Published: Aug 2, 2022 by Isaac Johnson
Recently, Codefresh launched a hosted Gitops solution backed by ArgoCD. I became aware of their latest offering from TechCrunch who interviewed their COSO Dan Garfied. Codefresh first launched a GitOps solution based on ArgoCD back in 2020 but just rolled it out publicly now. While the company has it’s own CI solution, it’s easy to integrate with other CI frameworks.
Today we’ll look at Argo through Codefresh and what it offers at the free tier. We’ll set up a couple sample apps on a new K3s cluster and lastly look at multi-cluster deployments.
Signup
Go to Codefresh to sign up
We can use various AuthN methods such as Google or Github
The flow is pretty straightforward with a signup screen
However, boo! for not accepting .science domains. I had to use gmail instead.
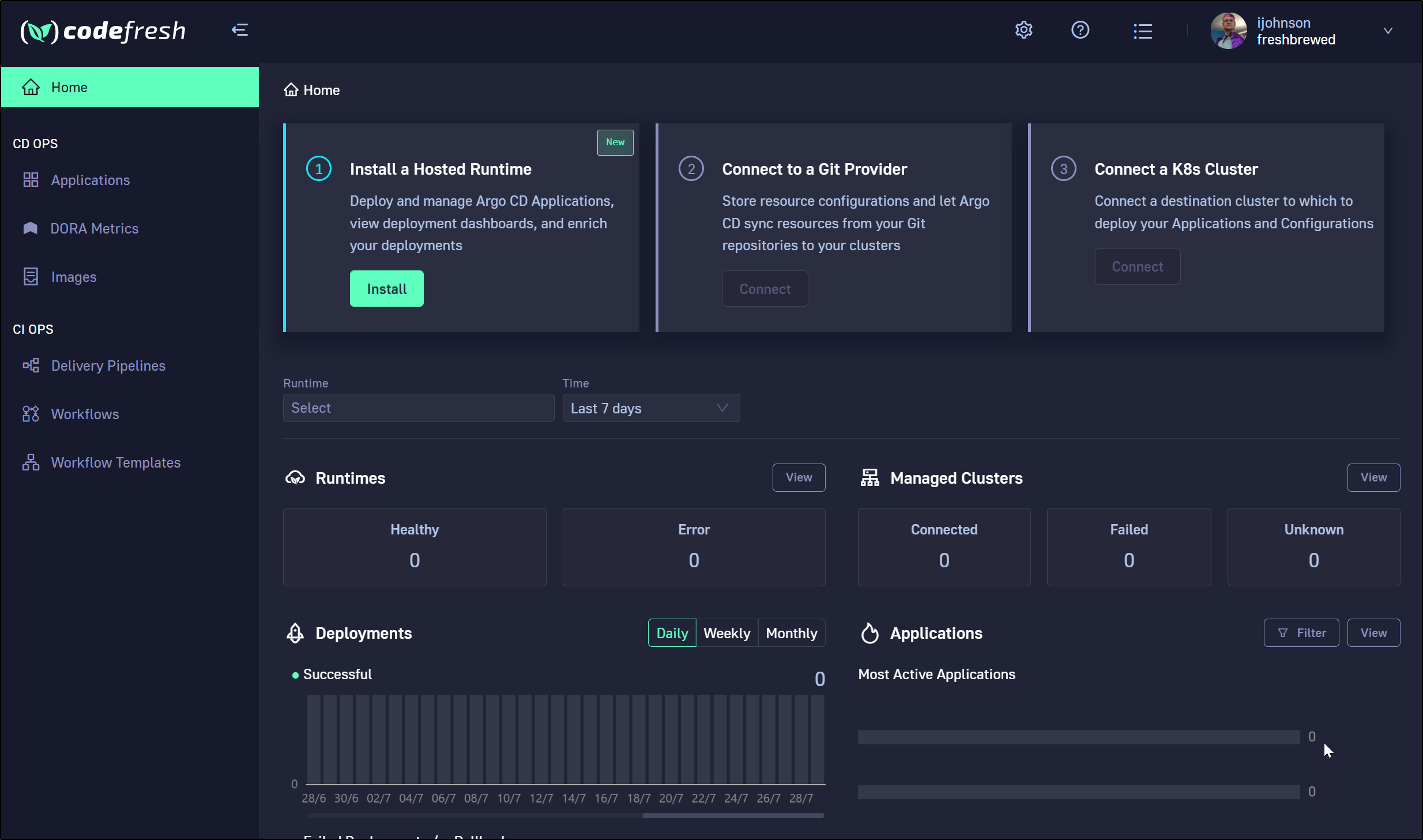
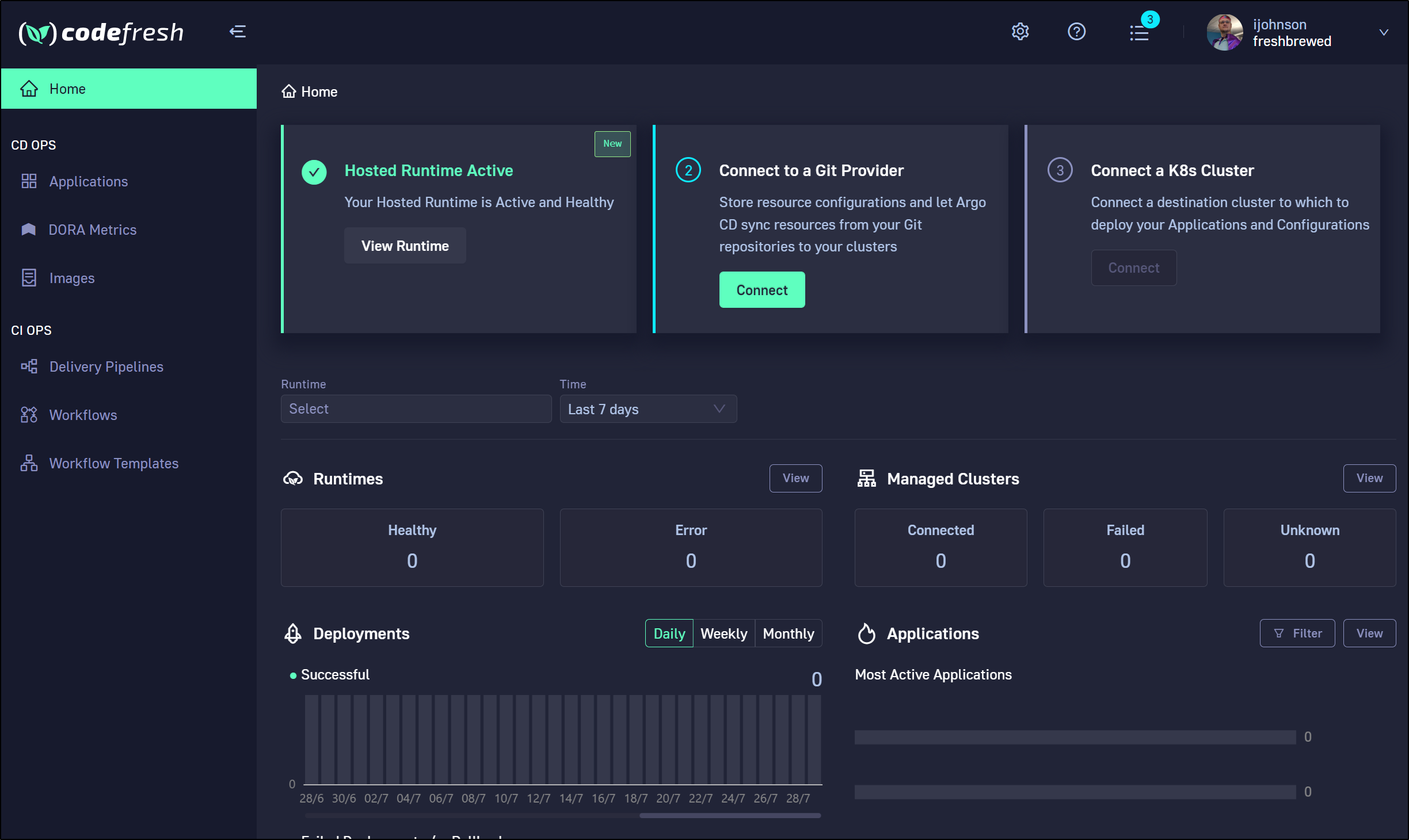
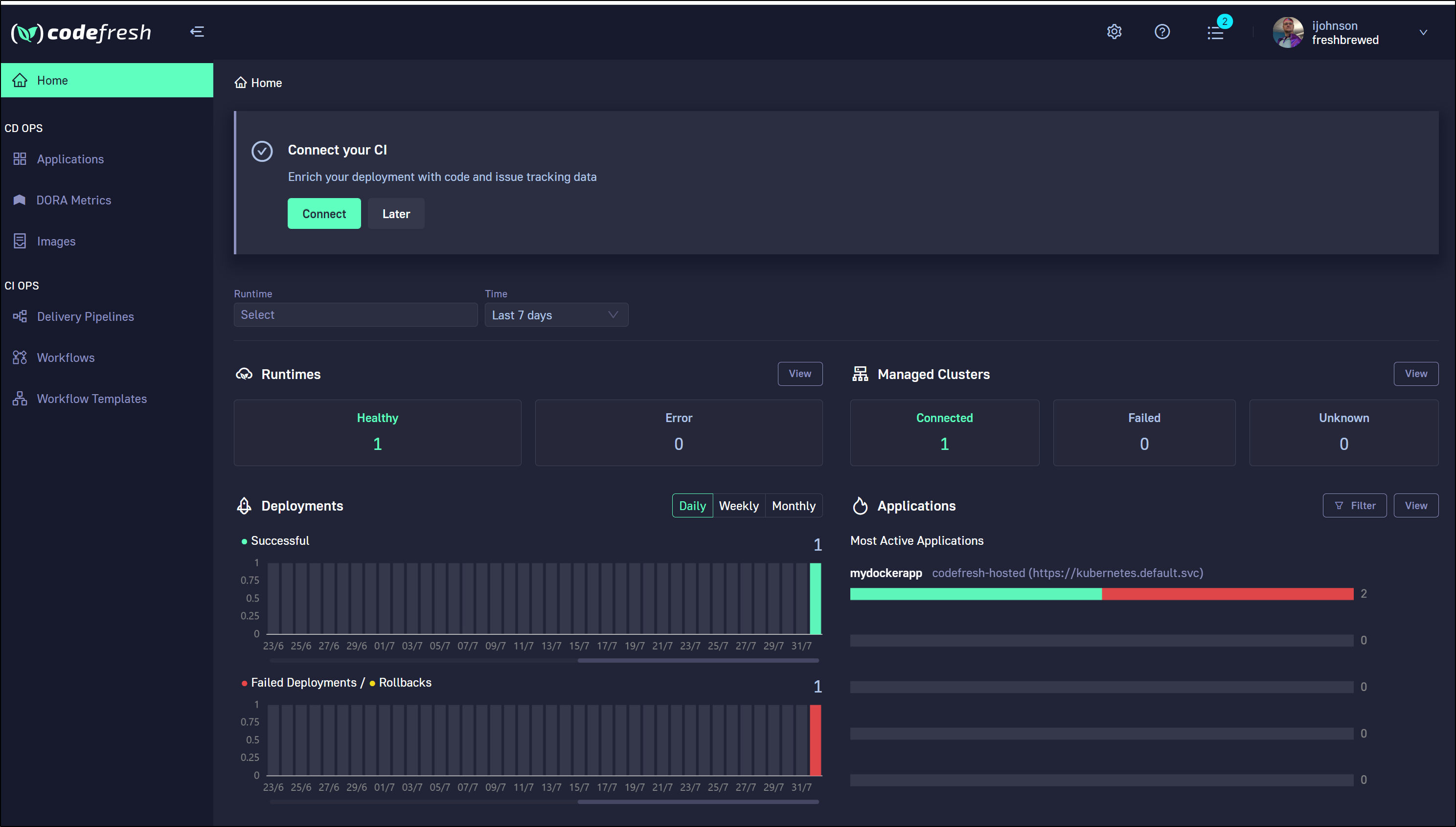
Once signed up, we are presented with the dashboard. Our first step is to install the Codefresh runtime.
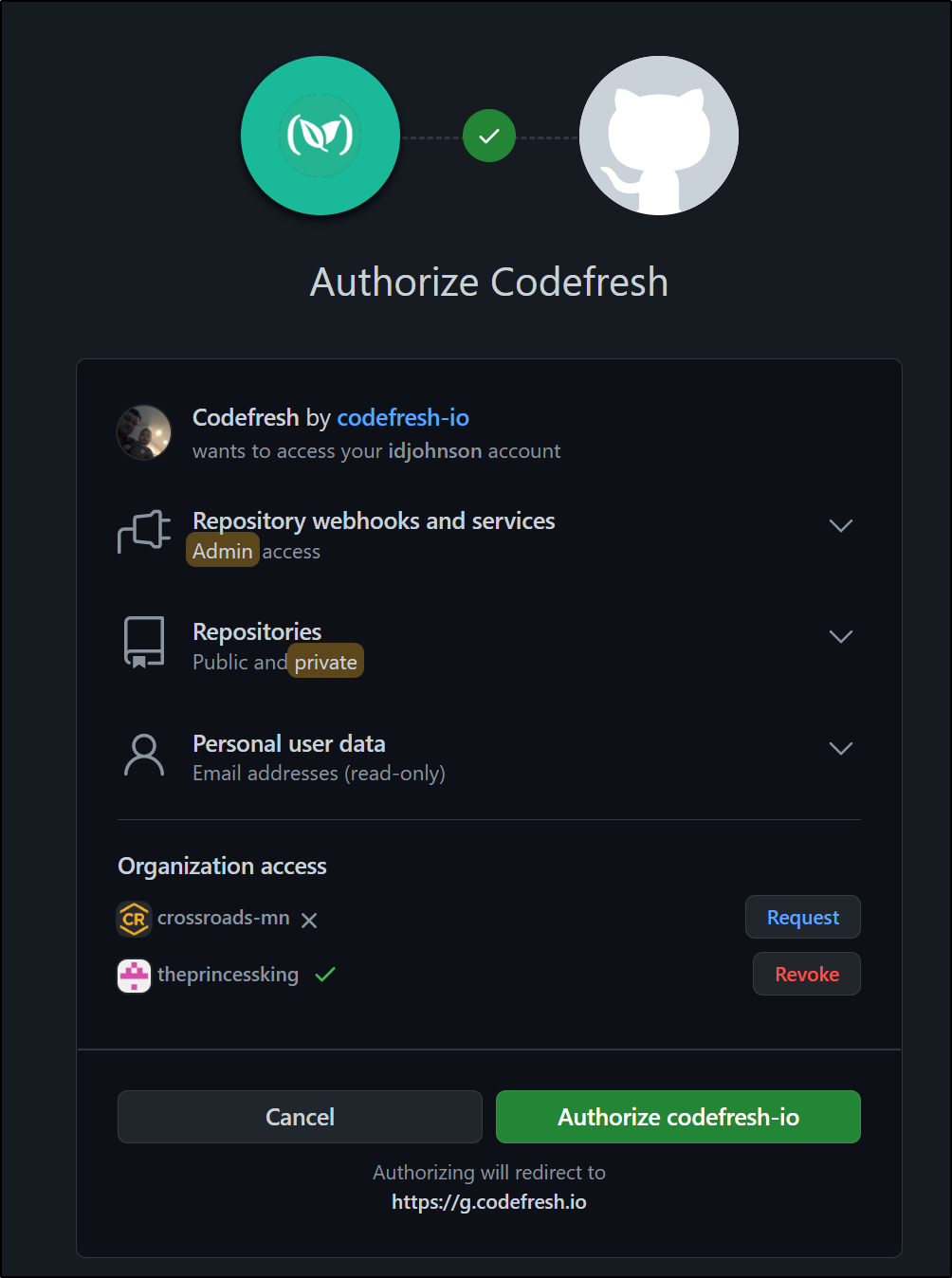
Then connect to a git provider, like Github
We need to authorize it (and to any organizations we wish to include)
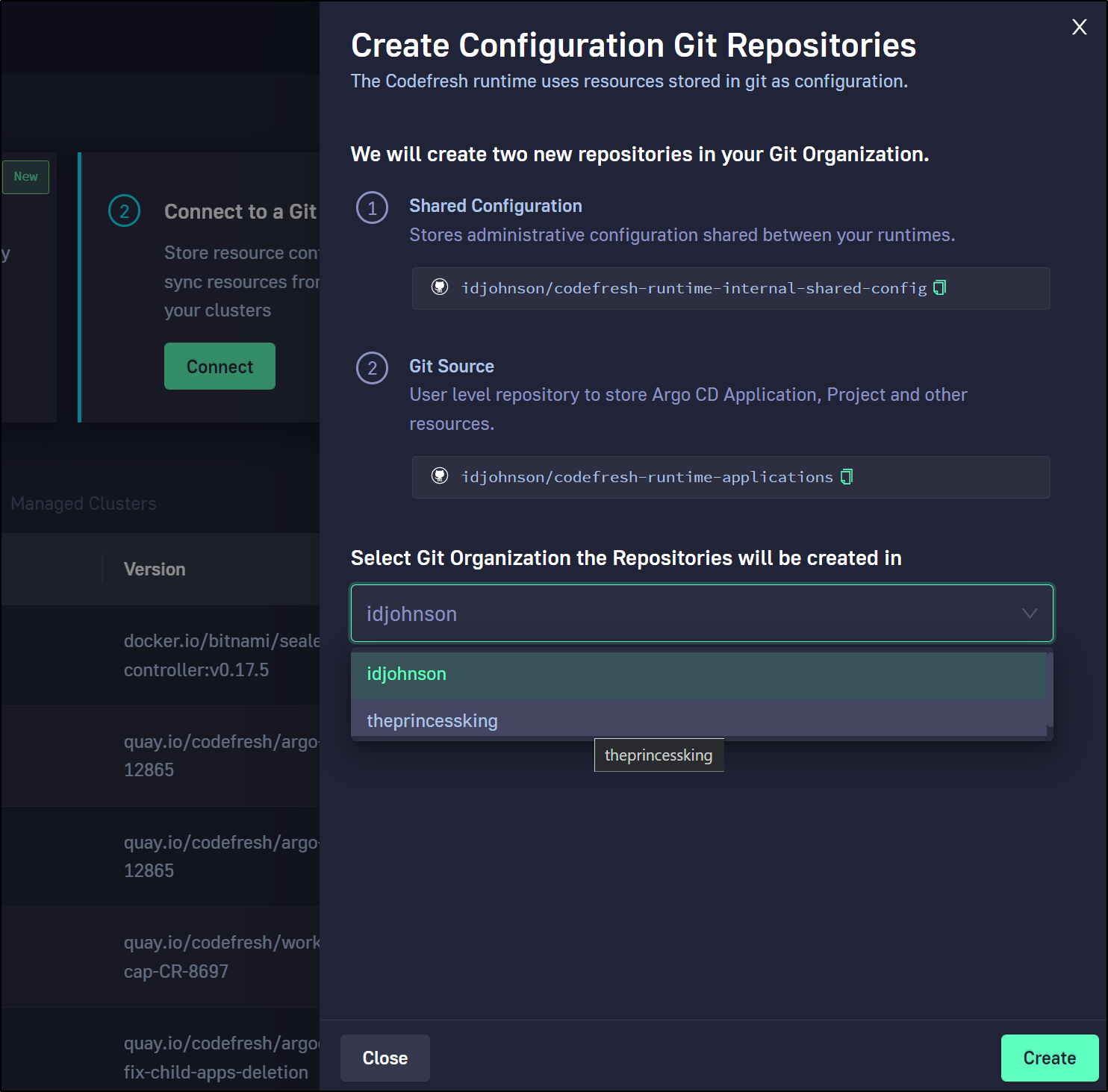
Configuration Repositories
Unlike other Argo offerings, Codefresh will store it’s actual configuration as code in a Github repo. Consider this an “Argo Configuration” repo.
