/bin/backup-wps-docs.sh
# Set variables
BACKUP_DIR="/mnt/backups/wps-docs"
NAMESPACE="default"
DATE=$(date +%Y%m%d)
# Create backup directory if it doesn't exist
mkdir -p "${BACKUP_DIR}"
# Get the pod name
POD_NAME=$(kubectl get pod -n ${NAMESPACE} -l app=wps-office -o jsonpath='{.items[0].metadata.name}')
if [ -z "${POD_NAME}" ]; then
echo "No WPS Office pod found"
exit 1
fi
# Create temp directory
TMP_DIR=$(mktemp -d)
echo "Created temp directory: ${TMP_DIR}"
# Copy files from pod
echo "Copying files from pod ${POD_NAME}..."
kubectl cp ${NAMESPACE}/${POD_NAME}:/config/Documents/ ${TMP_DIR}/
# Create tarball
echo "Creating backup archive..."
tar -czf "${BACKUP_DIR}/wps-docs-${DATE}.tgz" -C ${TMP_DIR} Documents/
# Cleanup
echo "Cleaning up..."
rm -rf ${TMP_DIR}
echo "Backup completed: ${BACKUP_DIR}/wps-docs-${DATE}.tgz"