Published: Feb 6, 2019 by Isaac Johnson
One can add other secrets engines. Secret engines are Vault’s extensibility model that allows a way to take data, do an action and return a result.
For instance, if one would like to dynamically provision service principals in Azure, one can add the Azure engine (providing they have sufficient privileges in Azure)
Note: The Azure secret engine is about creating service principals. Enabling Azure auth does not have anything to do with AKV
$ vault write azure/config \
> subscription_id= ******-**** - ****-**** - ********** \
> tenant_id= ******-**** - ****-**** - ********** \
> client_id= ******-**** - ****-**** - ********** \
> client_secret= *********************************
Success! Data written to: azure/config
$ vault write azure/roles/my-role ttl=1h max_ttl=24h azure_roles=-<<EOF
> [
> {
> "role_name": "Contributor",
> "scope": "/subscriptions/<uuid>/resourceGroups/Website"
> },
> {
> "role_id": "/subscriptions/<uuid>/providers/Microsoft.Authorization/roleDefinitions/<uuid>",
> "scope": "/subscriptions/<uuid>"
> },
> {
> "role_name": "This won't matter as it will be overwritten",
> "role_id": "/subscriptions/<uuid>/providers/Microsoft.Authorization/roleDefinitions/<uuid>",
> "scope": "/subscriptions/<uuid>/resourceGroups/Database"
> }
> ]
> EOF
Secrets Engines example: databases
A powerful use of Vault Engines is interacting with Databases.
For instance, during software validation, one may wish to dynamically create a temporary test user.
See a standard CI CD flow below.
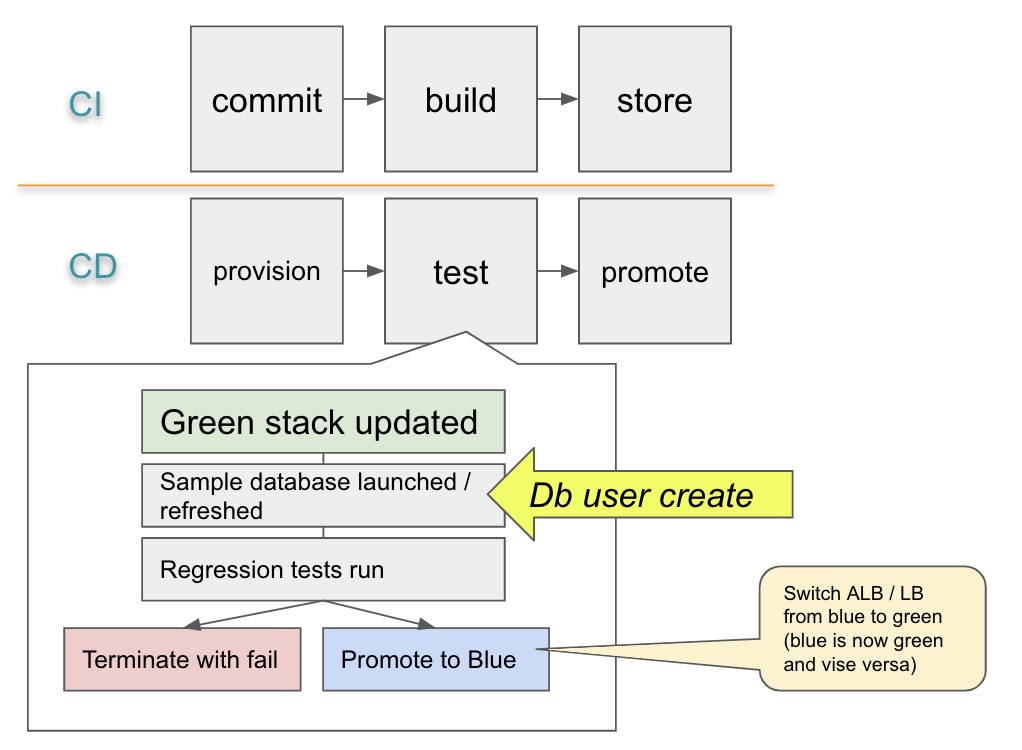
Example with MongoDB:
First one can create a MongoDB instance using the free bitnami image on Azure (“MongoDB Certified by Bitnami”)
Once launch, add an inbound rule for port 27017.
The database password is in the boot diagnostics log.
Create the database entry and role. Then you can use the “read” command to get a temporary user account
You can use Compass CLI, but I opted to download just the CLI. You can sanity check your connectivity this way.
#sanity check with CLI
$ ~/Downloads/mongodb-osx-x86_64-3.6.2/bin/mongo mongodb://137.117.104.120:27017
MongoDB shell version v3.6.2
connecting to: mongodb://137.117.104.120:27017
MongoDB server version: 4.0.3
WARNING: shell and server versions do not match
Welcome to the MongoDB shell.
$ vault write database/config/my-azure-mongodb \
plugin_name=mongodb-database-plugin \
allowed_roles="my-role" \
connection_url="mongodb://:@137.117.104.120:27017/admin" \
username="root" \
password="pvK9Xk9sz357"
$ vault write database/roles/my-role \
> db_name=my-azure-mongodb \
> creation_statements='{ "db": "admin", "roles": [{ "role": "readWrite" }, {"role": "read", "db": "foo"}] }' \
> default_ttl="2h" \
> max_ttl="24h"
Success! Data written to: database/roles/my-role
$ vault read database/creds/my-role
Key Value
--- -----
lease_id database/creds/my-role/zquLtoyl8Mk6SvLyZoQeJFpH
lease_duration 2h
lease_renewable true
password A1a-U5JzyT5YBRHprZrF
username v-token-my-role-2Ph0kxLfI2gAE634ElHu-1546356485