Here we create a configuration repository
Which we can see reflected in Github
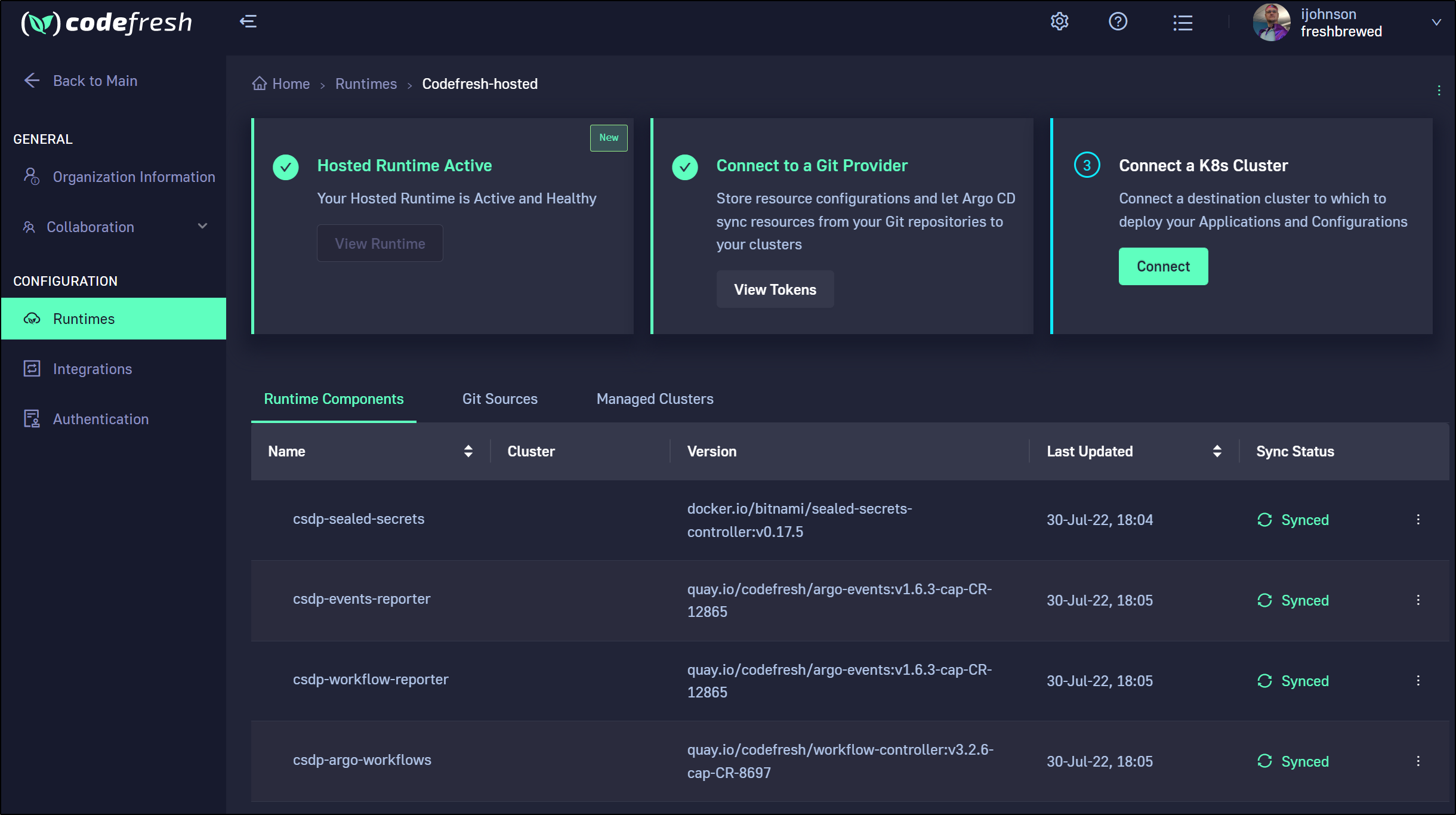
Next, we want to connect a cluster
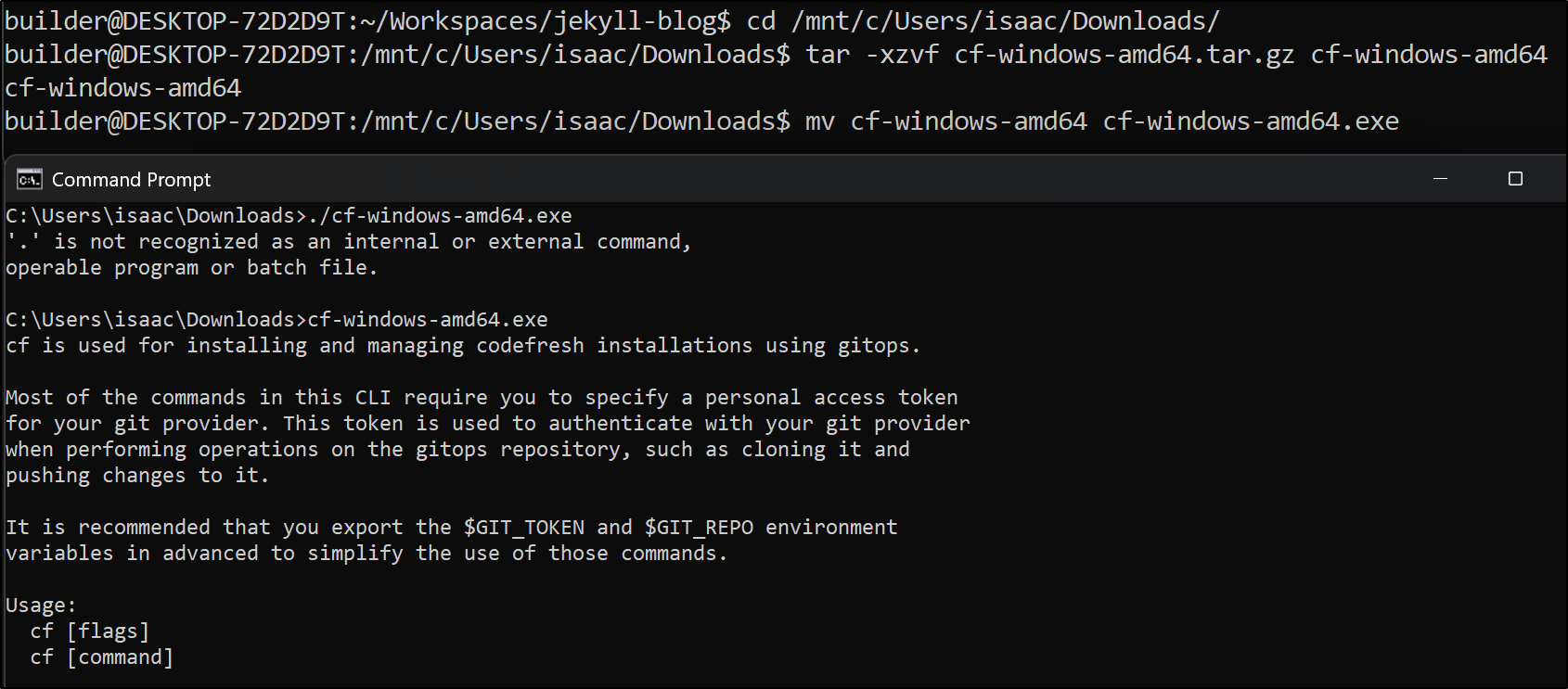
Our first step is to install the CLI
Interestingly, the download for Windows was a tgz that I needed to use WSL to extract. I then needed to give it an “.exe” extension to run.
C:\Users\isaac\Downloads>cf-windows-amd64.exe config create-context codefresh --api-key asdfasfasfsadfasdfas.asdfasdfasdfsadfsadf
level=info msg="New context created: \"codefresh\""
level=info msg="Switched to context: codefresh"
In WSL, the cf binary works the same
$ cf config create-context codefresh --api-key asdfasfasfsadfasdfas.asdfasdfasdfsadfsadf
INFO New context created: "codefresh"
INFO Switched to context: codefresh
Adding Clusters
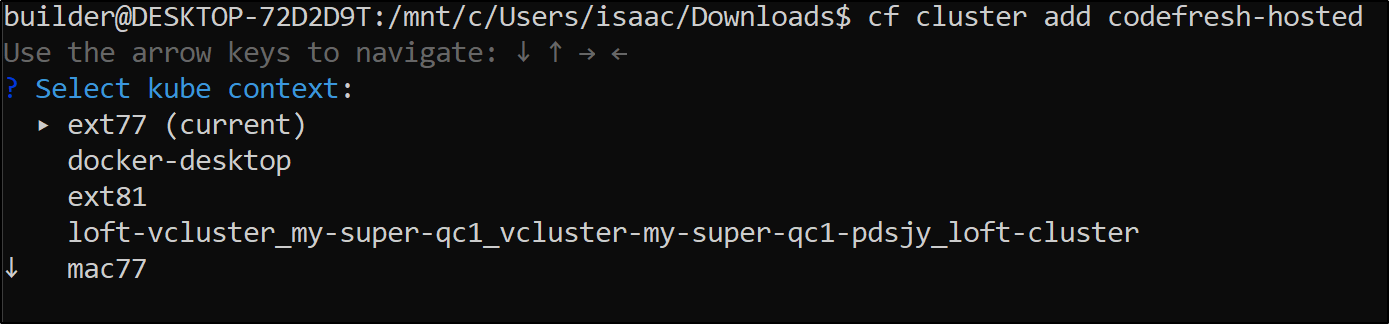
We can then add a cluster with cf cluster add codefresh-hosted
We see what was installed
$ cf cluster add codefresh-hosted
ext77
INFO Building "add-cluster" manifests
serviceaccount/argocd-manager-1659314524497 created
clusterrole.rbac.authorization.k8s.io/argocd-manager-role-1659314524497 created
clusterrolebinding.rbac.authorization.k8s.io/argocd-manager-role-binding-1659314524497 created
configmap/csdp-add-cluster-cm-1659314524497 created
secret/csdp-add-cluster-secret-1659314524497 created
job.batch/csdp-add-cluster-job-1659314524497 created
INFO Attempt #1/1 succeeded:
=====
ServiceAccount: argocd-manager-1659314524497
Ingress URL: https://mr-62e3d9f588d8af3a8b8581d3-d6dd0e5.cf-cd.com
Context Name: ext77
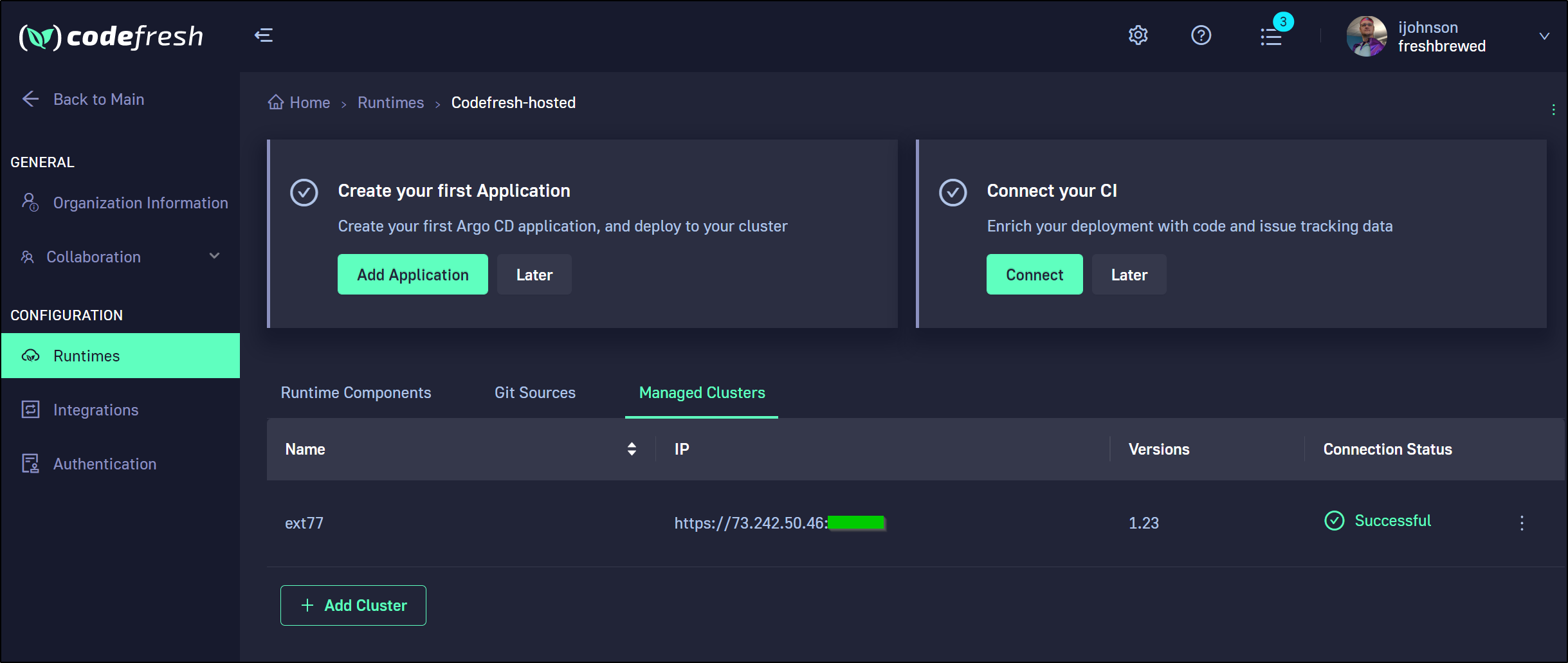
Server: https://73.242.50.46:25560
Found ServiceAccount secret argocd-manager-1659314524497-token-dpkks
Cluster "73.242.50.46:25560" set.
User "argocd-manager-1659314524497" set.
Context "ext77" created.
STATUS_CODE: 201
deleting token secret csdp-add-cluster-secret-1659314524497
secret "csdp-add-cluster-secret-1659314524497" deleted
=====
cluster ext77 was added successfully to runtime codefresh-hosted
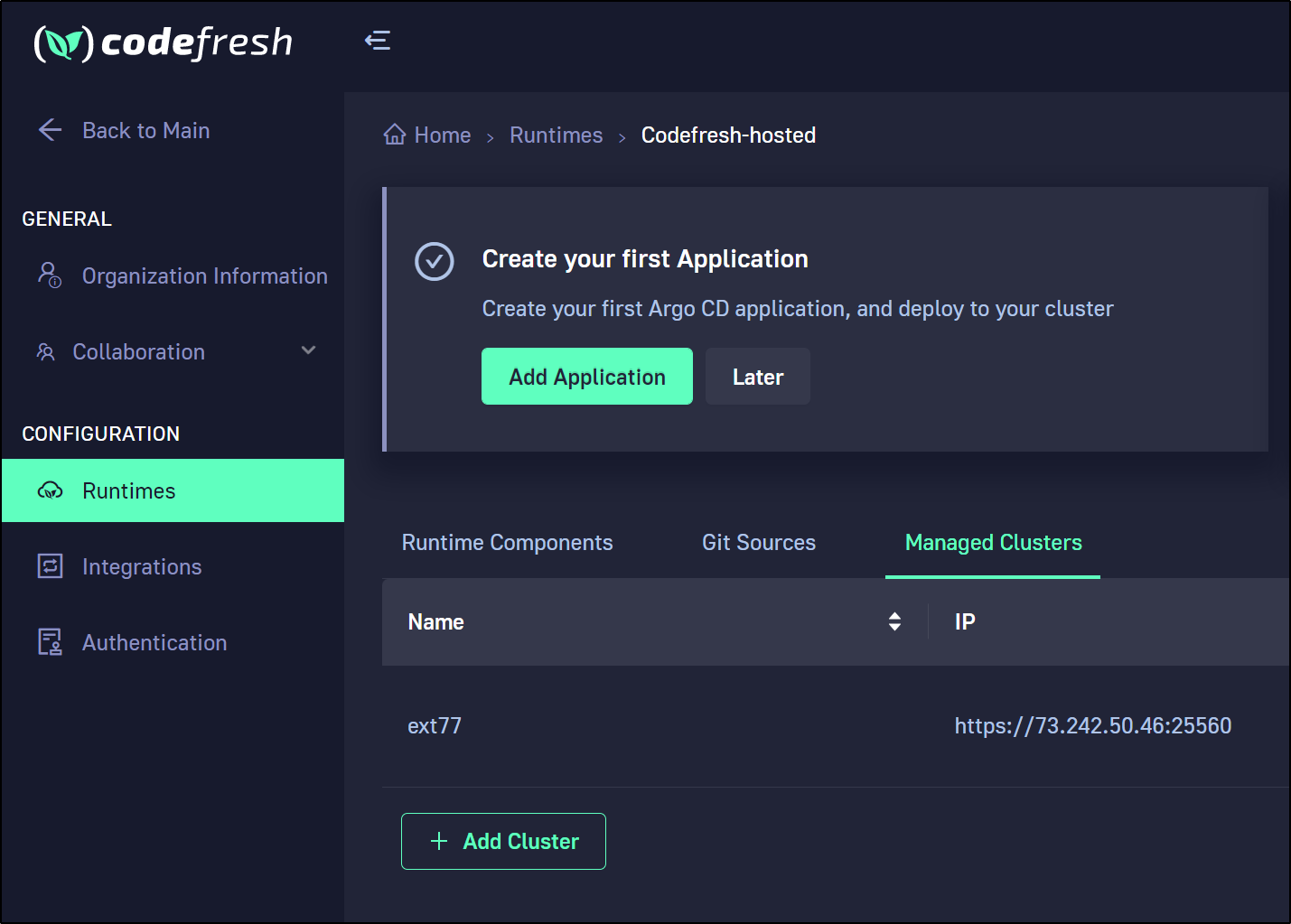
And now we can verify that cluster was added
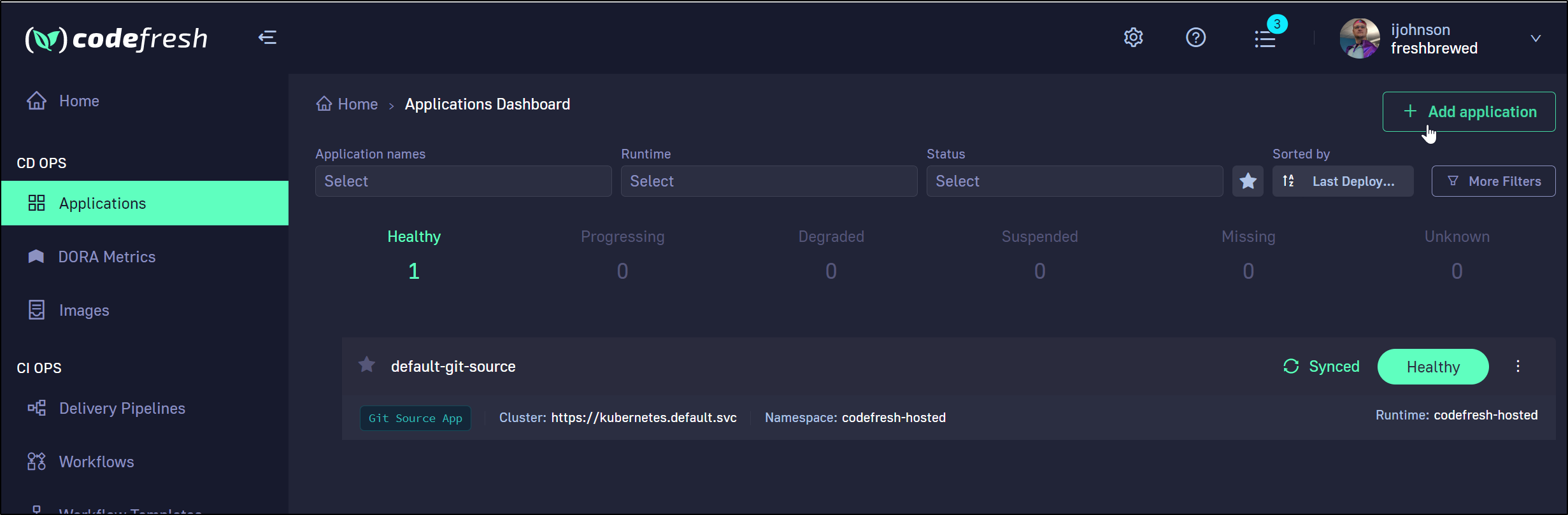
Add Application
Our next step is to add an application
Choose “Add Application” from the application menu
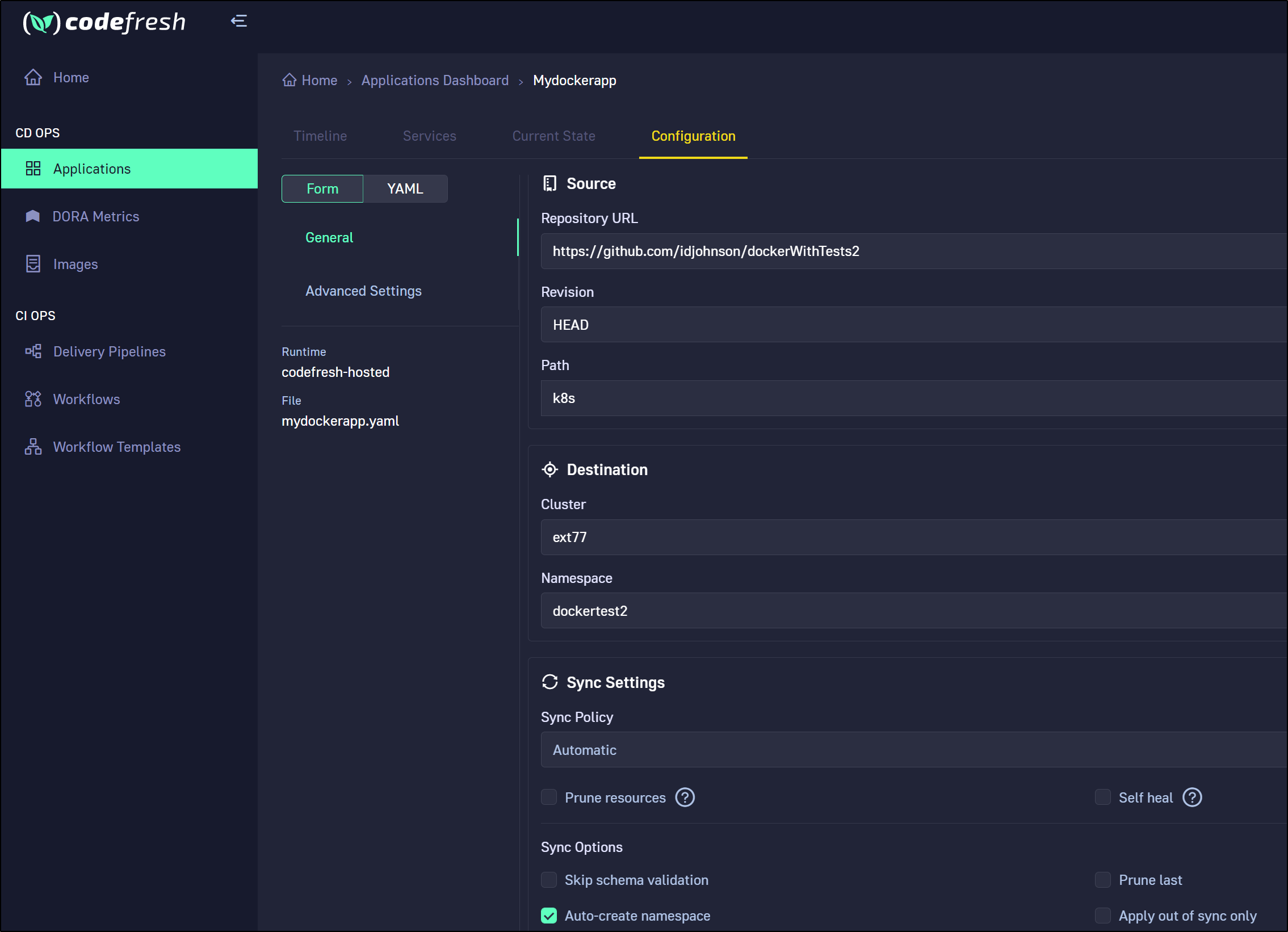
We give the app a name and YAML file. The next screen allows us to enter standard Argo details.
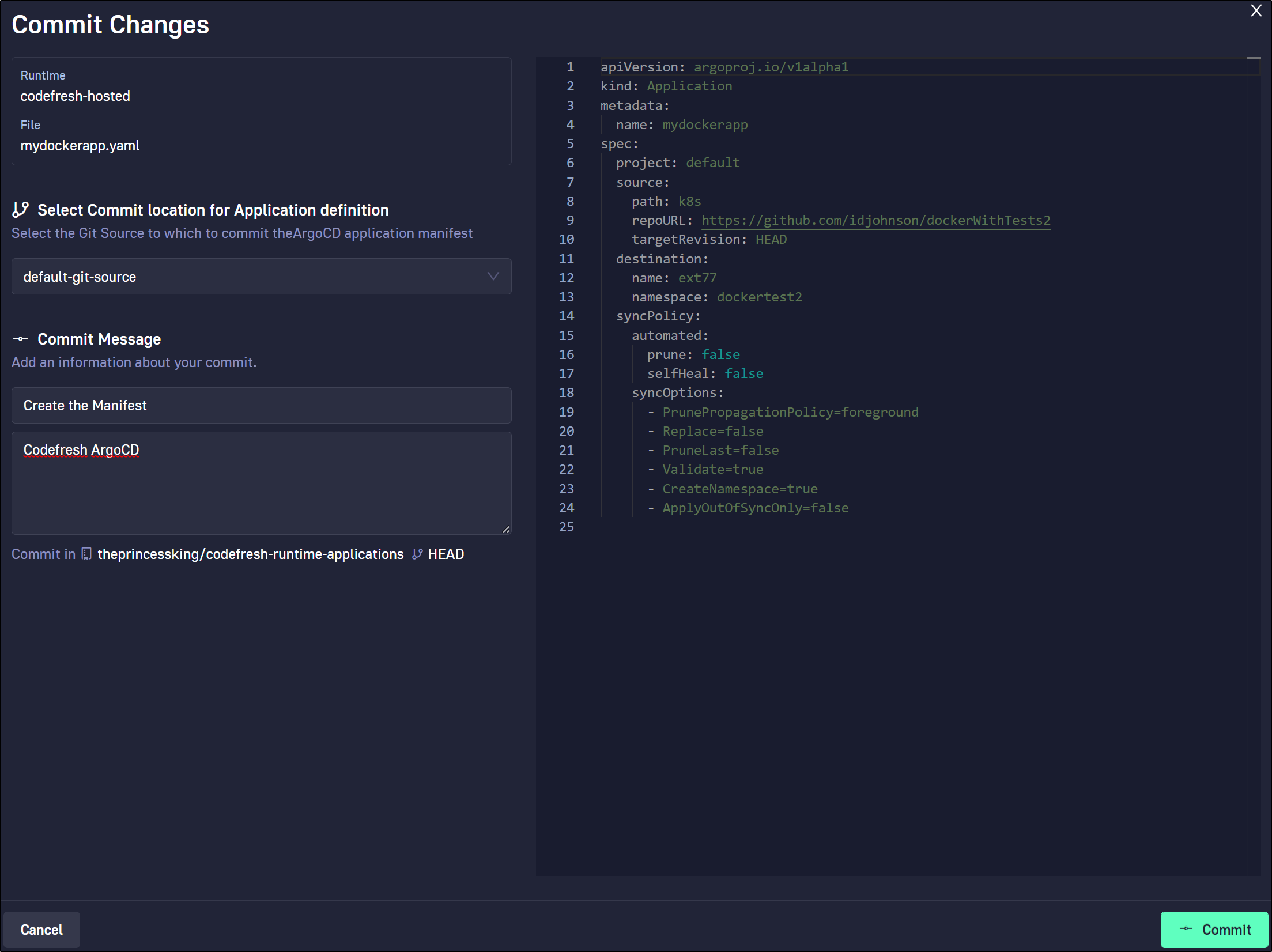
We can then decide where to save the Manifest file
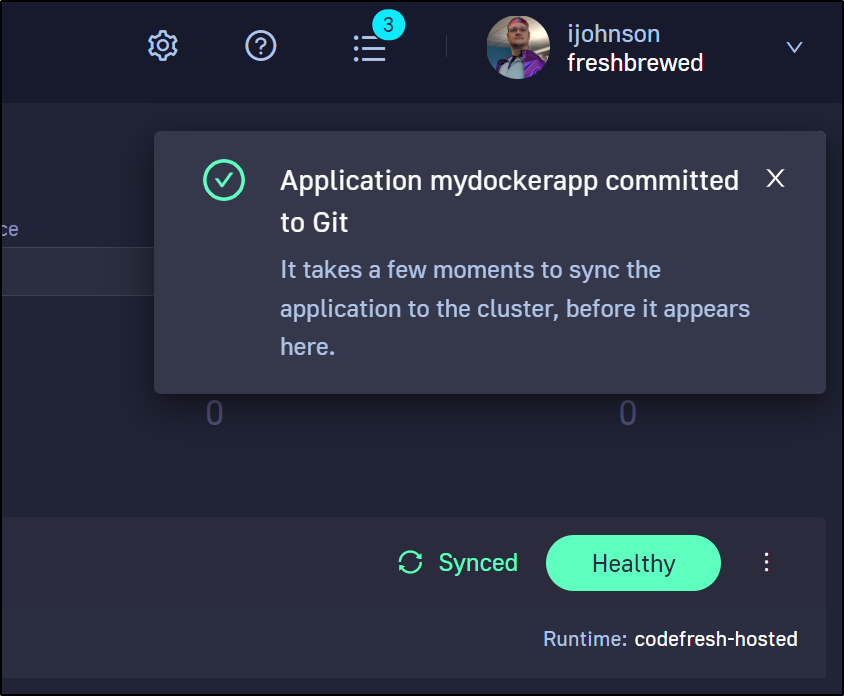
We see that the application was added
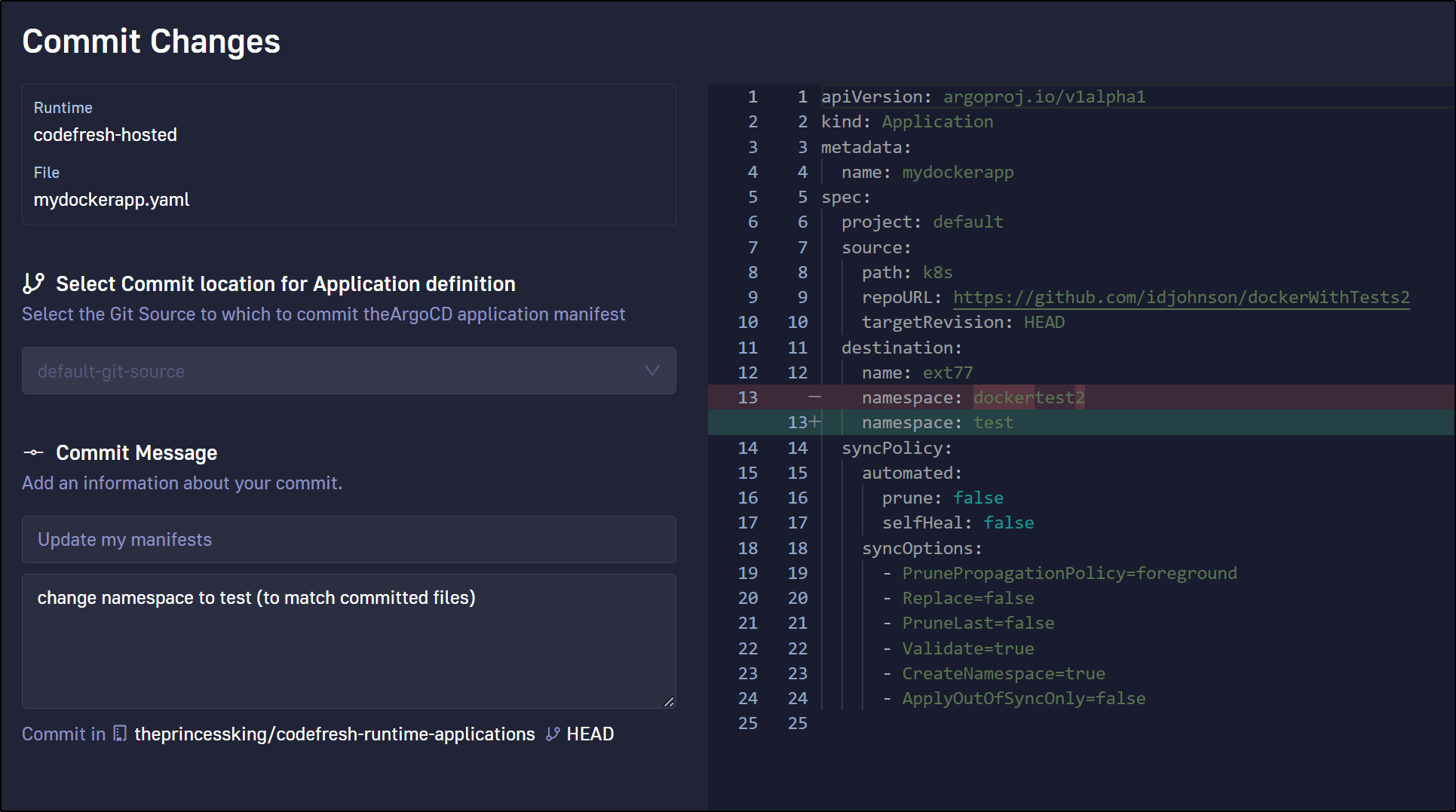
I had errors since I hardcoded the “test” namespace on main. I changed the app and committed it
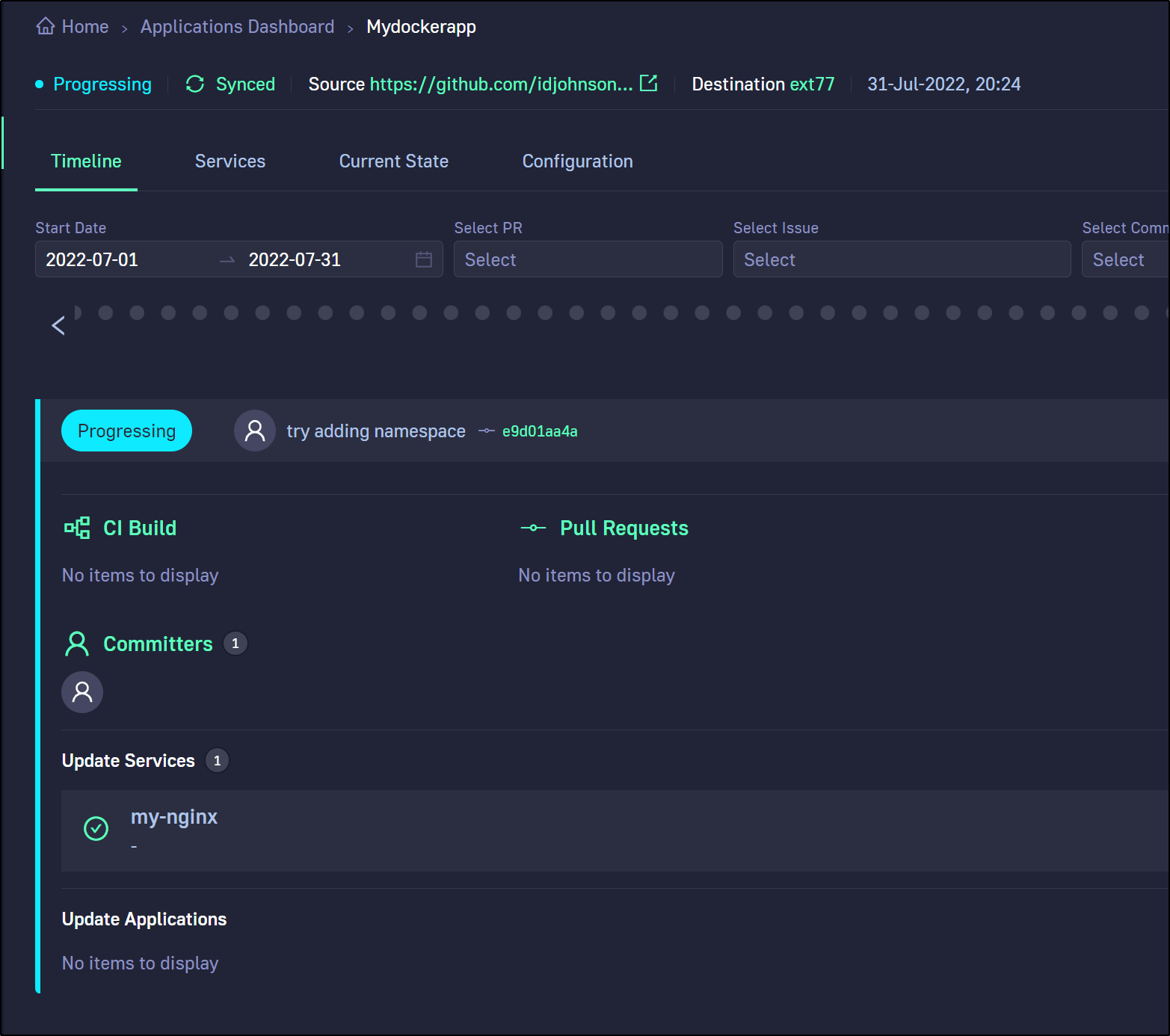
And now we can see it progressing (after I created the “test” namespace)
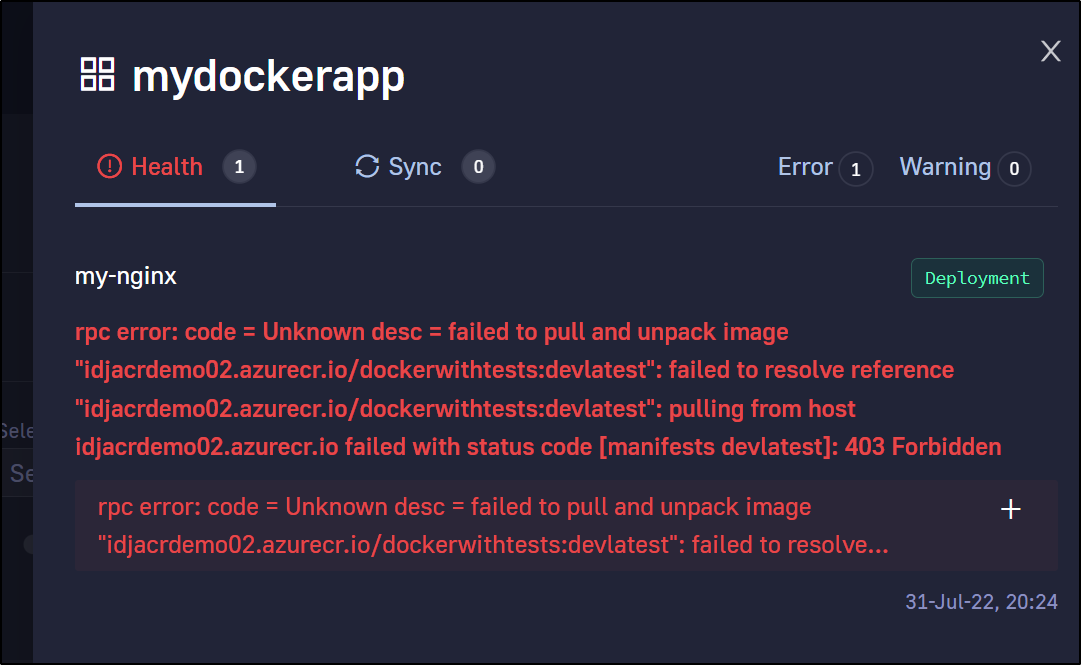
Now my error is around the lack of credentials (403) accessing my Azure CR
Updating Applications
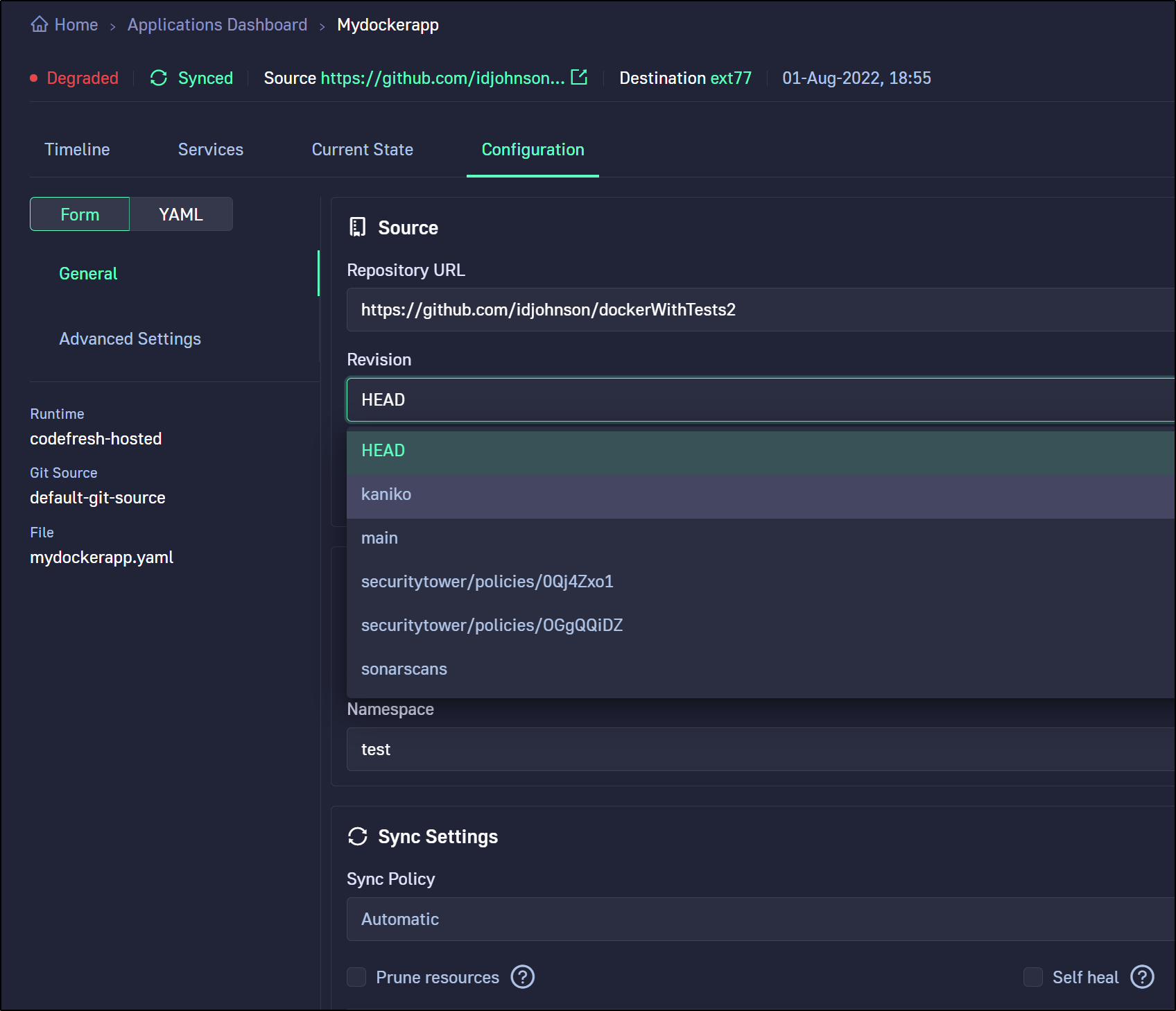
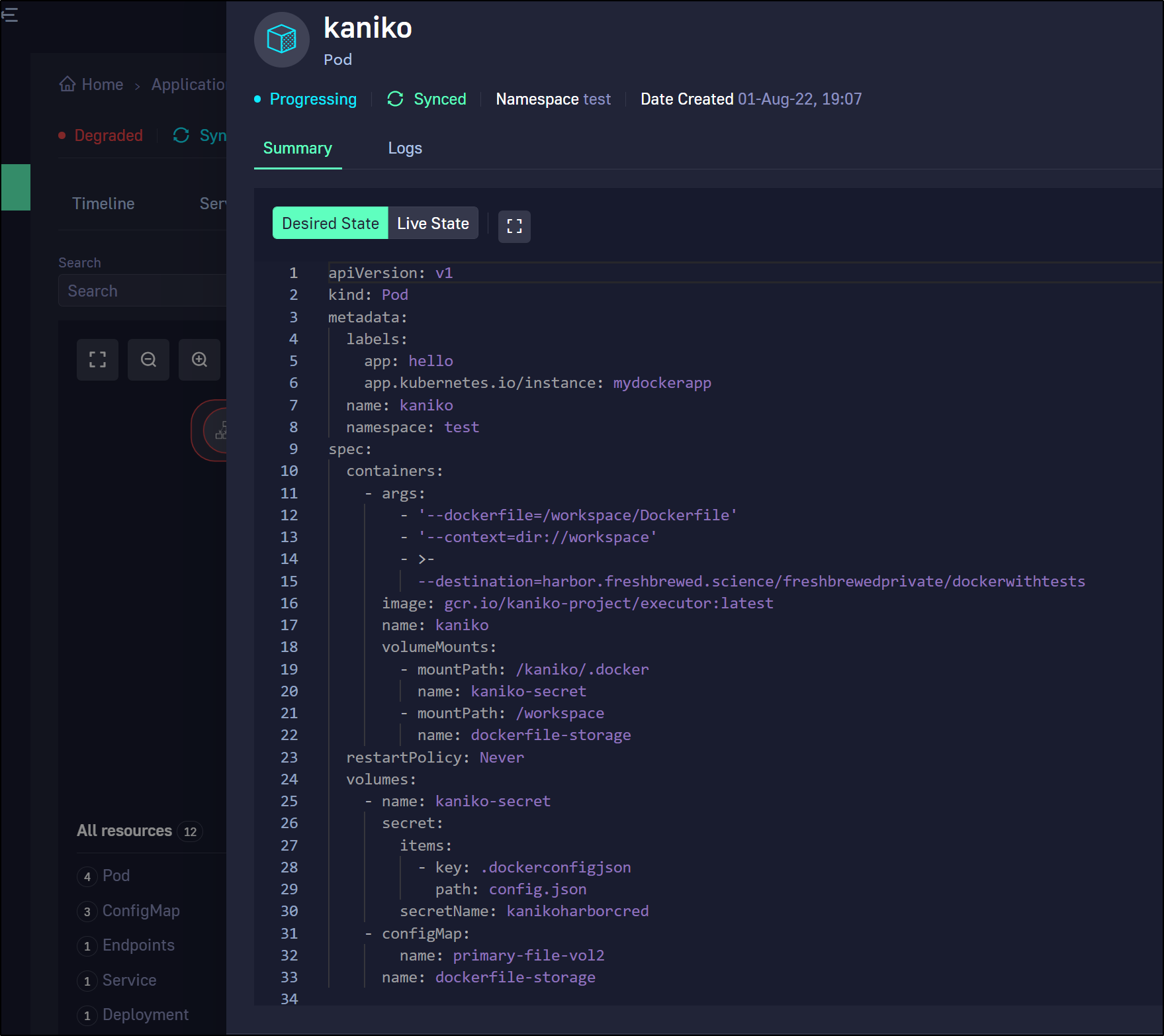
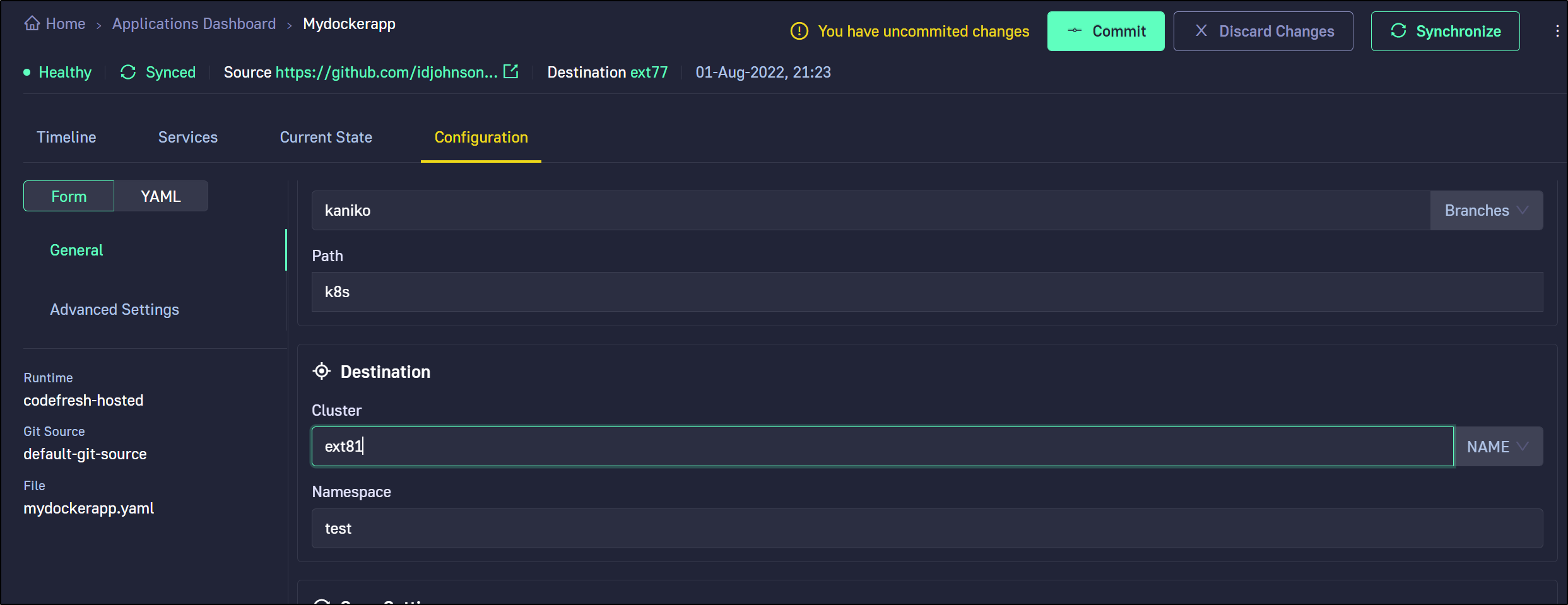
We can change branches to switch applications. Here I switched to the kaniko branch
we can see it sync
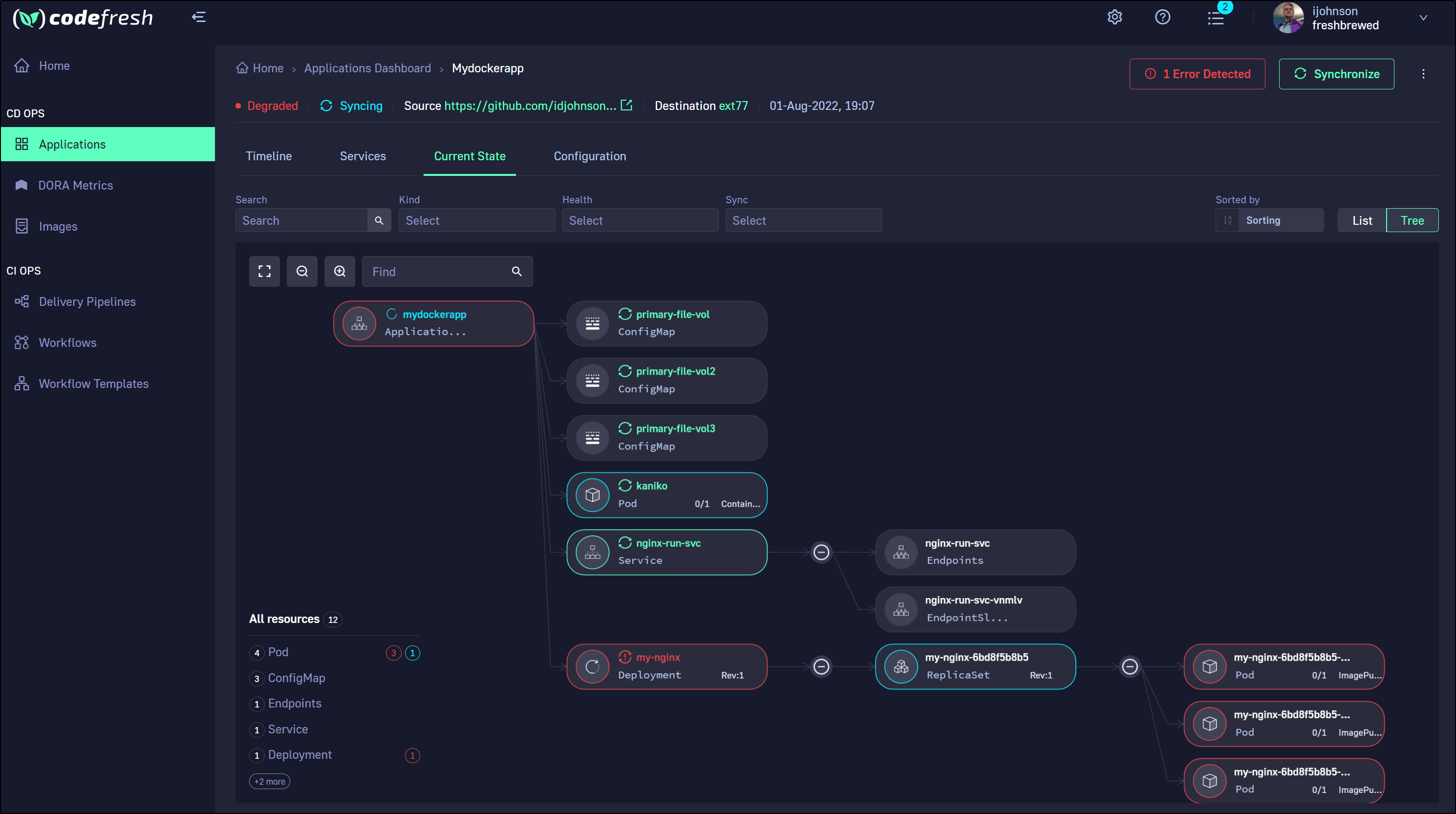
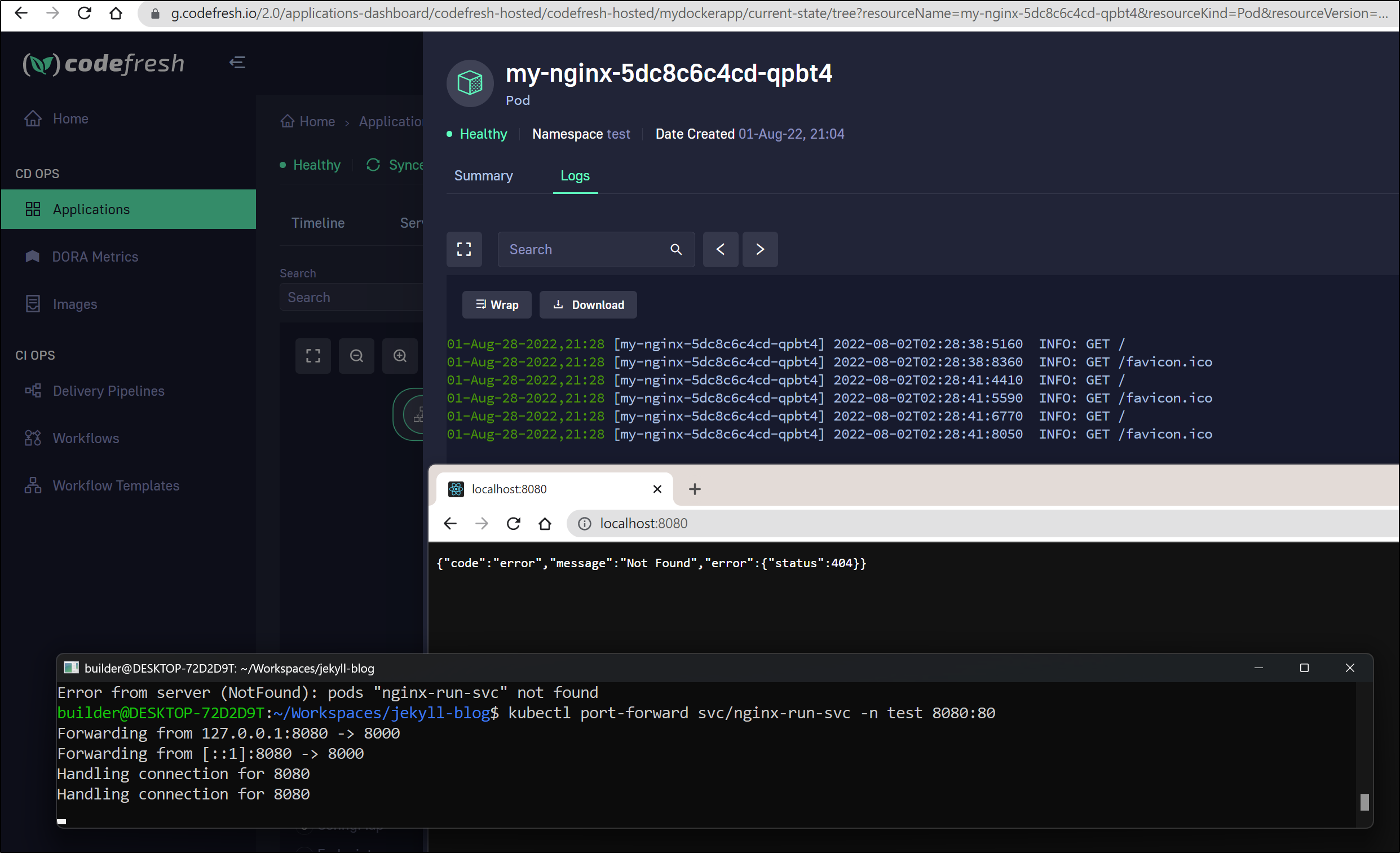
I can check the pod details for manifest
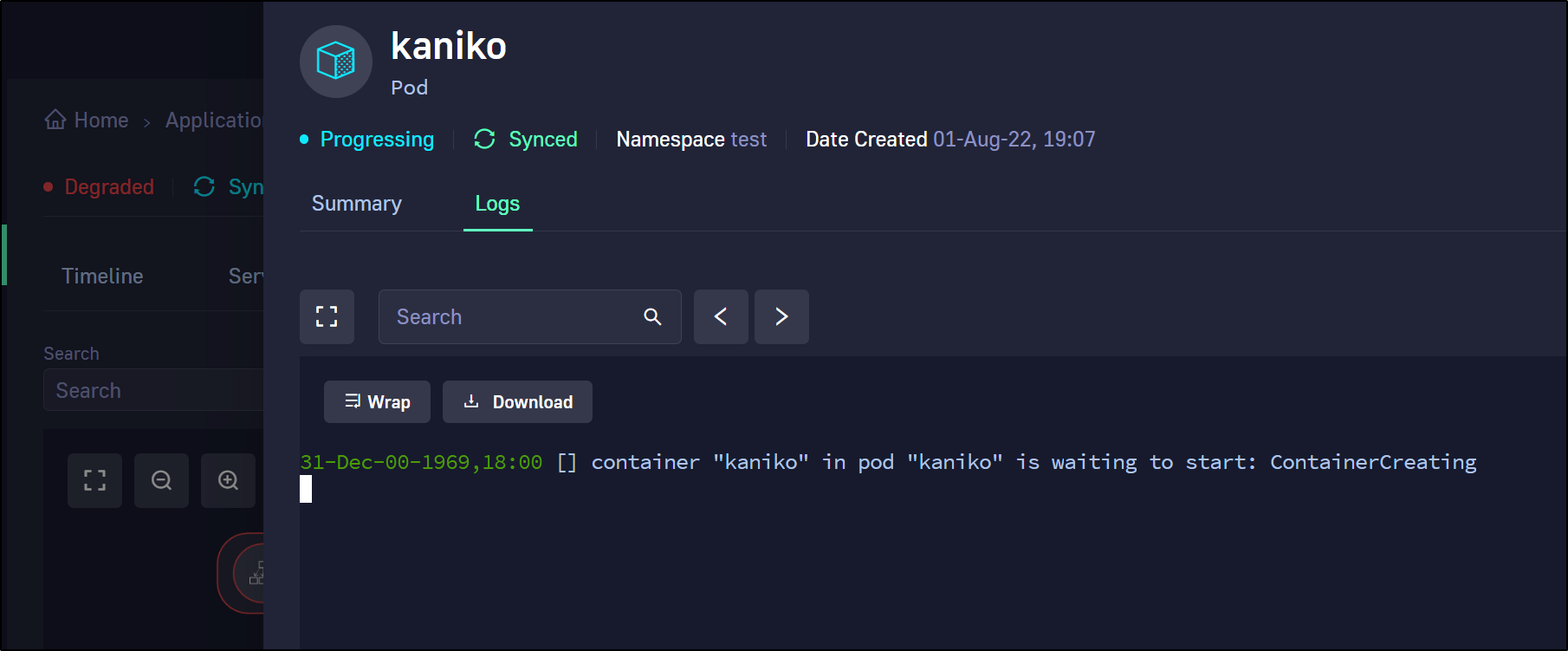
and logs
When it didn’t come up for a while, i went to the cluster to check on it.
We can see it’s due to my missing secret
$ kubectl describe pod kaniko -n test | tail -n 7
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 7m11s default-scheduler Successfully assigned test/kaniko to isaac-macbookair
Warning FailedMount 2m50s (x2 over 5m8s) kubelet Unable to attach or mount volumes: unmounted volumes=[kaniko-secret], unattached volumes=[kaniko-secret dockerfile-storage kube-api-access-jdkmf]: timed out waiting for the condition
Warning FailedMount 59s (x11 over 7m11s) kubelet MountVolume.SetUp failed for volume "kaniko-secret" : secret "kanikoharborcred" not found
Warning FailedMount 35s kubelet Unable to attach or mount volumes: unmounted volumes=[kaniko-secret], unattached volumes=[dockerfile-storage kube-api-access-jdkmf kaniko-secret]: timed out waiting for the condition
I need to copy over the missing secret
builder@DESKTOP-72D2D9T:~/Workspaces/jekyll-blog$ kubectx mac81
Switched to context "mac81".
builder@DESKTOP-72D2D9T:~/Workspaces/jekyll-blog$ kubectl get secret kanikoharborcred -n test -o yaml > khc.test.yaml
builder@DESKTOP-72D2D9T:~/Workspaces/jekyll-blog$ kubectx mac77
Switched to context "mac77".
builder@DESKTOP-72D2D9T:~/Workspaces/jekyll-blog$ kubectl apply -f khc.test.yaml
secret/kanikoharborcred created
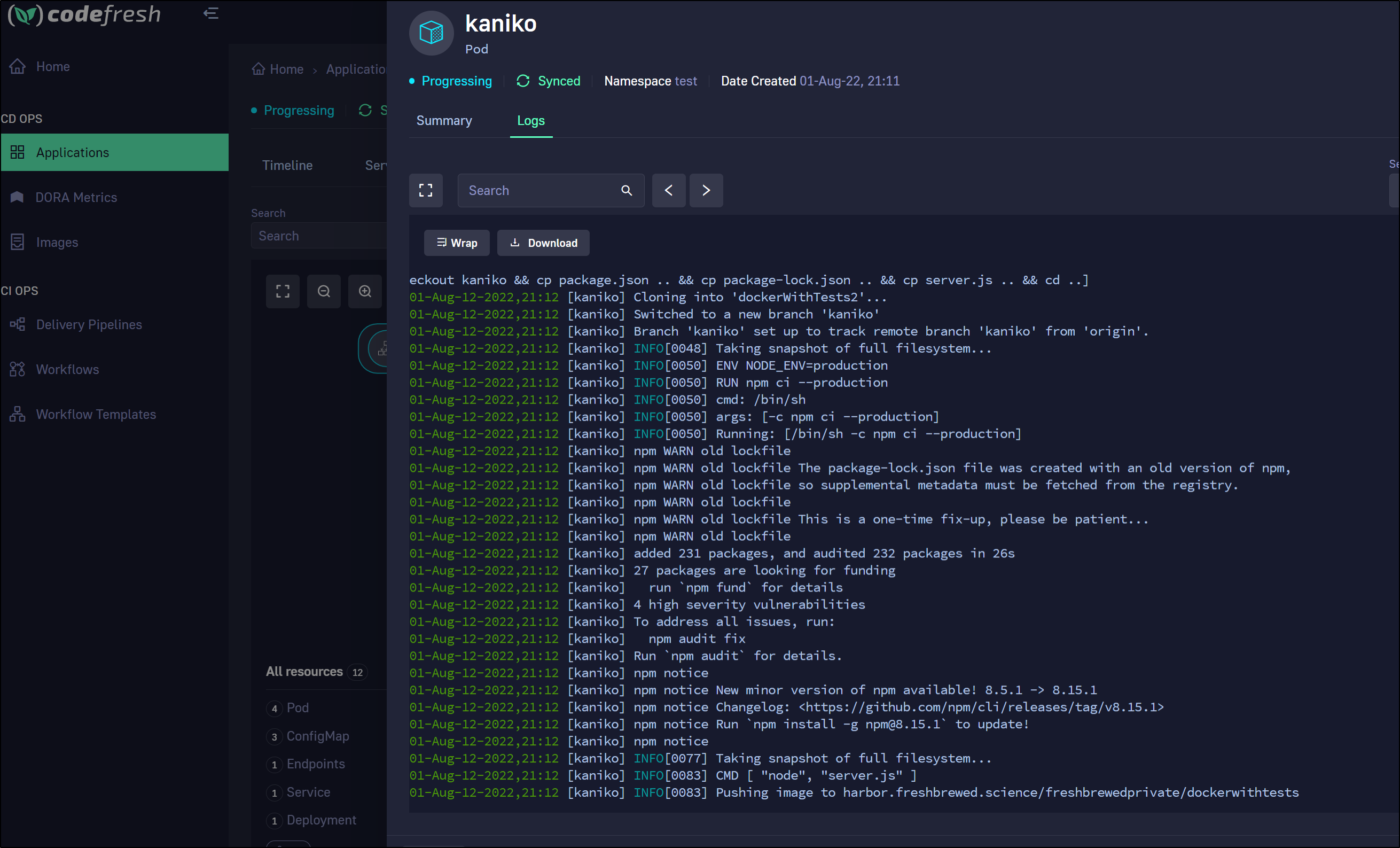
Once I fixed the secret and membership on the project, the container started to build
Then once the pods found their registry credential, they could launch
We can see it’s serving traffic by looking at live logs
Dashboards
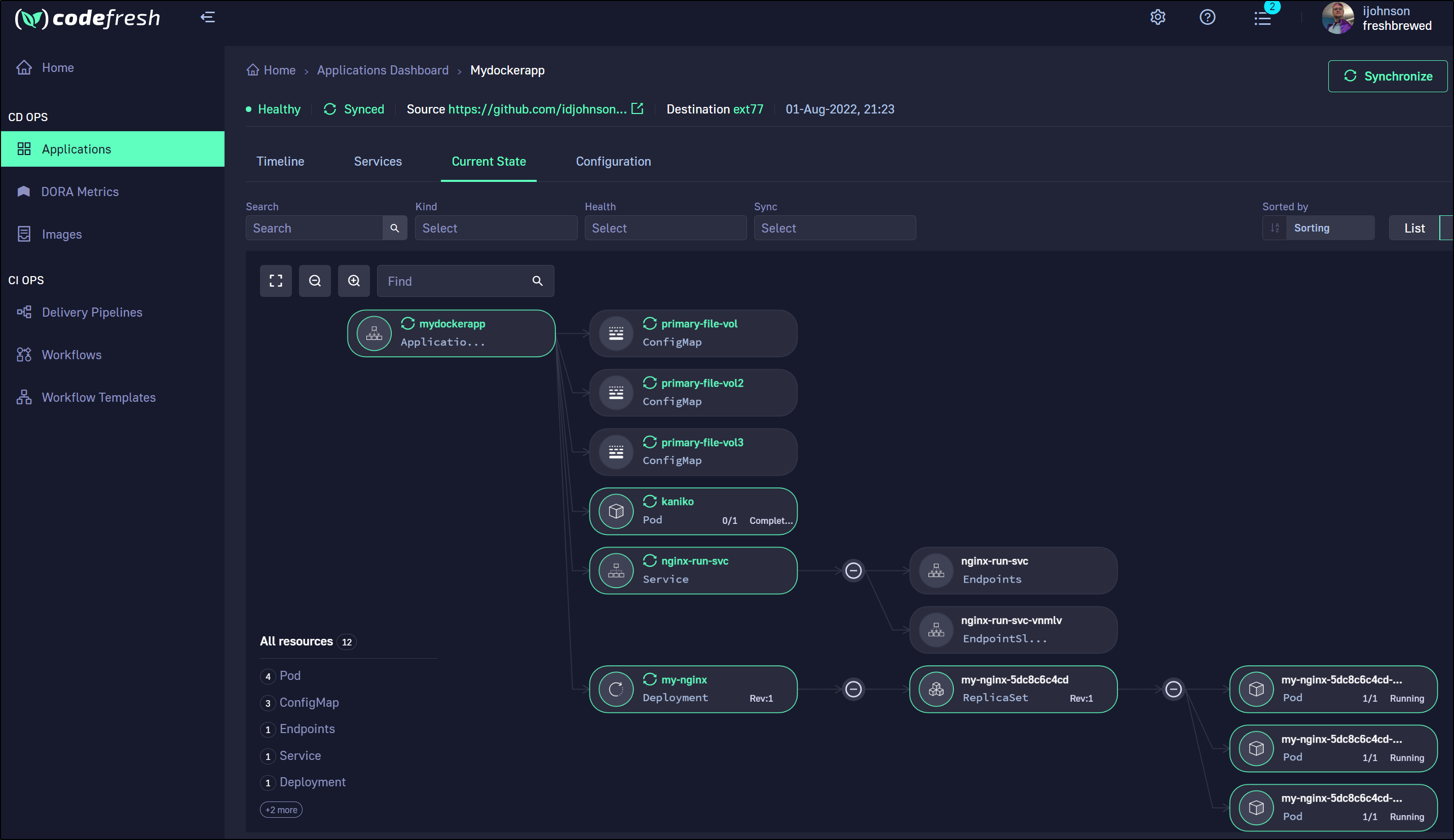
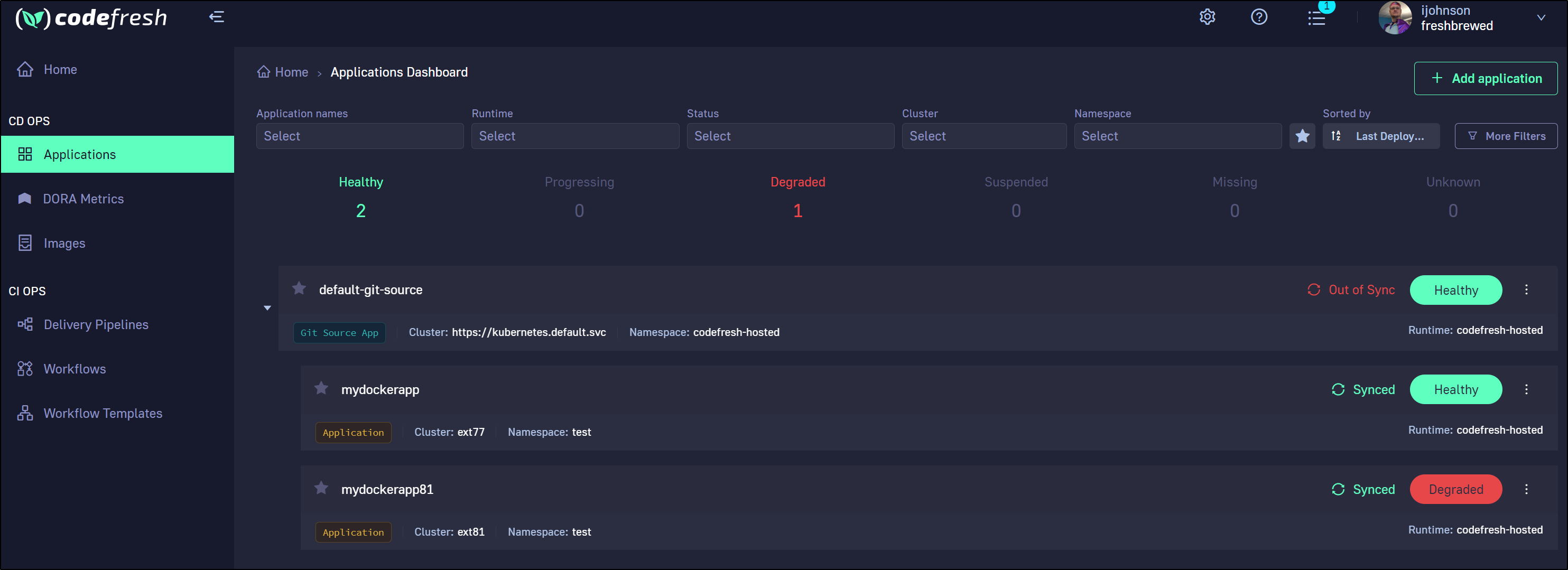
From our Dashboard we can see the successful deployment
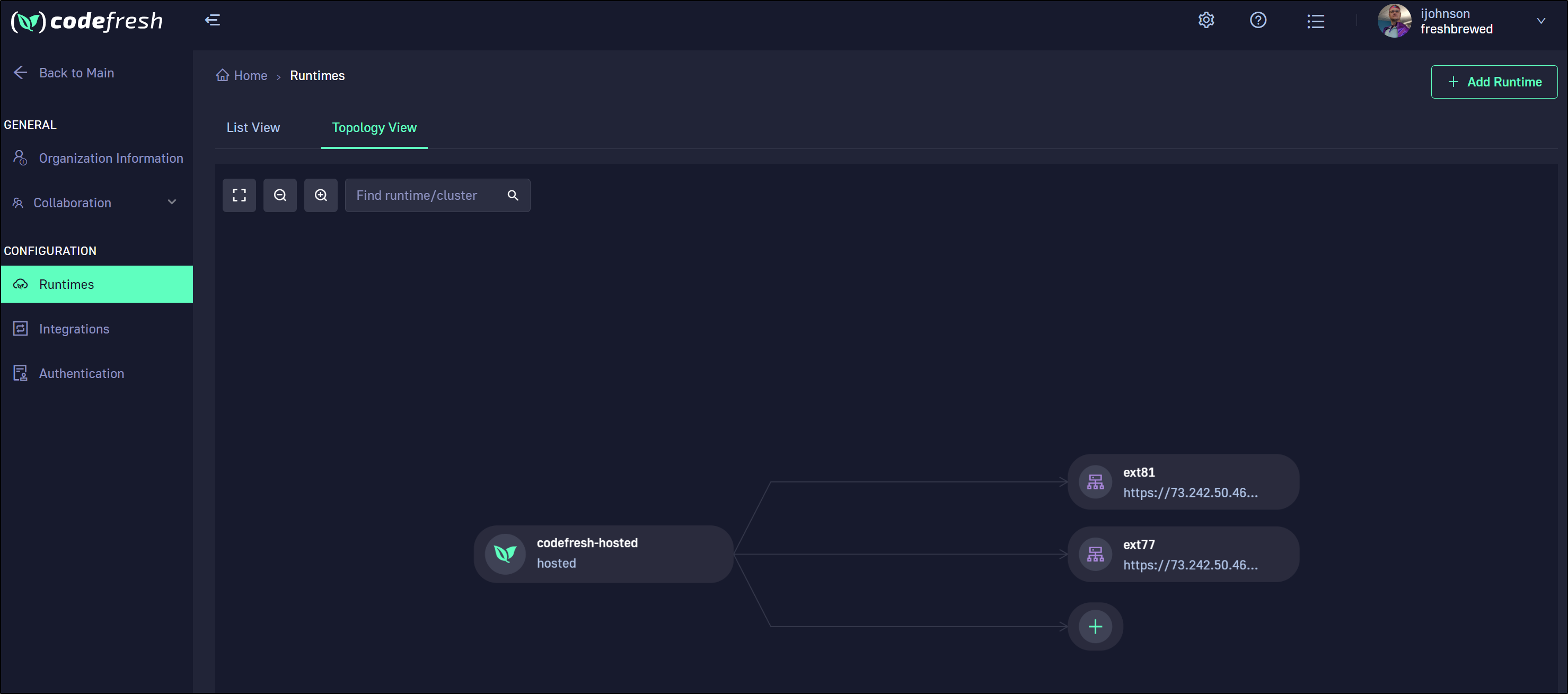
we can go to Runtimes to add more clusters
We can change namespace and/or cluster in the edit application page
We can add more applications for the same repository, but a new cluster
Next steps
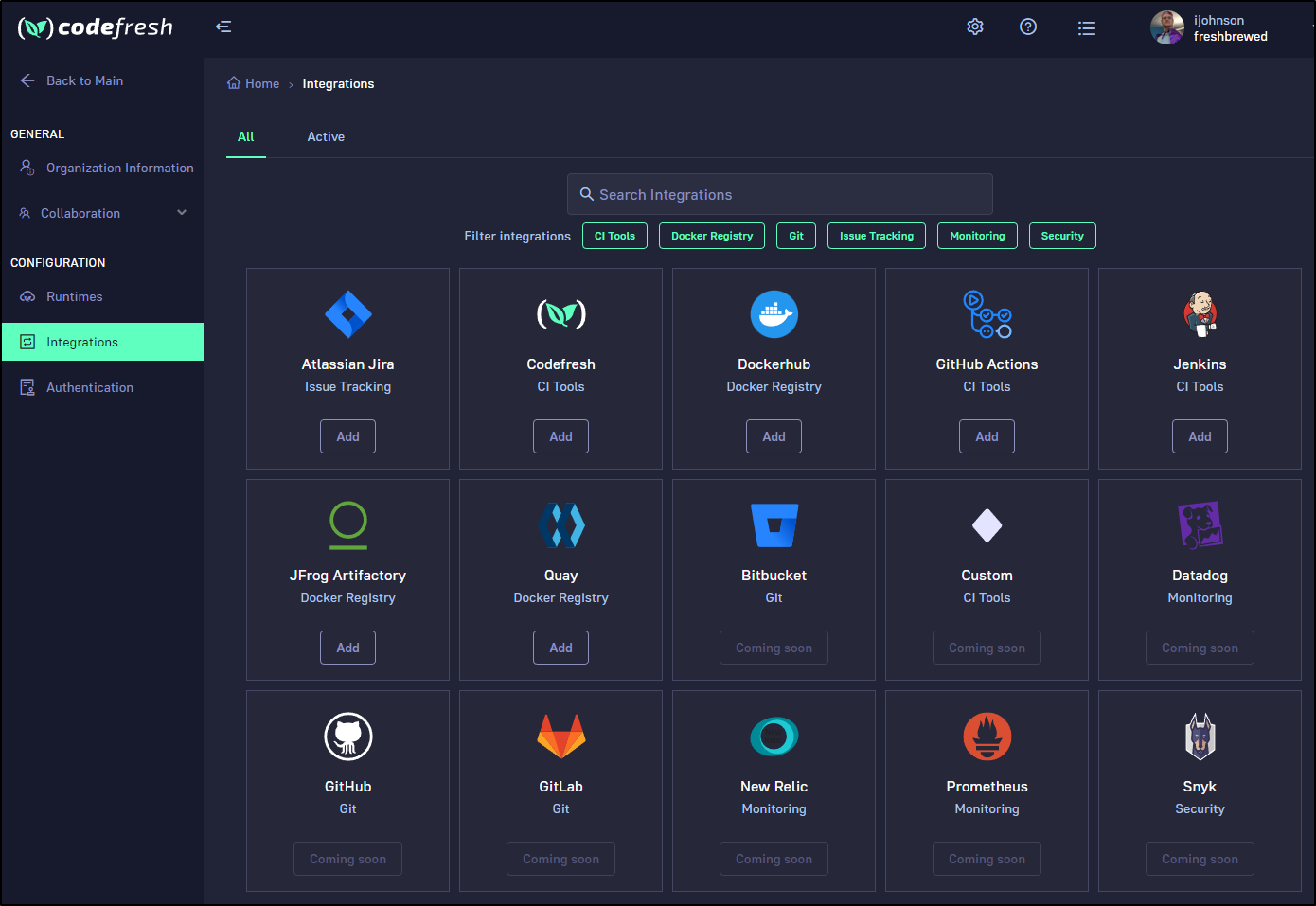
They have a series of integrations already setup and a few “coming soon”
Obviously, I care deeply about monitoring so adding Github integration (likely for PR flows) will be key as well as Datadog for monitoring.
JIRA
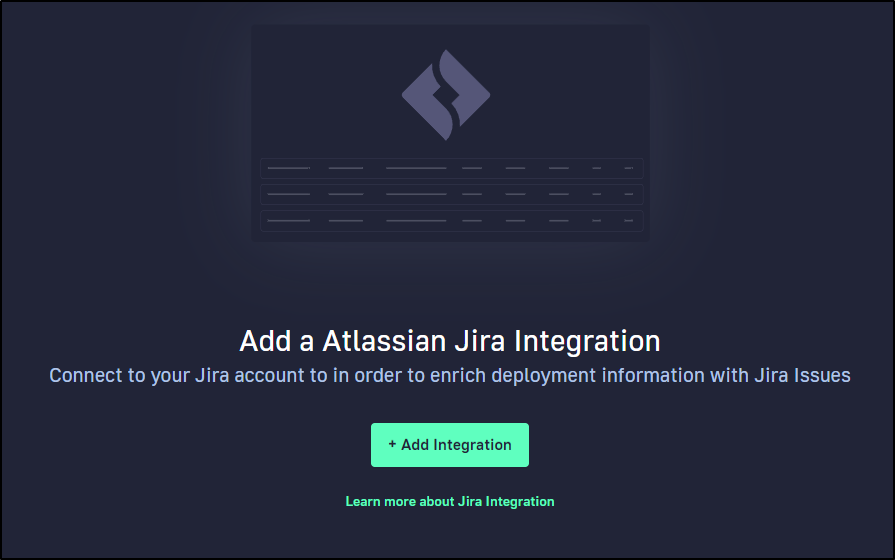
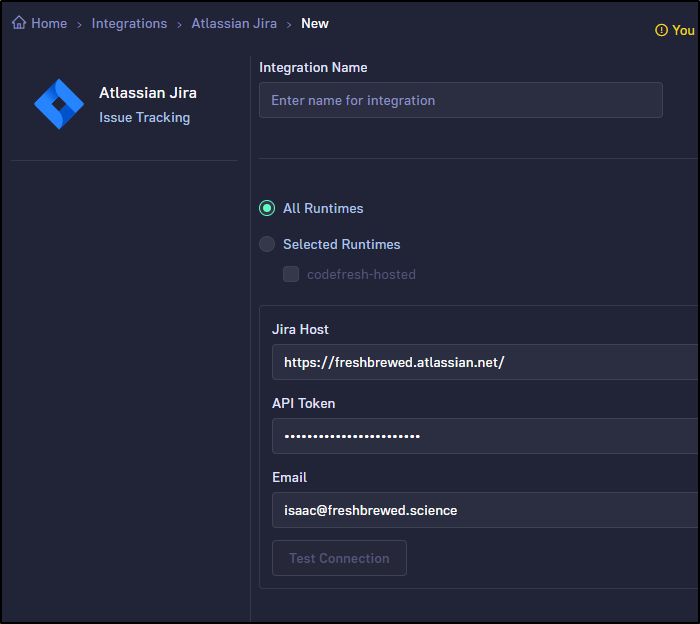
Let’s add a JIRA integration
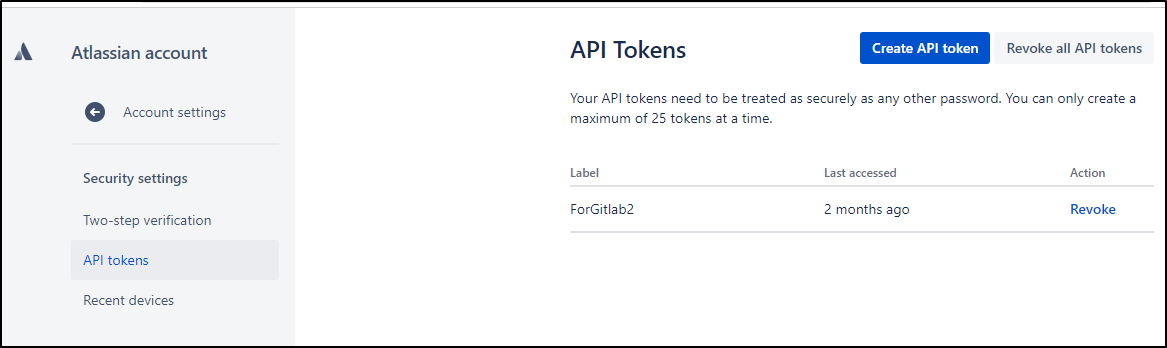
As mine is hosted, I’ll need to create an API token in the API Token section of user settings
We can then use it in the Integration settings
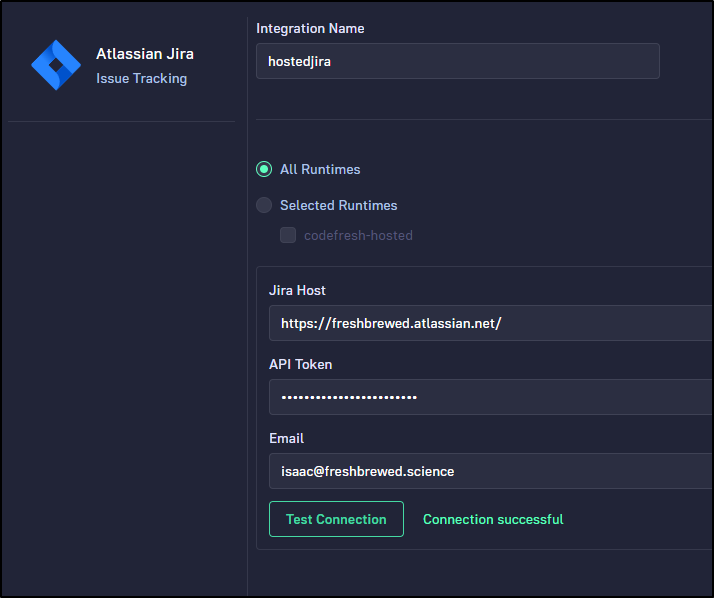
You can use Test Connection to see if the API token is valid and that Codefresh can connect
The UI took a few to realize I had a new Integration. At first I thought my settings were eaten. But it just was a delay between saving and seeing it reflected in the Integrations area
This integration really just applies to the Github Action and Codefresh CI pipeline, not Argo
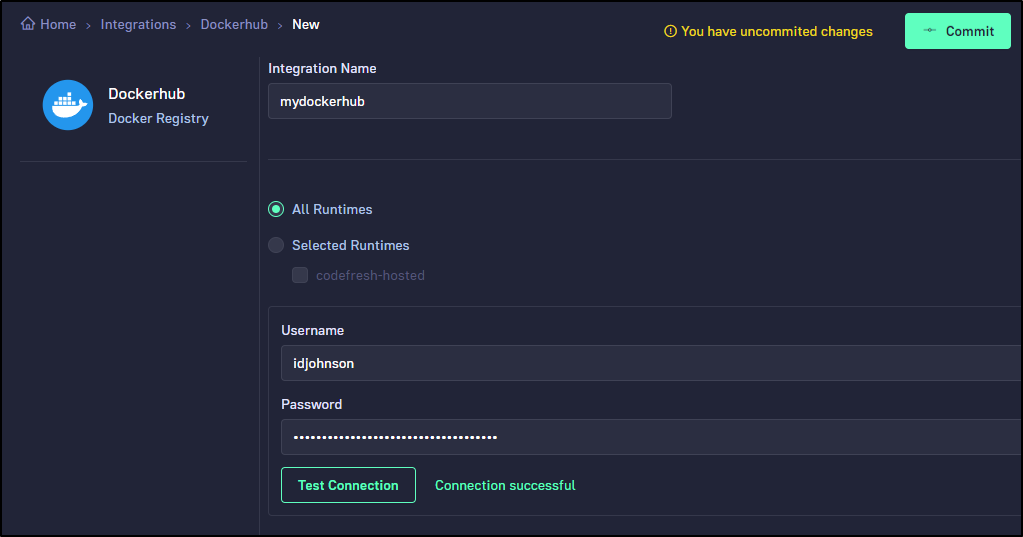
Dockerhub
Let’s also add Dockerhub
Like before, we enter a username and password (or token). We can Test Connection here as well
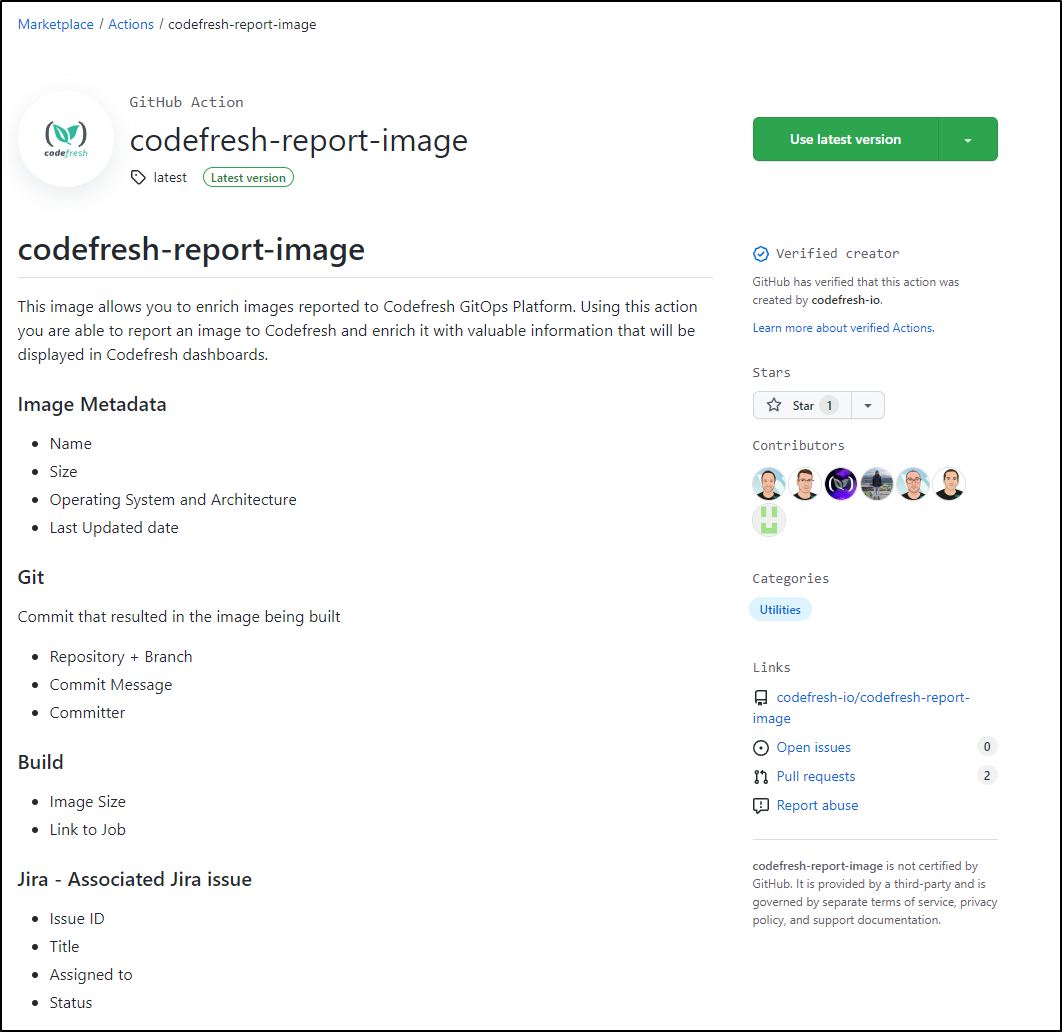
Codefresh Github Action
For instance, there is a codefresh-report-image Github action
Which can tie a Dockerhub image with JIRA and Codedfresh.
- name: report image by action
with:
CF_HOST: "https://my-runtime-url"
CF_API_KEY: $
#Codefresh Integrations to USE
CF_CONTAINER_REGISTRY_INTEGRATION: "dockerhub"
CF_JIRA_INTEGRATION: "jira"
CF_IMAGE: $/my-image-name:tag
CF_GITHUB_TOKEN: $
#Jira issues that match
CF_JIRA_MESSAGE: "CR-12293"
CF_JIRA_PROJECT_PREFIX: "CR"
uses: codefresh-io/codefresh-report-image@latest
From my examples above, that might easily look like:
- name: report image by action
with:
CF_HOST: "https://mr-62e3d9f588d8af3a8b8581d3-d6dd0e5.cf-cd.com"
CF_API_KEY: $
#Codefresh Integrations to USE
CF_CONTAINER_REGISTRY_INTEGRATION: "mydockerhub"
CF_JIRA_INTEGRATION: "hosted"
CF_IMAGE: idjohnson/my-image-name:tag
CF_GITHUB_TOKEN: $
#Jira issues that match
CF_JIRA_MESSAGE: "TPK-1234"
CF_JIRA_PROJECT_PREFIX: "TPK"
uses: codefresh-io/codefresh-report-image@latest
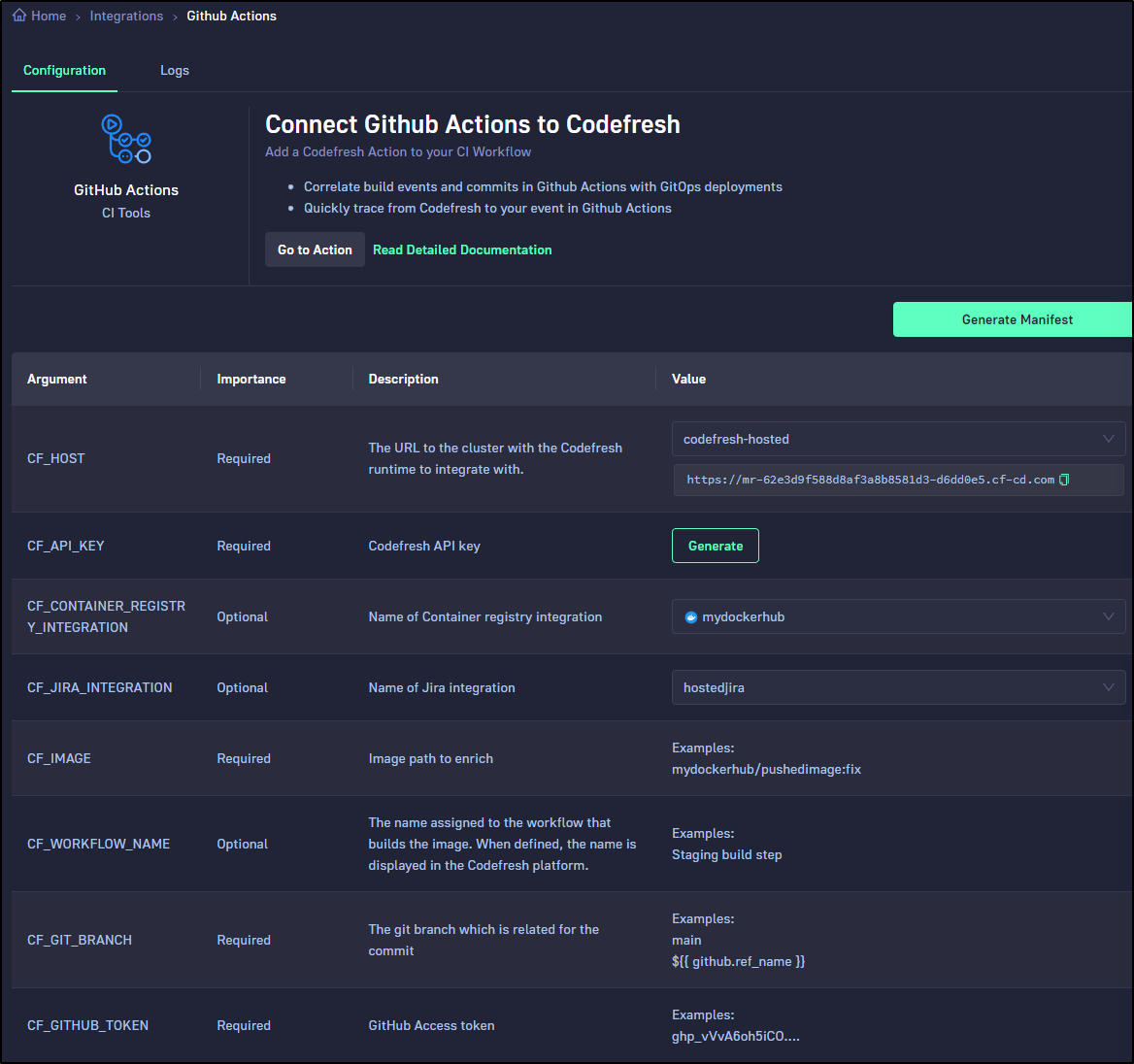
I can see the settings in the Github Actions Configuration page
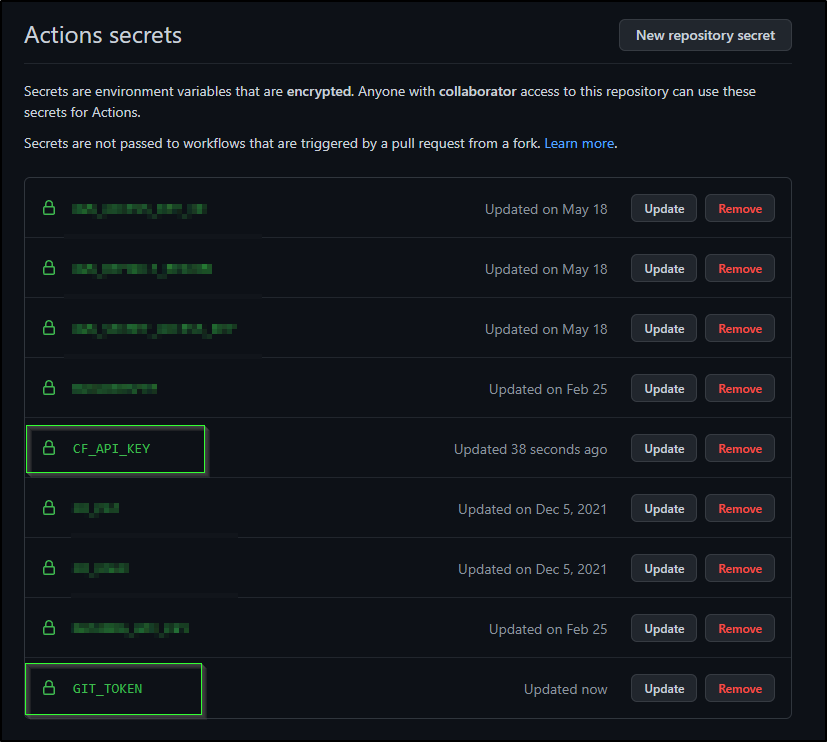
To use, I’ll add the secrets I don’t already have into my Github actions secrets area
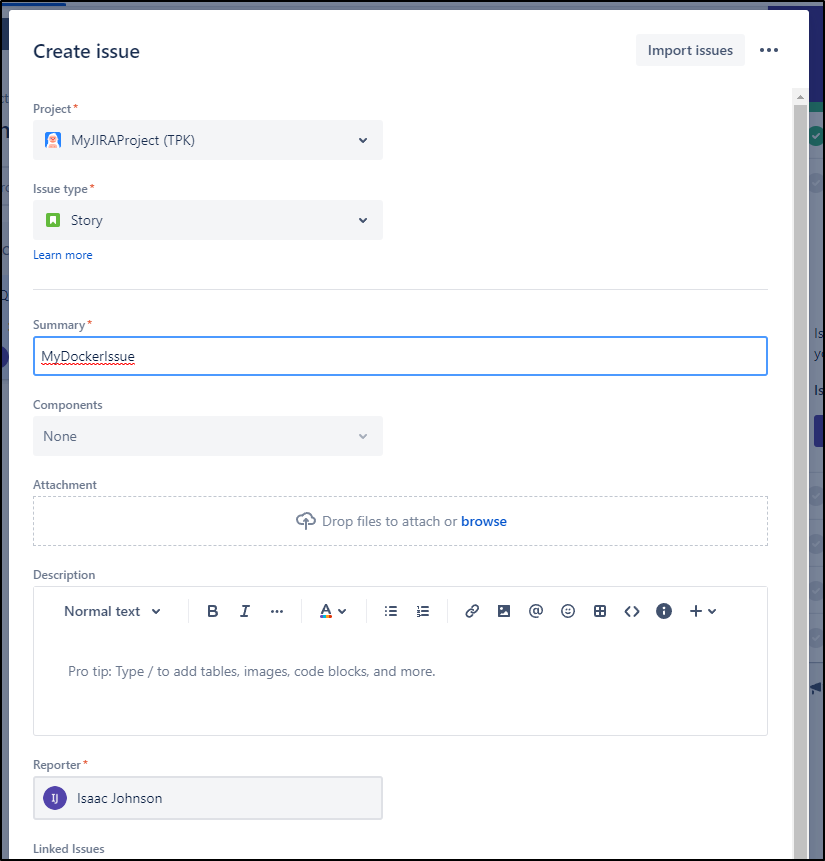
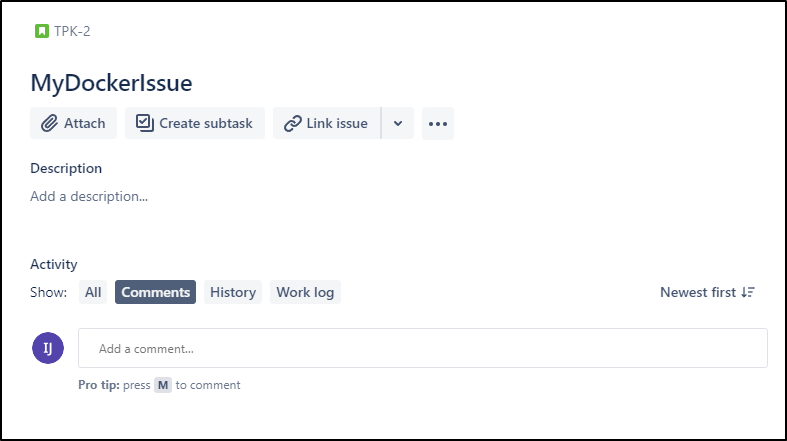
I also need to create a quick JIRA ticket to use for testing
which will be TPK-2
My Github Action now looks like (this does not match the image I’m building, ghrunner, but it’s just a test). The file itself is “testing-ghrunner.yml” so the modification should trigger the run.
name: GitHub Actions TEST
on:
push:
paths:
- "**/testing-ghrunner.yml"
jobs:
HostedActions:
runs-on: self-hosted
steps:
- name: report image by action
with:
CF_HOST: "https://mr-62e3d9f588d8af3a8b8581d3-d6dd0e5.cf-cd.com"
CF_API_KEY: $
#Codefresh Integrations to USE
CF_CONTAINER_REGISTRY_INTEGRATION: "mydockerhub"
CF_JIRA_INTEGRATION: "hostedjira"
CF_IMAGE: idjohnson/dockerwithtests2:latest
CF_GITHUB_TOKEN: $
#Jira issues that match
CF_JIRA_MESSAGE: "TPK-2"
CF_JIRA_PROJECT_PREFIX: "TPK"
uses: codefresh-io/codefresh-report-image@latest
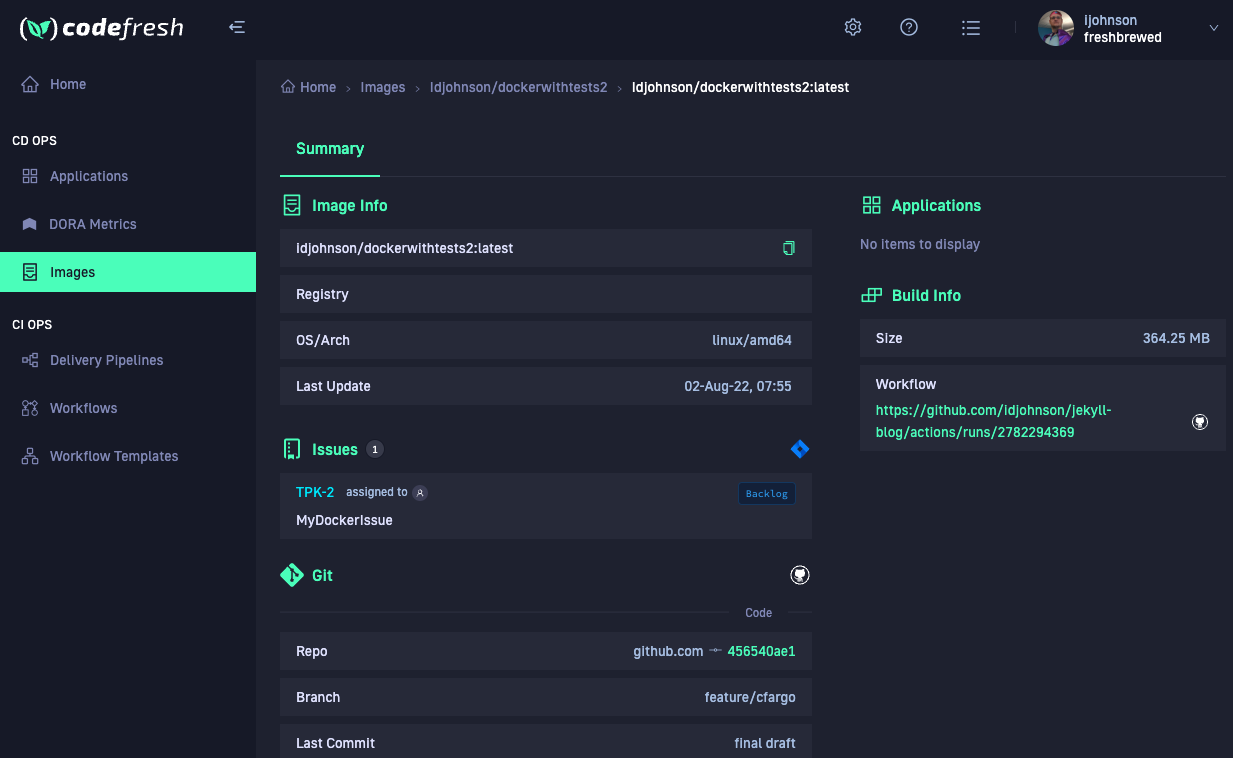
When completed, I did not see annotations or notes added in Github Pull Requests or SHAs. I saw nothing added in JIRA, however I do see information stored in Codefresh:
Pricing
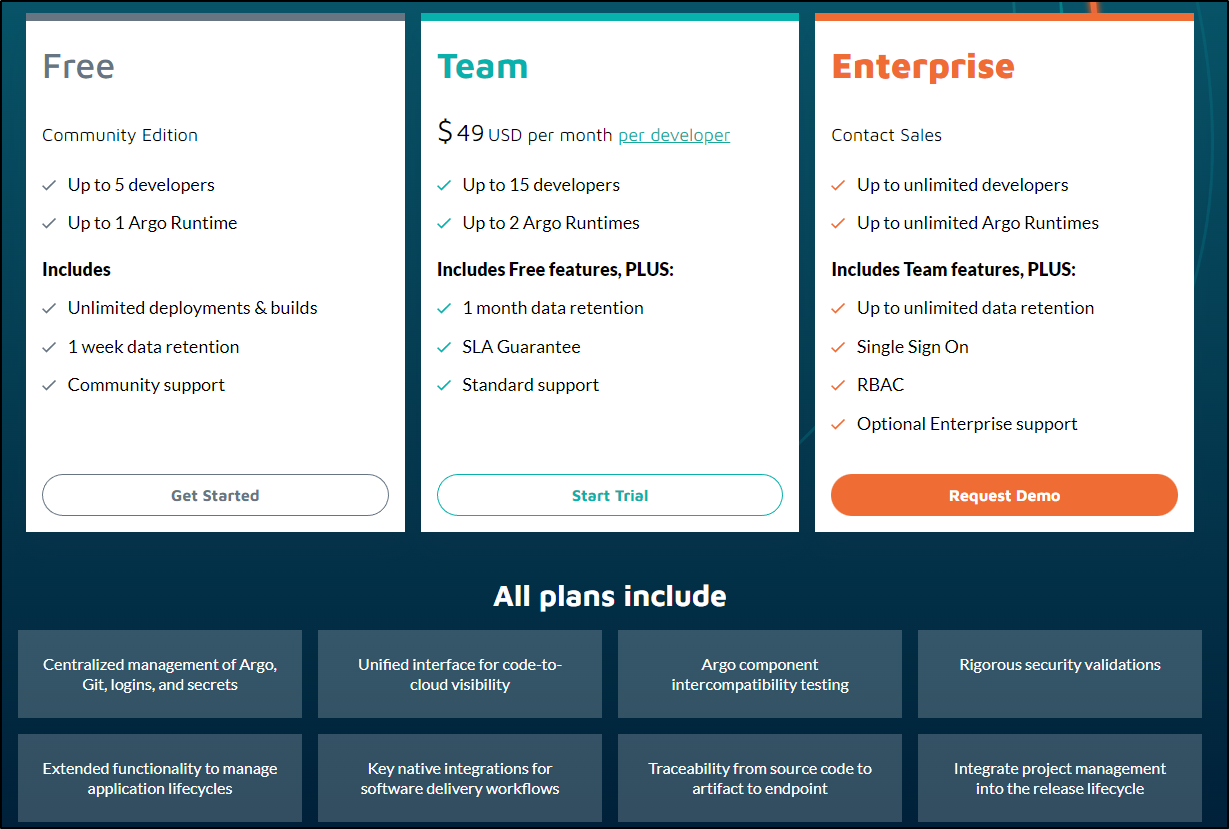
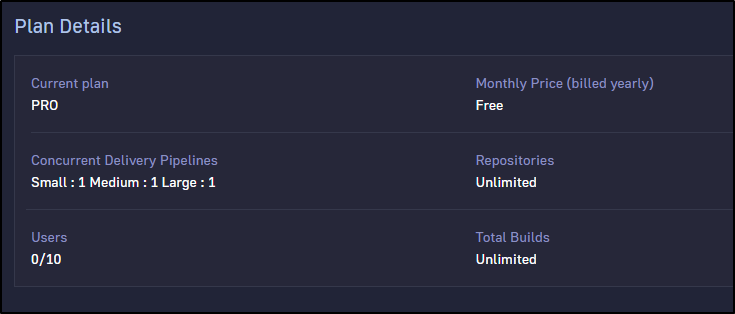
I do not see a way to upgrade in the UI, but I can see pricing on their pricing page
I cannot really see a reason one would move from the current 10 user 1 pipeline account to a Team at $50/user/mo that just adds a bit more retention and one more runtime. I hope they rethink their offering since the only other choice is “Enterprise” with that magic “Call Us” price that I never will do.
Summary
We have signed up and created a Codefresh ArgoCD Project from scratch. We onboarded two clsuters and launched two different variants of a Docker with Tests repo. We looked at Dashboards and Integrations and explored the free/open-source project offering.
Overall, I was quite impressed with all that we get. To date, I have used Koncrete.dev when I needed a quick Argo CD demo. However they have a light wrapper around ArgoCD and just allow one application and cluster. I am not complaining at all - free is free. However, this new CF offering offers way more at the free tier.
It’s pretty clear from the various sections of the tool that they want you to start with the free tier and be won over to try the rest of their commercial products. For instance, if you want to add more than 10 users or more than one concurrent pipeline, you need to use a Team or Enterprise account
I look forward to coming back and exploring their CI offering more.